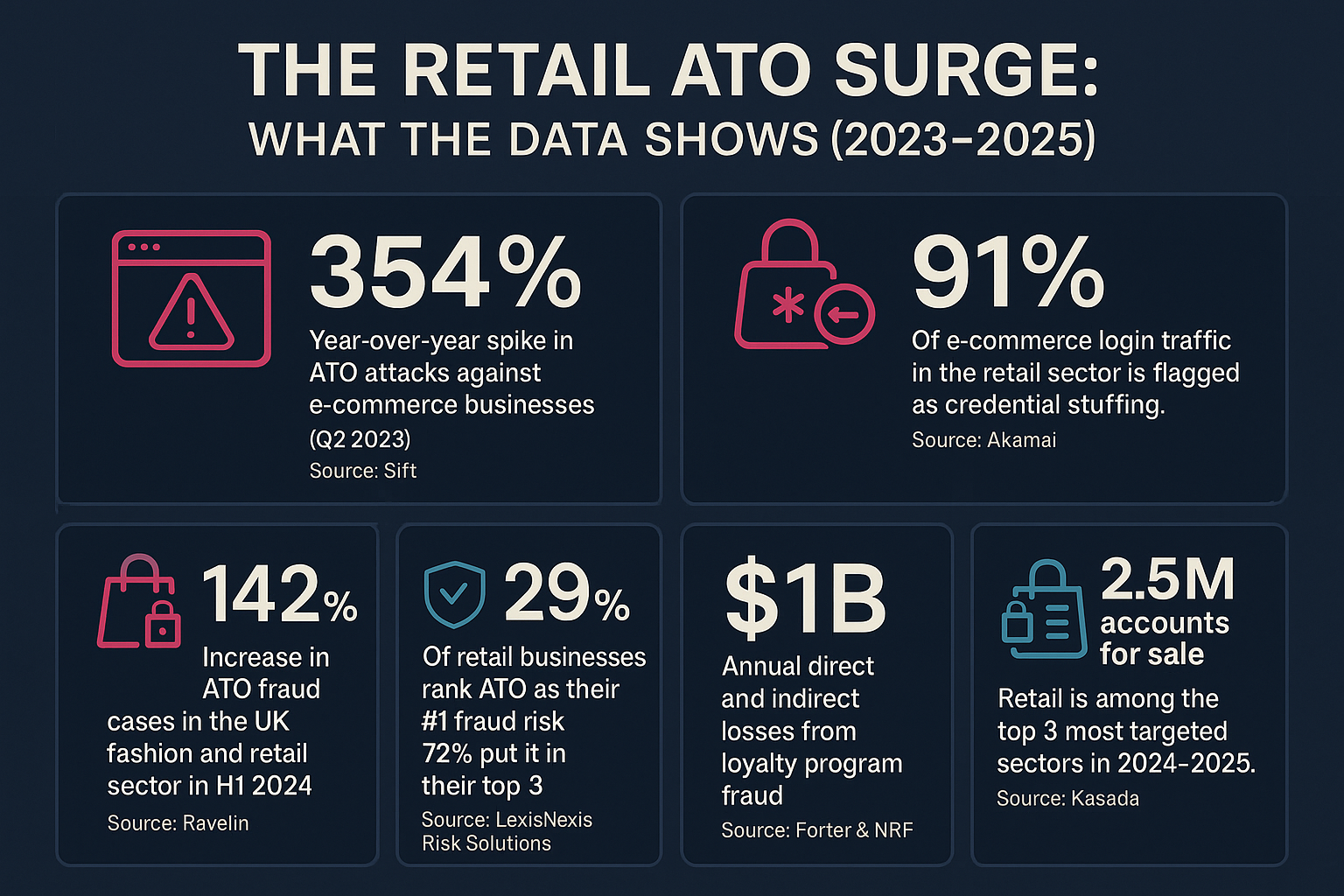
Retail account takeover fraud has surged in recent years, with attackers exploiting stored payment details, loyalty points, and digital wallets. This blog analyzes five of the biggest and most impactful retail account takeovers in recent years, evealing how each unfolded, how customers were affected, and how real-time, in-session defenses could have changed the outcome.
