Many enterprises turn to the DMCA takedown process when they discover infringing or fraudulent content online. While DMCA takedown serves as a protective mechanism for copyrighted material, it was never designed to address the speed and scale of brand impersonation and phishing scams. To put things into context, it takes less than 60 seconds for users to fall for phishing emails. That’s 21 seconds to click, plus 28 seconds to enter their data on a phishing site, according to Verizon’s 2024 Data Breach Investigations Report. This gap leaves businesses compromised, leveraging a reactive approach that can’t keep up with the sheer agility and scale of scammer operations.
To confront it head-on, we’ll show how to file a DMCA takedown notice effectively, while highlighting tactics for resolving its shortfalls in aggressive brand impersonation, phishing and account takeover (ATO) scenarios.
What is a DMCA takedown?
A DMCA takedown is a formal legal request to remove online content that infringes copyrighted material. It applies to text, media, and code, and requires platforms or hosts to remove the infringing content once a valid notice is received.
In practice, the DMCA process works well for disputes over:
- Republished articles or blog posts.
- Unauthorized use of images, video, or audio.
- Copying website code or layouts.
For enterprises, it’s often used when competitors or malicious actors copy digital assets wholesale. It sits alongside other enforcement mechanisms such as trademark complaints (for logos and branding) or domain disputes (UDRP filings for hijacked domains).
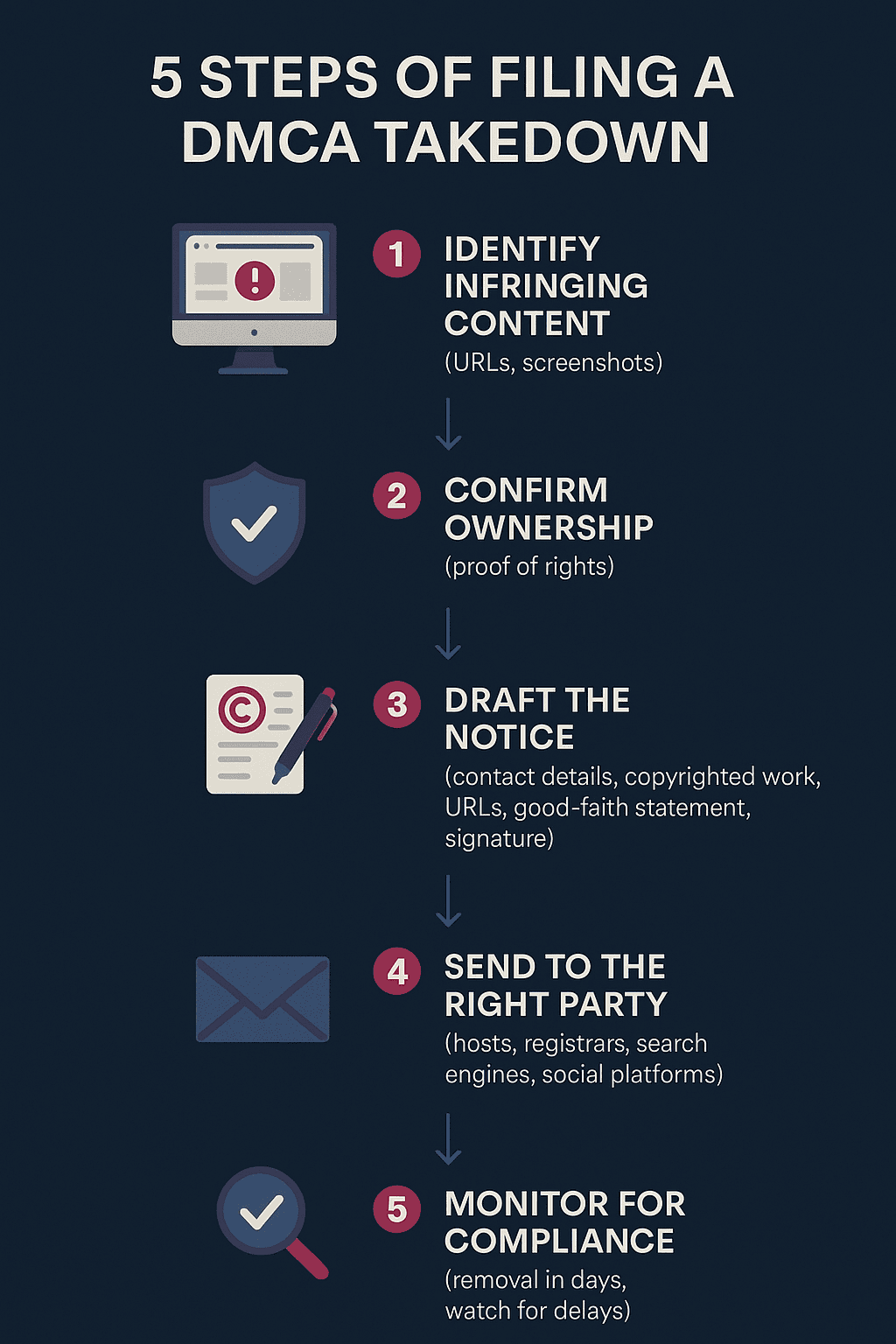
Steps to File a DMCA Takedown Notice
Here’s how the process usually works.
