Evil Twin attack prevention has become more difficult than ever. With affordable, easy-to-use tools, these attacks are now more accessible and harder to detect, leaving customers vulnerable to sophisticated account takeovers without the usual phishing hallmarks.
Tools like the Wi-Fi Pineapple Mark VII ($299) create rogue networks and phishing portals, while the ESP8266 Deauther V4 ($15) disrupts Wi-Fi handshakes to force devices onto less secure networks. Aircrack-ng 5.0, enhanced with quantum-optimized algorithms, cracks WPA3 passwords in under 12 hours, exploiting both legitimate and rogue networks.
These low-cost tools make it easier for attackers to carry out real-time phishing schemes, stealing credentials and compromising accounts. Despite the growing sophistication of these tools, businesses still rely on user vigilance when connecting to public Wi-Fi—a reliance that has expanded the external attack surface.
To effectively mitigate Wi-Fi-based threats, businesses must adopt proactive, real-time defenses that neutralize phishing attempts before credentials are exposed.
What is an Evil Twin Attack?
How Attackers Set the Trap
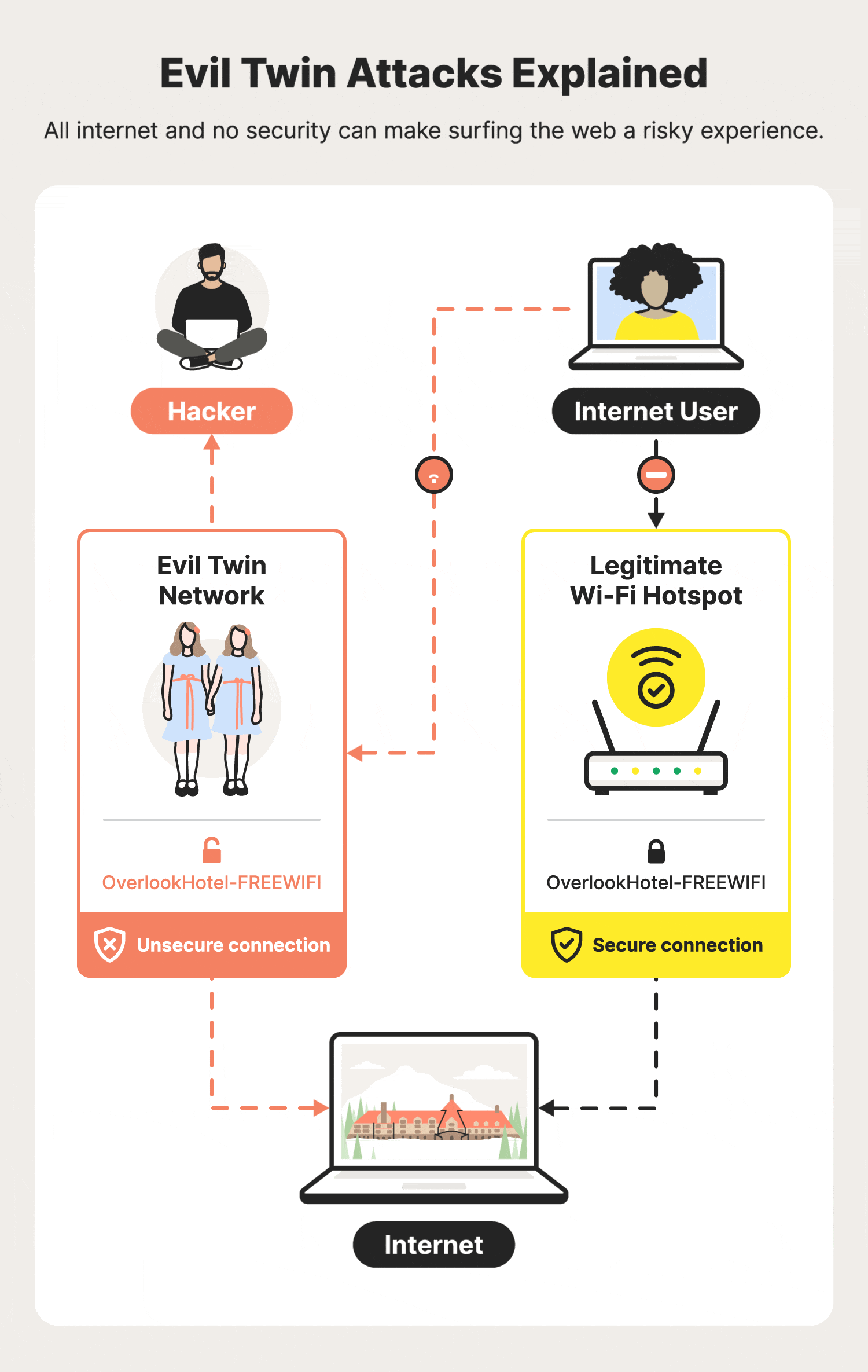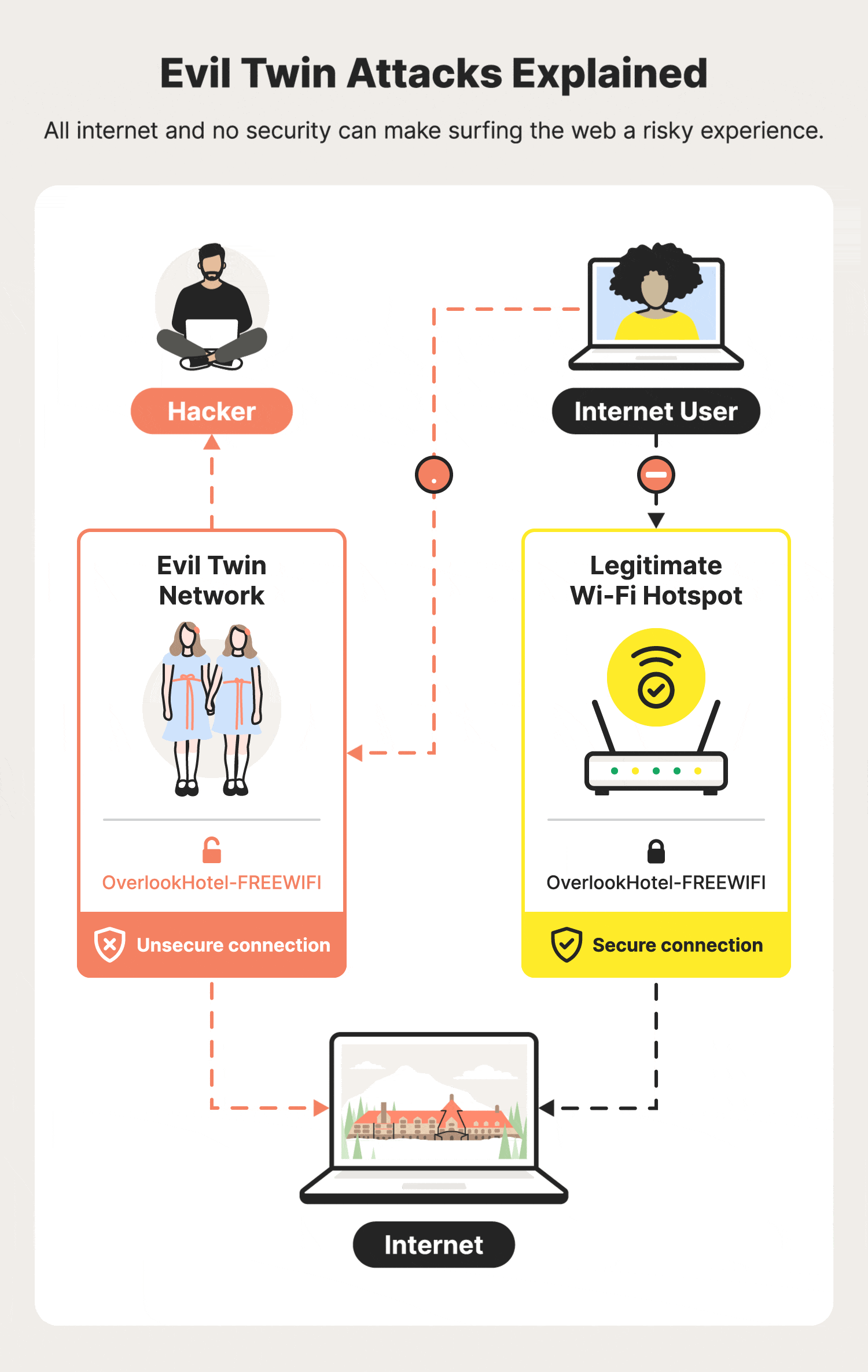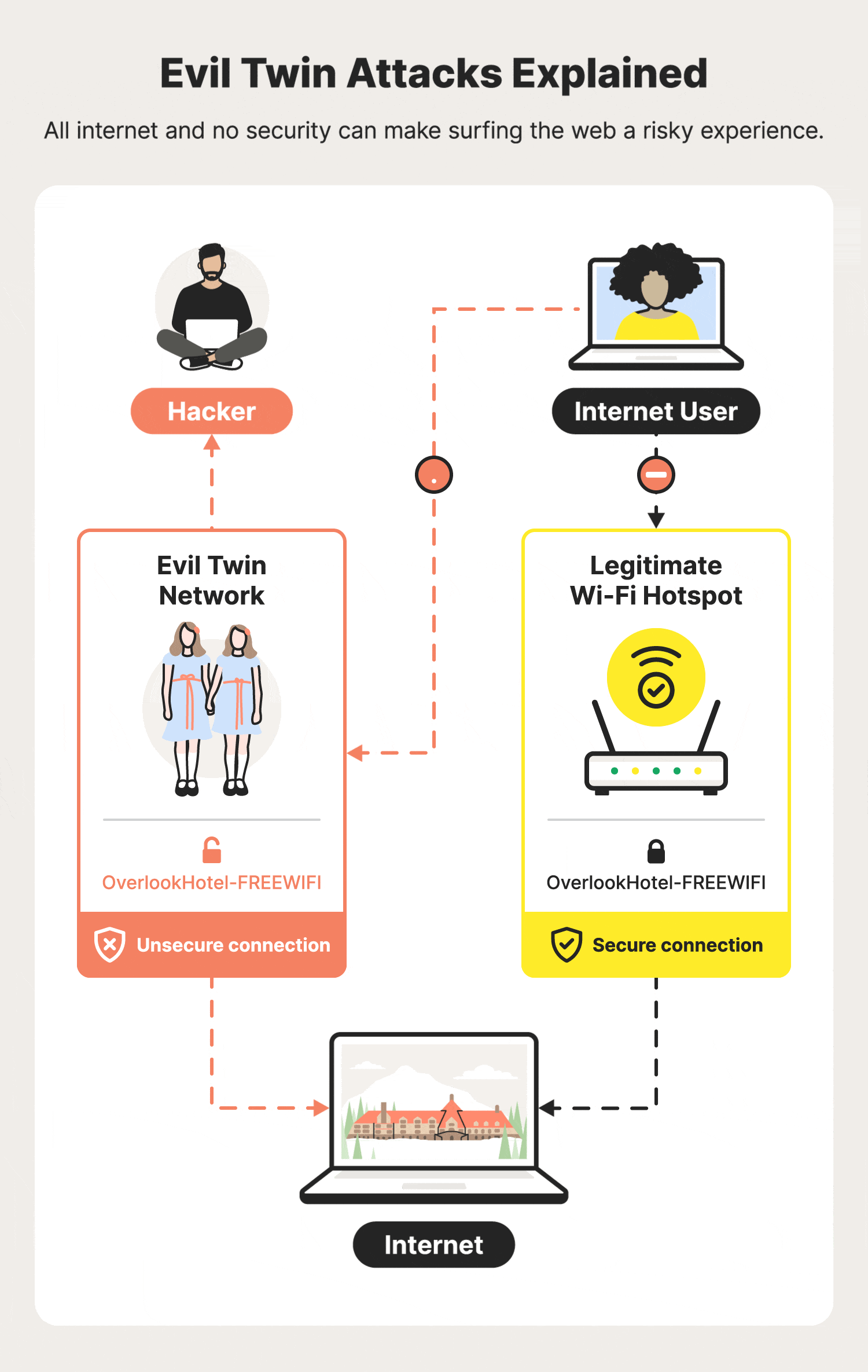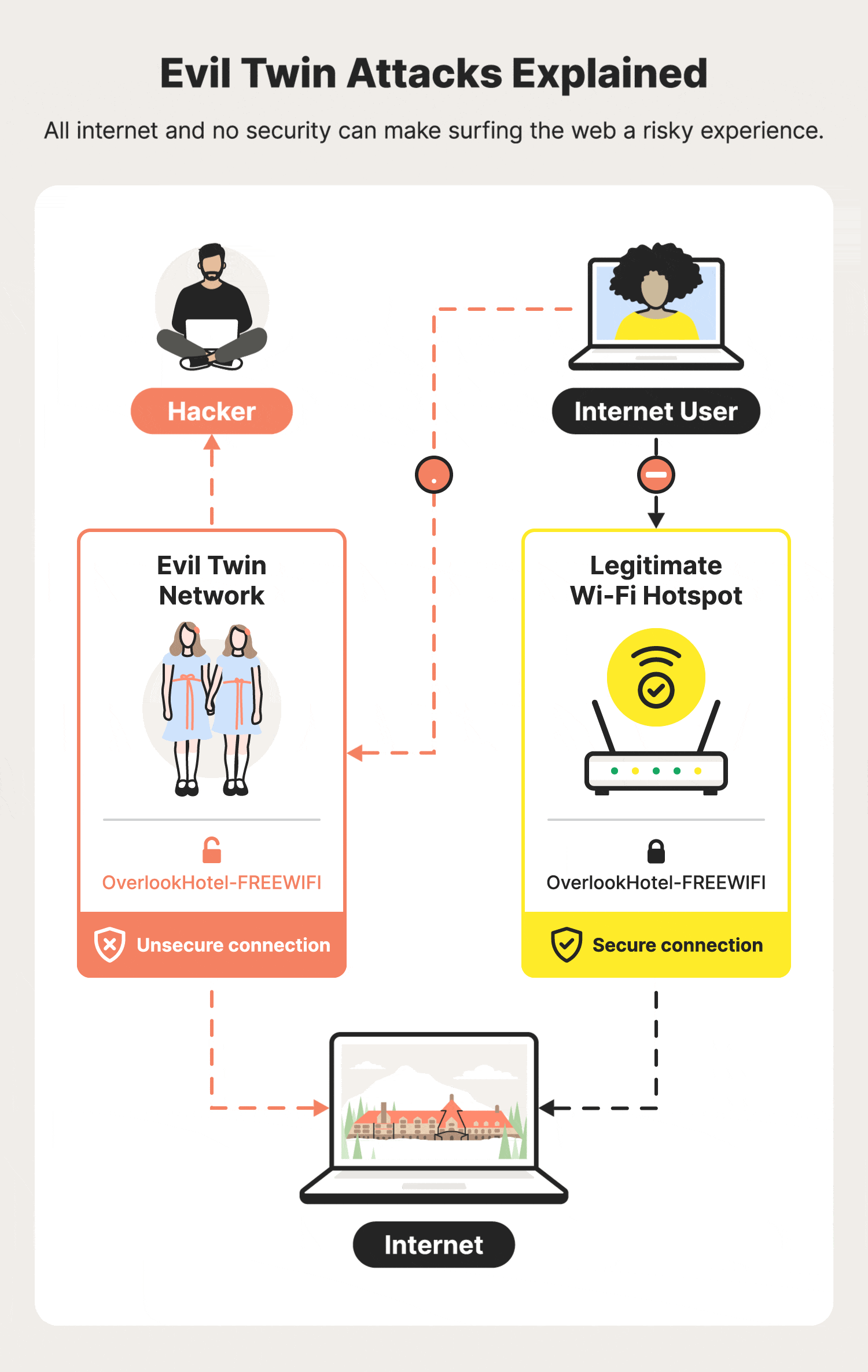
To execute an Evil Twin attack, a threat actor sets up a rogue Wi-Fi access point designed to look identical to a trusted network. Common tactics include:
- Copying the SSID (network name) of nearby Wi-Fi
- Using high signal strength to overpower the real hotspot
- Exploiting auto-connect settings on user devices
- Launching fake captive portals to harvest credentials
These setups are easy to deploy in airports, hotels, and even enterprise lobbies, making them an accessible and scalable phishing tactic.