The following five high-profile cases across loyalty, e-commerce, hospitality, digital wallets, and luxury retail demonstrate how customers were directly impacted – and how real-time, browser-level defenses could have changed the outcome.
Case Study 1: Boots Advantage Card Breach (2020)
Recap
Boots temporarily suspended its Advantage Card loyalty program after detecting a large-scale credential stuffing attack. Roughly 150,000 customer accounts were affected, with attackers attempting to redeem loyalty points for purchases.
Attack Vector
Credential stuffing using usernames and passwords recycled from other data breaches.
Outcome
Customers found their loyalty balances drained or locked. Boots was forced to reset accounts and restore points, facing reputational damage over program security.
How Memcyco Would Have Helped
- Detects credential stuffing attempts in-session with high fidelity, including rapid login failures and unusual access patterns.
- Replaces entered credentials with traceable decoy credentials during suspicious attempts – rendering stolen data useless and exposing attacker devices when replayed.
- Provides per-user and per-device intelligence to guide targeted remediation instead of mass account resets.
The Boots incident demonstrates how credential reuse directly threatens stored value programs – and how real-time, in-session defenses can prevent attackers from monetizing stolen logins.
Related: How Browser-Level Signals Help Prevent Credential Stuffing Attacks
Case Study 2: Chick‑fil‑A Rewards Breach (2022)
Recap
Over 71,000 loyalty accounts were hijacked in a credential stuffing campaign that lasted for months. Attackers drained rewards balances and purchased gift cards.
Attack Vector
Automated login attempts with reused credentials from other breaches.
Outcome
Customers found their rewards accounts empty, forcing Chick‑fil‑A to compensate victims and reset accounts at scale.
How Memcyco Would Have Helped
- Detects credential stuffing attempts in-session with high fidelity, including failed login spikes.
- Flags attack devices and login patterns for immediate lockout or added friction.
- Provides per-user insights to prioritize response and avoid blanket resets.
The Chick‑fil‑A incident highlights how attacks can persist undetected without real-time visibility – visibility Memcyco delivers from the first login attempt.
Case Study 3: The North Face Credential Stuffing (2022)
Recap
The North Face reset nearly 195,000 customer accounts following a credential stuffing attack, exposing names, emails, addresses, and purchase histories.
Attack Vector
Large-scale automation of breached username and password combinations.
Outcome
Personal details were exfiltrated, resold on dark markets, and reused in phishing campaigns. Customers endured repeated password resets and reputational fallout from the brand.
How Memcyco Would Have Helped
- Identifies credential reuse attacks early using in-session behavioral signals.
- Replaces entered credentials with traceable decoy credentials to detect replay attempts and render stolen logins useless.
- Tags suspicious devices and provides session-level forensics for SOC teams.
This breach illustrates how credential-based attacks enable downstream fraud – a chain Memcyco breaks before it starts.
Related: 7 Best Practices for eCommerce Fraud Prevention
Case Study 4: PayPal Digital Wallet Breach (2022)
Recap
Nearly 35,000 PayPal accounts were hijacked in a credential stuffing assault, exposing names, addresses, birthdates, and in some cases Social Security numbers.
Attack Vector
Credential reuse against PayPal’s digital wallet login.
Outcome
Customers faced heightened risk of identity theft. PayPal was fined and forced to provide credit monitoring – underscoring the regulatory and reputational cost of inadequate defenses.
How Memcyco Would Have Helped
- Detects real-time login anomalies and credential replay patterns.
- Surfaces impacted users and risky devices before funds or data are lost.
- Swaps legitimate credentials with traceable decoy credentials during suspicious login attempts – rendering stolen credentials ineffective and exposing attack infrastructure.
The PayPal breach shows how regulatory exposure grows with every missed signal – Memcyco ensures those signals are captured the moment a session begins.
Case Study 5: Neiman Marcus Breach (2021)
Recap
Attackers accessed 4.6 million customer accounts, exposing names, passwords, payment card numbers, and loyalty balances.