1. Identify the infringing content
Collect URLs, screenshots, and context. The more precise the evidence, the stronger your case. One challenge: phishing sites often rotate domains or obfuscate hosting details to make them harder to trace.
2. Confirm ownership
You must prove you own or control rights to the original content. For example, authorship, registration, or copyright documentation. Without this, the notice risks rejection.
3. Draft the DMCA takedown notice
A DMCA takedown notice must include:
- Your contact details.
- A description of the original copyrighted work.
- The URLs of the infringing content.
- A statement of good-faith belief that infringement occurred.
- Your signature (physical or digital).
4. Submit the notice to the appropriate party
Notices can be sent to:
- Hosting providers (the servers where the content lives).
- Registrars (who issued the domain).
- Search engines (Google will de-index infringing pages).
- Social platforms (if the content appears in ads or profiles).
5. Monitor for compliance
Once the notice is accepted, the content is usually removed within a few business days. Be aware that some hosts are less responsive, and bad actors can file counter-notices to delay takedown.
How long does it take?
Even under the best conditions, a DMCA takedown takes days. In fraud terms, that’s a lifetime. Phishing sites can harvest hundreds of victims within hours of going live.
Related: Automated Brand Impersonation Protection: How It Works
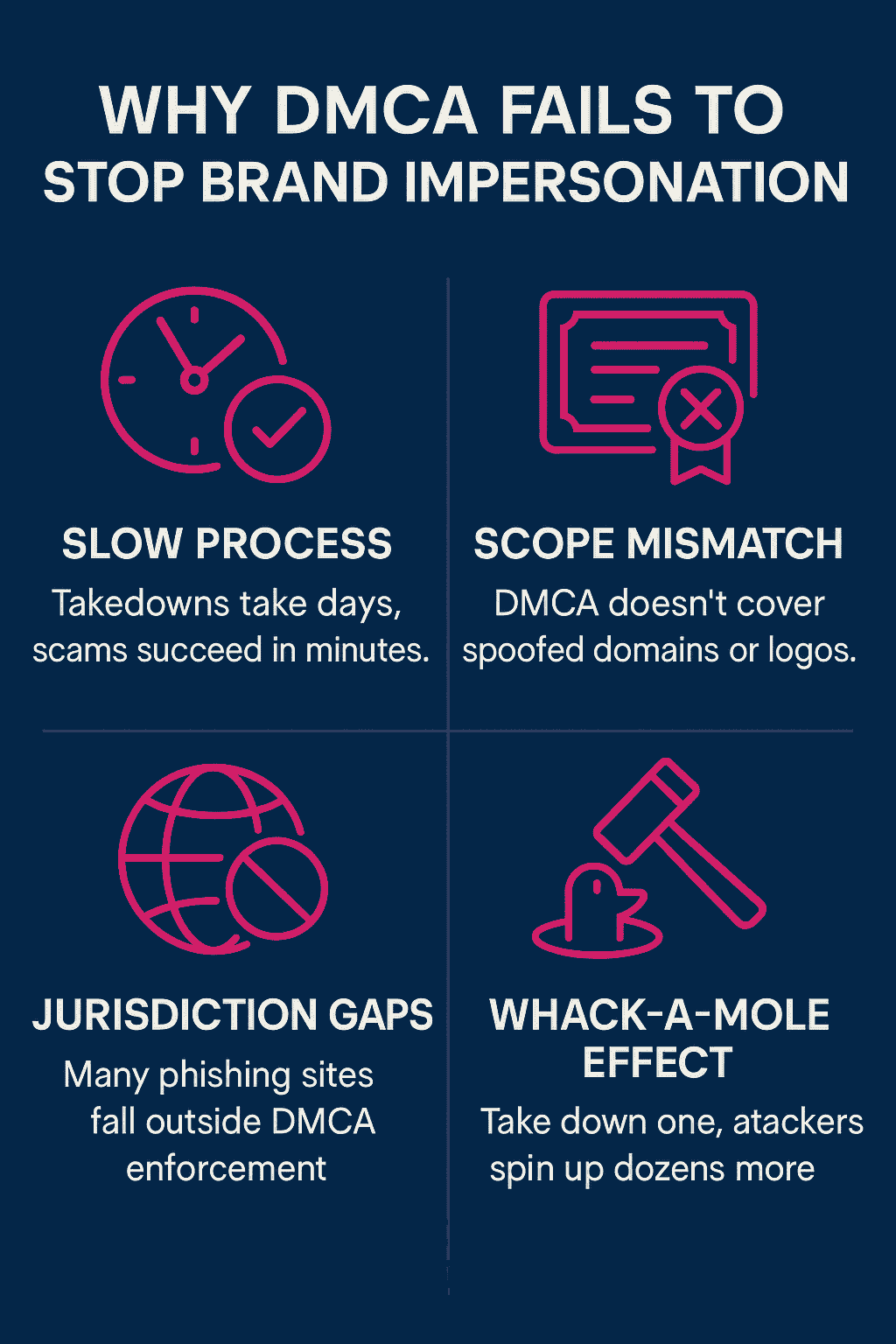
Limitations of DMCA for Brand Protection
While valuable for copyright disputes, DMCA notices were never intended to combat phishing or brand impersonation fraud. Their weaknesses include:
- Slow process: Legal removal takes days, while fake websites steal credentials in minutes.
- Scope mismatch: DMCA covers copyrighted material, not lookalike domains or spoofed logos.
- Jurisdiction gaps: Many phishing sites are hosted in countries that don’t recognize DMCA law.
- Whack-a-mole effect: Even if one site is removed, attackers spin up dozens more with automated kits.
The “Whack-a-mole” effect in practice