An Evil Twin attack occurs when a bad actor creates a rogue Wi-Fi access point that mimics a legitimate network. Victims unknowingly connect to the fake hotspot, allowing the attacker to intercept or redirect their traffic to a fake site in real time.
Unlike basic phishing emails or SMS lures, Evil Twin attacks:
- Exploit trust in public or enterprise Wi-Fi networks
- Redirect users to spoofed login pages without raising browser warnings
- Enable real-time credential theft and ATO through seamless redirection
These attacks often form the first phase of a broader fraud chain, ending in stolen accounts, drained balances, or unauthorized access to enterprise systems.
This is a common pattern in modern account takeover fraud, where attackers operate upstream of authentication and inside the Window of Exposure (WoE), before traditional controls engage.
Common Evil Twin Attack Targets and Industry Trends
While Evil Twin attacks are often associated with public Wi-Fi in cafés or airports, they’re increasingly used in targeted attacks against:
- Financial institutions and fintech platforms
- eCommerce and retail loyalty programs
- Airlines and travel booking portals
- Remote access tools and VPN providers
These industries are attractive due to high account value, stored payment data, or access to identity-rich environments.
Real-world example: In 2024, Australian cybersecurity researchers revealed that a passenger on a domestic flight had mimicked the airline’s in-flight Wi-Fi. Multiple passengers unknowingly entered real credentials into a spoofed login page before the attack was flagged, demonstrating how quickly Evil Twin phishing can lead to account compromise.
Why Evil Twin Attacks Pose a Serious ATO Threat
Evil Twin phishing is not just a nuisance, it’s a rising threat vector for ATO. The danger lies in its stealth and speed:
- Users don’t need to click a link. Just connecting to Wi-Fi puts them at risk.
- HTTPS and padlocks won’t help. Attackers forward legitimate content from the real site, complete with SSL.
- MFA can be bypassed. Through real-time relay, attackers steal and reuse codes.
While many businesses rely on traditional defenses like VPNs, WAFs, or threat intelligence feeds, these methods often miss early signs of phishing attempts. They typically fail to account for browser-based manipulations during a live session, where attackers can exploit these vulnerabilities in real-time. To effectively prevent such threats, businesses need proactive defenses that detect suspicious behavior during the session itself, before credentials or sensitive information are compromised.
How to Prevent Evil Twin Phishing as Sessions Are Being Compromised
Many cybersecurity teams understand Evil Twin attacks but lack effective tools to detect or block them during live sessions, the critical point where attackers steal credentials and initiate account takeover.
A 2025 survey by TechRadar Pro, in partnership with OnePulse, found that nearly 40% of respondents feel vulnerable when using public Wi-Fi abroad, highlighting growing awareness of this threat.
Real-world data underscores this concern: a case study reported by The Hacker News in October 2024 illustrates how attackers used malicious redirects from legitimate shopping sites to fraudulent checkout pages. Evil Twin attacks are one common technique used to facilitate such malicious redirects, demonstrating how attackers can exploit public Wi-Fi to carry out phishing schemes, leading to credential theft and financial fraud.
Some organizations consider monitoring rogue Wi-Fi activity as a defense. However, this approach is limited and often insufficient to prevent credential theft. Network manipulation detection is difficult without endpoint control and doesn’t address the attack’s real impact inside the user’s browser.
Why VPNs Aren’t Enough to Prevent Evil Twin Phishing
Even virtual private networks (VPNs) – which many users rely on for public Wi-Fi security – aren’t enough to stop these attacks. While VPNs protect the data flow by encrypting it, they can’t stop users from being redirected to phishing sites. Many users, feeling secure with a VPN, may be unaware that they’re still vulnerable to these real-time threats.
