What do bank account takeovers, credit card scams, purchase of counterfeit goods, and frequent flier mile theft, all have in common? All these cyber crimes usually begin with a user visiting a fake website.
In the first quarter of 2024, over 963,000 unique phishing sites were detected worldwide. Phishing sites are just one category of fake websites that mimic legitimate sites to steal information. The overall scope of fake websites is likely much broader.
Interacting with fake websites can have severe impacts, including data theft, customer mistrust, and financial losses. Before we look at some fresh examples of fake websites in the wild, let’s look at the types of fake websites and what you can do to protect your clients from them.
What Is a Fake Website and How Does It Work?
Fake websites are malicious clones of real ones, built to mislead users into handing over credentials, personal data, or money. Most fake sites rely on website spoofing – the act of mimicking a legitimate brand site’s design, URL, and functionality-to gain users’ trust.
Once a user lands on a spoofed site, attackers can:
- Steal credentials via phishing logins
- Harvest credit card details or PII
- Install malware
- Spread misinformation
They’re deployed at speed and scale, often using paid ads, SEO poisoning, social engineering, or SMS phishing to reach victims. Common targets include banking, e-commerce, streaming, airlines, and package delivery services.
Common Types of Fake Websites
Fake websites are used to execute a range of scams. Below are some of the most frequently observed patterns across industries:
E-commerce scams
Attackers create fake online stores that closely mimic legitimate brands — often replicating logos, product listings, and promotional language. Victims may receive counterfeit goods, nothing at all, or unknowingly share payment data.
Account takeover setups
Spoofed login pages for services like banking, travel, and education are used to harvest credentials. Once obtained, these are used for account takeover or may be resold access on underground markets.
Investment fraud
Scam sites impersonate financial platforms, including brokerages and crypto apps, to trick users into transferring funds. They often promise high returns to accelerate decision-making.
Gift card scams
Fake sites sell invalid, already-used, or counterfeit gift cards. Attackers may also use these sites to collect payment information for further fraud.
Misinformation and fake news
In the US, there are more fake news websites than real local media websites. These websites are incredibly dangerous because they purposely distort public opinion based on lies, sway people to change their values and beliefs, defend (often extremist) causes, or even endanger readers’ health based on incorrect and unfounded healthcare information.
How Can You Spot a Fake Website?
Here are some key signs a website may be fake:
- Suspicious URLs (typos, extra words, misspelled brand names)
- No HTTPS or invalid SSL certificates
- Urgent language or popups pressuring action
- Requests for sensitive info outside of known login flows
- Linked from untrusted sources like random emails or texts
If your brand’s customers are being lured to fake sites, the damage isn’t just technical-it’s reputational and financial.
5 Real-World Fake Website Examples and the Tactics Behind Them
As these examples show, fake websites succeed not because users are careless but because attackers are adept at imitating brand trust signals. Spotting a fake often comes down to subtle inconsistencies in domains, content, or context. For security teams, this makes it all the more important to combine user awareness with browser-level detection.
1. PayPal Phishing Clones
In late 2023, attackers launched spoofed PayPal login pages using lookalike domains like paypa1.com and paypaysecurity.com. Victims were tricked by phishing emails claiming account issues and prompted to “log in.” The cloned pages looked nearly identical to PayPal’s, enabling attackers to steal credentials and drain accounts. These scams often rely on deceptive URLs and urgent account-related messages to lure users.