One of the most frustrating realities for security teams is the speed at which fake websites reappear. Attackers now rely on automated phishing kits that can replicate a legitimate site in minutes. Even if a DMCA notice succeeds, the same kit can be redeployed under a new domain before the original takedown is processed. Security teams end up chasing domains endlessly, while customers remain exposed to near-identical spoofs across multiple URLs. This constant regeneration means takedowns solve symptoms, not the problem.
Consider a fake banking site cloned in under an hour. By the time a DMCA request reaches the host, the fraud campaign has already succeeded. The brand is left to clean up after the fact.
Critical Limitations of DMCA Takedowns for Phishing & Brand Impersonation Scams
Modern phishing campaigns outpace reactive takedown mechanisms not only in speed but also in operational tempo. Attackers iterate faster than enforcement can respond, creating a structural disadvantage for defenders.
How attackers operate
- Use automated phishing kits to clone brand assets instantly.
- Provision lookalike domains on demand.
- Drive victims via email, compromised ad networks, or SEO poisoning.
- Harvest credentials and payment data within minutes.
- Exfiltrate and monetize data immediately for ATO or resale.
A Scenario Example
Imagine this scenario: during a critical sales event, threat actors deployed hundreds of ephemeral spoofed domains. Even with fast detection, the process of verifying infringement, drafting a DMCA notice, and awaiting registrar or host action spanned several days. By then, attackers had already achieved their objective: mass credential harvesting and data exfiltration. Thousands of customer accounts and card numbers were compromised, and brand trust was severely damaged.
Why DMCA Takedown Is the Wrong Tool for Phishing Sites
Takedown requests are by definition post-factum, relying on detection, often via customer reports, and then move through a multi-stage legal workflow. While useful for cleanup, they cannot prevent the initial compromise. DMCA and domain takedowns remain reactive tools for IP infringement, not proactive defenses against agile, real-time fraud and impersonation.