The key is this: effective Evil Twin prevention activates when phishing attempts reach the browser session. This is where defenses can identify phishing pages, suspicious behavior, and credential misuse in real time, stopping attackers before they steal data or take over accounts.
How to Evaluate Solutions for Preventing Evil Twin Attacks
When selecting a solution to combat Evil Twin attacks, focus on capabilities that address the core weaknesses of traditional defenses:
- Browser-level visibility: Ensure that your solution can monitor and analyze user behavior in the browser. This allows it to detect phishing attempts in real-time, even if the attack happens within the session itself.
- Real-time phishing site detection: Choose a solution that can identify fake sites or spoofed domains quickly, even those that have not yet been added to known threat databases.
- Device and session anomaly detection: Look for a system that can flag unusual or untrusted device activity, such as a sudden device change or suspicious login patterns, indicating a potential ATO risk.
- Suspicious session behavior detection: Evaluate if the solution can monitor for red flags like credential relay attempts or bot-driven automation, which are common in live-session attacks.
- Decoy credential injection: Effective solutions inject decoy credentials, disrupting the attacker’s plans and exposing them before damage occurs.
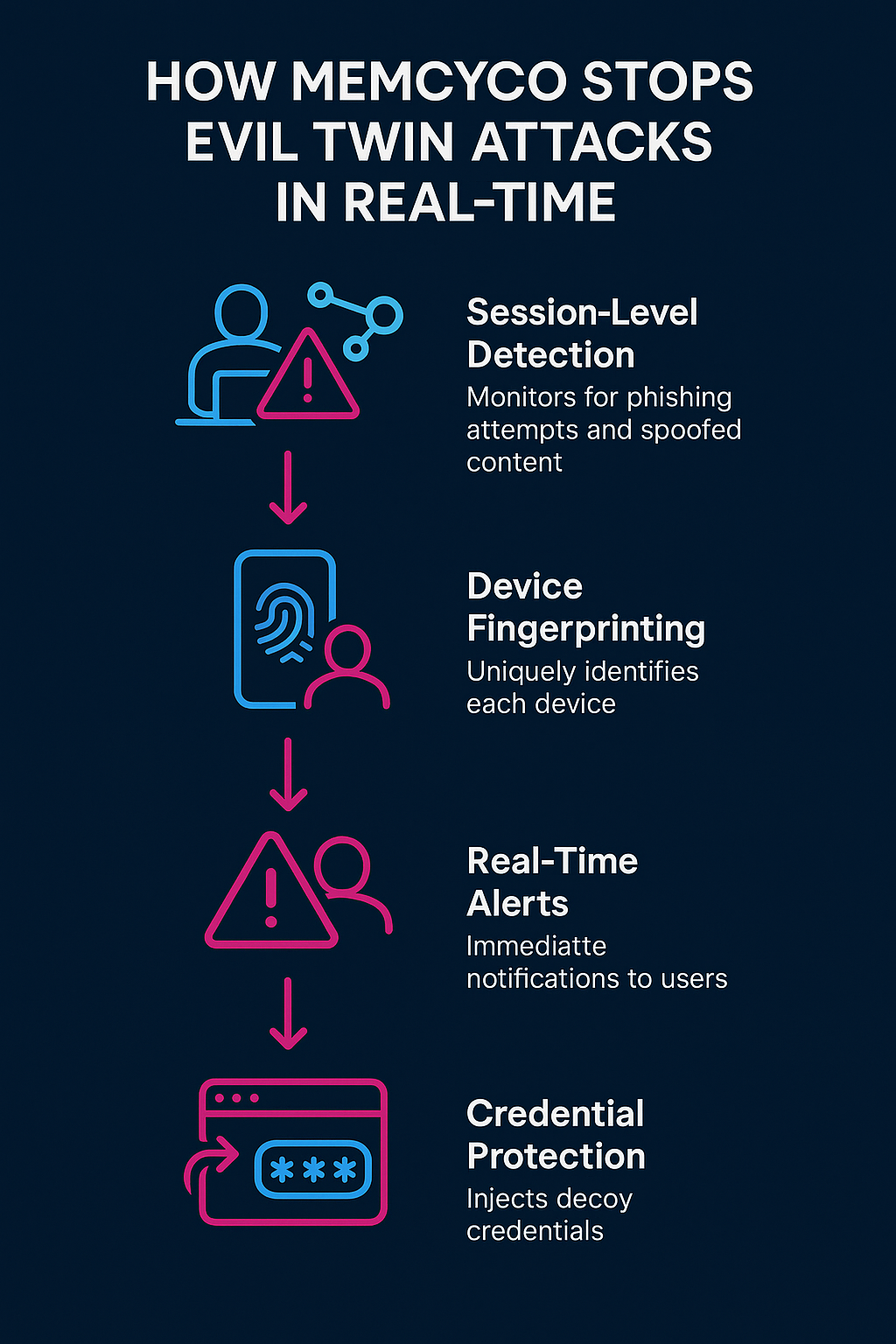
How Memcyco Stops Evil Twin Attacks in Real Time
Memcyco focuses on defeating Evil Twin attacks at the critical moment, during the browser session when credential theft and ATO risks first arise. Memcyco’s protections include:
Device DNA and Session Intelligence
Memcyco creates a persistent device profile that goes beyond traditional fingerprinting. This enables detection of suspicious login attempts from unknown or new devices, including cases where attackers “follow” victims from phishing sites to legitimate sites. Sudden device or session fingerprint changes after phishing referrals trigger alerts indicating probable Evil Twin activity.
Decoy Credential Injection
When a user submits credentials on a phishing site, Memcyco replaces them with marked decoy credentials. If attackers try to use these decoys on the genuine site, the system immediately detects and reports compromised accounts, allowing security teams to act proactively.
Real-Time Phishing Warnings