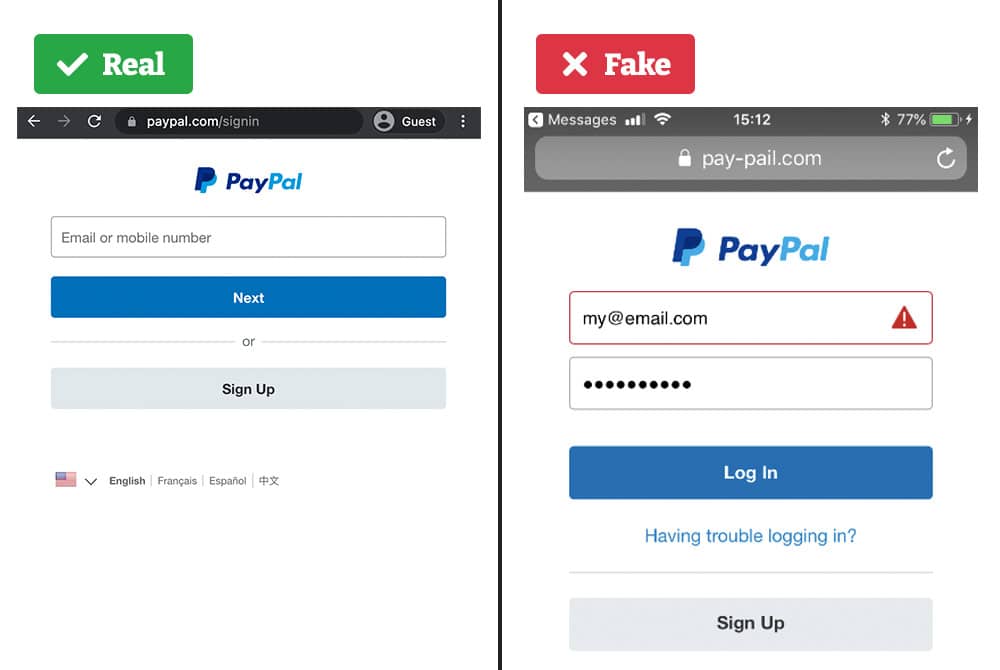
2. Apple Support Scams
Fake Apple support websites used SEO poisoning to hijack search results for phrases like “iPhone not charging.” Frustrated users landed on spoofed support pages and were tricked into calling fake phone numbers. From there, attackers upsold fake services or harvested payment info. This tactic highlights how attackers exploit SEO to misdirect users searching for trusted support content.
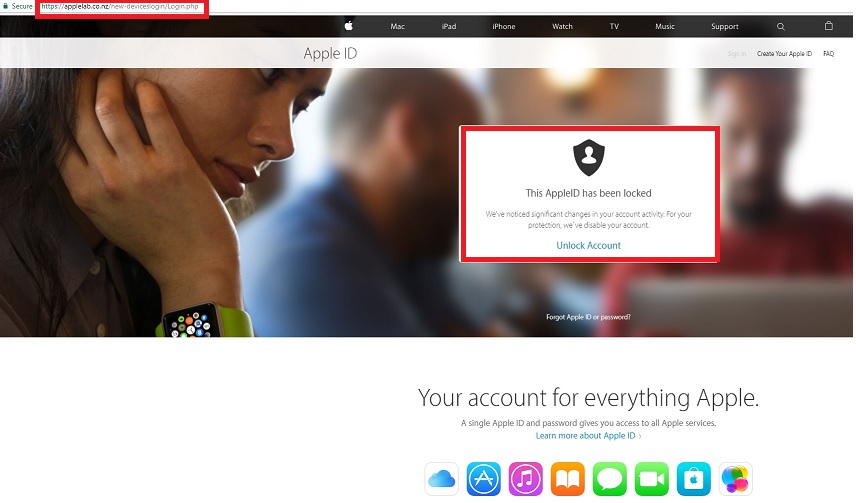
3. Netflix Subscription Alerts
In a 2023 campaign, fake Netflix sites mimicked the brand’s login interface and told users their accounts would be suspended due to billing errors. Victims submitted their details, which were used for both ATOs and credit card fraud. Users lost $2,270 on average. The company had to reset the passwords of all affected users, send out warnings, and strengthen its security measures to allow earlier and easier fraud detection.