Related: What Domain Takedown Services Miss & How to Close Gaps
A Proactive Alternative: Real-Time Brand Impersonation Protection
Instead of relying on slow, legalistic processes, enterprises can now defend against brand impersonation in real time. Memcyco provides automated brand impersonation protection that detects the earliest indicators of impersonation threats as their happening, such as website code reconnaissance and dev-tool usage on your genuine website.
Key features include:
- Cloning detection: Flags early-stage cloning behaviors, such as dev-tool-based inspection and spoofed domain setup. Memcyco detects structural replication and impersonation attempts as they go live, cutting off attacker engagement before users are exposed.
- Decoy credential injection: Auto-swaps real login data with decoys, rendering stolen credentials useless. When attackers replay them, they trigger alerts and lockouts, exposing the threat and destroying ROI.
- Red Alerts on spoofed sites: Customers see visible warnings when they land on spoofed domains, stopping engagement before harm occurs and breaking the scam funnel.
- Suspicious device blocking: Prevents access from devices linked to fraud, even if credentials are correct. Reused stolen data hits a wall.
- SEO poisoning defense: Detects and suppresses scam sites hijacking your brand in search results, reducing visibility and clickthrough.
- Victim and attacker infrastructure visibility: Surfaces the identities of targeted users and the tools used against them in real time, enabling faster, focused response.
Related: Phishing Site Detection & Takedown: What to Look For
Note: These features focus on web impersonation. For mobile spoofing and fake app detection, Memcyco provides separate daily monitoring and takedown workflows.
Automated Takedown Initiation
Memcyco’s real-time digital impersonation protection also automates the initiation of takedown requests against detected phishing and spoofed domains, coordinating in-house workflows and evidence packaging to fast-track removal. Instead of waiting for teams to draft and file notices, Memcyco triggers the process automatically and leverages SLA-backed takedown procedures, accelerating cleanup while defenses are already blocking attacks in session. This dual approach, real-time disruption plus automated takedown initiation, ensures brands are protected during the attack and cleaned up faster afterward.
Why this Matters for Different Teams
- SOC teams: Gain actionable alerts and seamless SIEM integration.
- Fraud teams: Enrich fraud risk engines with high-fidelity impersonation signals.
- Digital business teams: Protect customer trust with no added login friction.
This approach flips the model from after-the-fact takedown to in-session defense plus automated cleanup.
Make the switch from Reactive to Proactive Brand Impersonation Defense
In short, DMCA takedowns still have a place in long-term IP enforcement. But when the threat is brand impersonation, fake websites, and phishing-related fraud, the stakes are different. Speed is everything.
Get a Memcyco product demo and discover why global enterprises are switching to real-time defenses that permanently take the sting out of stubborn brand impersonation scams that drain revenue and reputation.
Related reading:
- How to Choose the Best Domain Takedown Service
- How to Replace Outdated Phishing Protection With Real-Time Defense
- How to Detect & Stop Fake Mobile Apps Before Account Takeover
FAQs About DMCA Takedowns
What is a DMCA takedown notice?
A legal request under the Digital Millennium Copyright Act requiring platforms or hosts to remove infringing content.
How long does a DMCA takedown take?
Typically a few business days. Against fast-moving phishing campaigns, this delay makes it ineffective.
Does a DMCA takedown stop phishing websites?
No. DMCA addresses copyright infringement, not fraud. Phishing sites can compromise victims long before takedowns occur.
What’s the difference between a DMCA takedown and brand impersonation protection?
DMCA removes infringing content after a report. Brand impersonation protection detects and blocks fake websites in real time, preventing customer harm, while also automating takedown initiation for faster removal.
Can attackers return after a DMCA takedown?
Yes. Fraudsters often launch multiple lookalike domains. Without proactive defenses, new spoofed sites can appear as fast as old ones are removed.
Is DMCA enough to protect a brand from impersonation scams?
No. DMCA is designed for copyright protection, not fraud prevention. To defend against phishing and impersonation, enterprises need tools that act in real time and automate removal.



