Users visiting a detected phishing (spoofed or cloned) site receive immediate alerts warning them of the threat before they enter credentials, reducing victimization risk.
Suspicious Login and Unknown Device Detection
Memcyco monitors login patterns to identify suspicious activities such as multiple failed login attempts, logins from unrecognized devices, and login attempts linked to known phishing site visitors. These detections enable rapid response to ongoing attacks.
Together, these features enable Memcyco to provide comprehensive protection against Evil Twin attacks, neutralizing threats before attackers can successfully use stolen credentials or compromise customer accounts.
Time to Rethink Evil Twin Attack Prevention? Start with a Memcyco Demo
In short, real-time protection against Evil Twin attacks, and other advanced ATO threats like reverse proxy phishing, is no longer optional. Both these attacks rely on real-time phishing using advanced Man-in-the-Middle techniques to steal credentials and instantly compromise accounts in real time, making proactive defense crucial. It’s the optimal way to stop credential theft before damage occurs.
Explore how Memcyco protects your customers from real-time phishing threats →
Book a product tour and discover the secret-sauce technologies helping Memcyco customers reduce incident-related opex by tens of millions annually.
What is an Evil Twin attack?
An Evil Twin attack involves a rogue Wi-Fi network impersonating a legitimate one to trick users into connecting. Once connected, victims are redirected to fake sites designed to steal credentials or sensitive data, often leading to account takeover or financial fraud.
How do Evil Twin attacks bypass traditional security?
They exploit trusted SSL connections and use real-time site forwarding, allowing them to appear legitimate. Many tools cannot see what happens inside the browser session.
Can VPNs or HTTPS prevent Evil Twin phishing?
No. VPNs may secure outbound traffic, but they don’t stop phishing redirects once users connect. HTTPS only confirms encryption, not the legitimacy of the site being visited.
What industries are most at risk?
Banking, eCommerce, travel, and fintech platforms are top targets due to stored financial data and customer account value.
How does Memcyco stop Evil Twin ATO attacks?
Memcyco detects suspicious session transitions, uses decoy credentials to expose attackers, and provides real-time phishing site detection, all without needing control over user devices or Wi-Fi networks.



