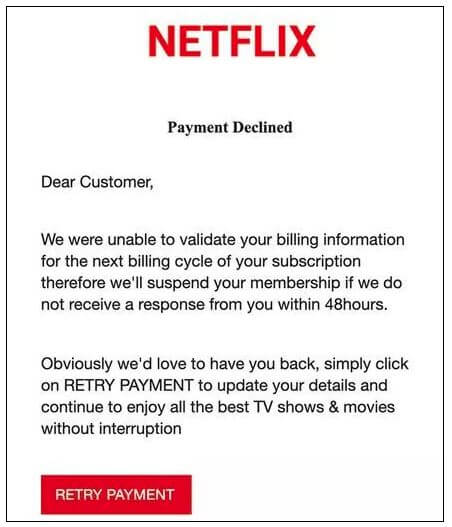
4. ChatGPT Download Scams
As ChatGPT gained popularity, attackers registered domains like chat-gpt-ai-pc.info to trick users into downloading fake tools. Instead, victims received malware or ransomware. Some fake ChatGPT sites also requested payment details to unlock premium features that didn’t exist. Phishing campaigns increasingly piggybacked on viral technologies like generative AI to boost credibility. In Q4 2024 alone, nearly 1 million phishing attacks were recorded globally, according to APWG, reversing the mid-year dip.
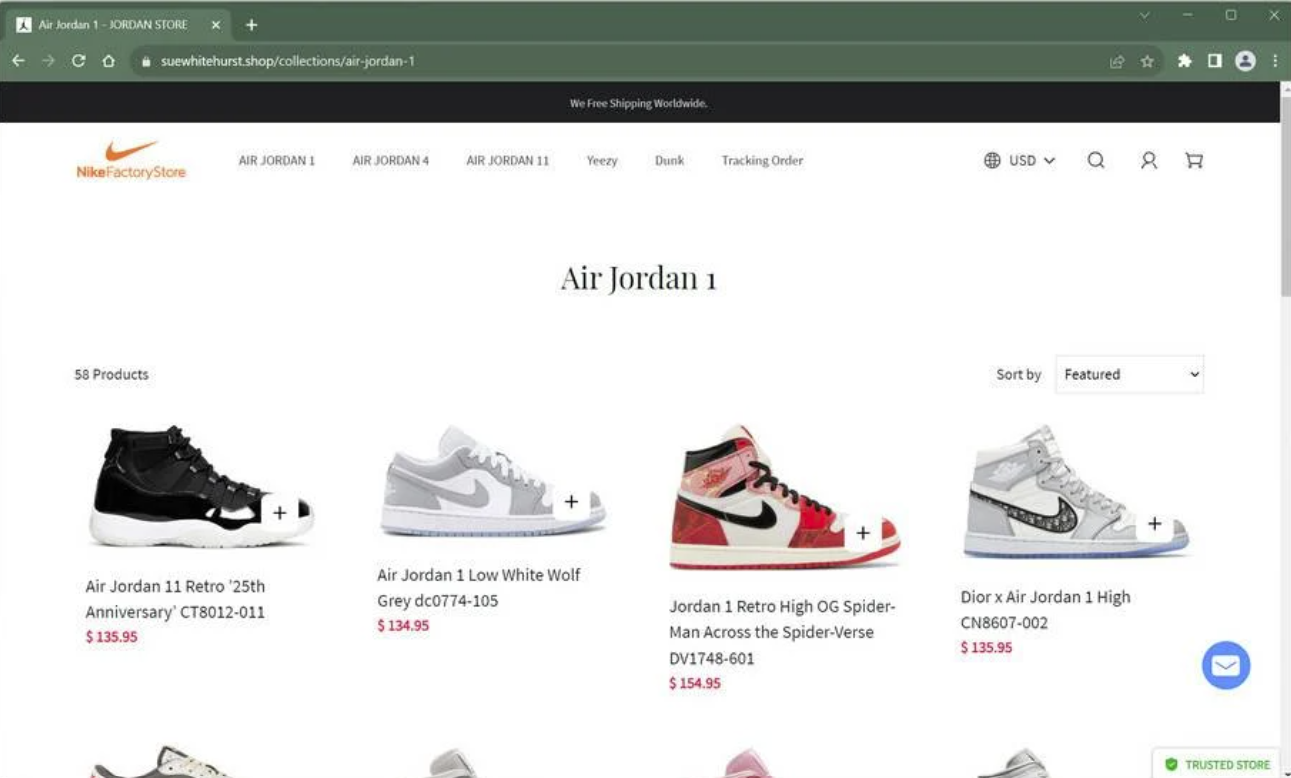
5. Nike World Cup Sale Hoax
During the 2023 FIFA World Cup, fake Nike sites flooded social media and search engines with limited-time discounts on Air Jordans. These scams used lookalike URLs and identical site designs. Victims either received counterfeits or nothing at all-and Nike had to deploy public takedown campaigns. These fake stores preyed on event-driven hype and aggressive discounting to pressure users into impulse purchases.
What Are the Risks of Fake Websites for Brands and Users?
In 2024, phishing scams more than doubled, and scammers increasingly used AI-generated content to create convincing fake sites. Reports show a sharp spike in domains spoofing major brands, especially during high-traffic seasons and crises. According to InfoSecurity Magazine, phishing activity surged over 200% last year—posing a serious threat to both users and brands.
Risk of fake websites for brands:
- Revenue loss: Customers are diverted to lookalike sites and make payments to attackers.
- Reputation damage: Victims often blame the real brand.
- Support overload: Fraud claims flood call centers.
- Compliance risk: Regulatory exposure grows when customers’ PII is mishandled.
Risk of fake websites for users:
- Financial fraud: From stolen credit cards to fake purchases.
- Account takeovers: Phishing logins often lead to downstream ATO.
PII theft: Data is resold or used in future fraud. - Emotional toll: Victims feel betrayed by brands they thought they could trust.
How Memcyco Helps Stop Fake Websites in Real Time
Fighting fake websites isn’t about being fast, it’s about being first. By the time a takedown team moves, attackers have already phished victims, stolen credentials, or deployed malware.
Memcyco predicts & preempts ATO, phishing and digital impersonation attacks in real time, protecting companies and their customers from digital fraud.
Memcyco stands apart as the only solution that:
- Identifies individual attack victims in real time
- Predicts, preempts & protects from ATO incidents before they cause any harm
- Replaces harvested credentials with decoy data, rendering them useless to attackers
- Disarms SEO poisoning attempts that undermine digital presence
- Tricks threat actors with deception campaigns, proactively bombarding fake sites with decoy credentials
Memcyco infiltrates the attack, enabling unmatched real-time visibility into its progress from inception and as it evolves, safeguarding revenue, reputation, and user accounts. In addition to rapidly reducing costs, Memcyco supports compliance readiness amid fast-changing regulatory standards.
With agentless deployment, Memcyco’s solution delivers immediate ROI by cutting fraud-related losses and operational burdens, all while strengthening digital trust.
Frequently Asked Questions About Fake Websites
How do I know if a website is safe?
Start by checking the URL – it should exactly match the brand’s official domain and use HTTPS. Look for other trust signals like no aggressive pop-ups, a professional layout, and contact info that matches what you’d expect. When in doubt, search for the site or access it via an official app.
What happens if you visit a fake website?
You could unknowingly give away personal data, login credentials, or payment info. Some fake websites also install malware or enable account takeovers, even if you don’t click anything.
Are there fake .gov websites?
Yes, though rare, attackers sometimes spoof government sites using lookalike domains like .gov.co or character swaps. Always verify through official directories or search engines before trusting the page.
How to check if a website is correct?
Compare the URL to the official domain, look at the SSL certificate details (click the lock icon), and avoid using links sent via email or SMS. If you’re unsure, type the site into a search engine instead of clicking.
How to identify a fake URL?
Fake URLs often include misspellings, extra dashes or numbers, or odd subdomains. They’re designed to look close to the real thing at a glance – inspect carefully for anything unusual.
Does HTTPS mean a website is safe?
No. HTTPS only means the connection is encrypted. It doesn’t confirm the site is legitimate. Many fake websites use HTTPS to appear credible, so always check the domain name and context.



