Attack Vector
Credential compromise leading to widespread ATO and loyalty fraud.
Outcome
Customers saw loyalty balances drained and card details exposed – leading to direct financial losses and identity theft attempts.
How Memcyco Would Have Helped
- Flags credential-based intrusions during login, not after the fact.
- Replaces stolen credentials with traceable decoy credentials that alert teams when replayed – rendering them useless to attackers.
- Provides per-victim intelligence to inform customer outreach and reduce damage.
This breach underscores how fast attackers can monetize compromised credentials – Memcyco’s role is to stop that monetization in real time.
Patterns Behind Retail ATOs
These cases highlight recurring weaknesses:
- Credential reuse – attackers exploit recycled usernames and passwords at scale.
- Phishing and impersonation – cloned sites deceive customers and staff into handing over credentials.
- Stored value theft – loyalty balances and digital wallets remain attractive targets.
- Lack of in-session detection – most defenses trigger only after compromise.
Retail account takeovers thrive on credential reuse and stored value theft. Without in-session detection, attacks succeed in draining loyalty points, exploiting wallets, and monetizing personal data before retailers or customers can react.
Many of the incidents described happen exactly as seen in the how modern account takeover fraud starts and evolves, with detection occurring only after access was already established.
How Memcyco Prevents Retail Account Takeovers
Endorsed by analysts, Memcyco’s preemptive cybersecurity platform closes gaps left by scanning and takedown solutions, threat intelligence feeds, and even multifactor authentication.
- Detect – Flags spoofed websites, credential stuffing, anomalous login behavior, and attacker devices.
- Protect – Uses traceable decoy credentials, device DNA, and authenticity markers to safeguard sessions.
- Disrupt – Neutralizes phishing operations through decoy feedback and takedown support.
- Reveal – Surfaces per-victim insights and attack telemetry to guide rapid response.
- Pre-empt – Establishes behavioral baselines and detects early reconnaissance before ATO attempts begin.
Why Retail Account Takeover Attacks Do Not Have to Succeed
Account takeovers in retail don’t persist because they’re hard to detect – they persist because most systems detect too late. Controls that rely on post-login signals or batch analysis allow attackers to operate freely for minutes, hours, or even days before action is taken.
The window between intrusion and response is the real threat surface. It’s where stored value is exfiltrated, trust is eroded, and compliance fallout begins.
Memcyco narrows this window to seconds. Its session-level telemetry surfaces credential misuse, site impersonation, and device anomalies as they unfold – enabling organizations to respond before credentials are weaponized or customer value is lost.
Book a Memcyco product demo and discover the truly preemptive cybersecurity approach global enterprises are turning to for avoiding being in the headlines.
Related:
- The 5 Biggest Bank Account Takeover Attacks in Recent Years (and How They Could Have Been Stopped)
- How To Prevent Loyalty Account Takeovers in Real Time
- Automated Brand Impersonation Protection: How It Works (and Why It Matters Now)
FAQs About Retail Account Takeover Fraud
What is retail account takeover fraud?
It’s when adversaries hijack customer accounts to extract stored value, such as loyalty points, gift cards, or linked payment methods. This often happens through credential reuse, phishing, or automation.
How do attackers take over customer accounts in retail?
They typically use phishing sites or credential stuffing attacks to steal login credentials. Once inside, they exploit stored payment methods or loyalty balances before detection can occur.
What is credential stuffing and why is it common in retail?
Credential stuffing is when attackers use automated tools to test stolen username-password combinations across sites. It’s common in retail because many customers reuse passwords, and accounts often contain valuable data or balances.
Why are loyalty points and digital wallets popular fraud targets?
They’re easy to monetize and often lack strong fraud controls. Attackers can quickly convert points or stored funds into gift cards, purchases, or resale value.
How can retailers stop phishing and credential-based account takeovers?
By deploying in-session protection that detects spoofed sites, credential replay patterns, and abnormal login behavior – all before attackers succeed. Static defenses like takedowns or MFA are not enough.
How does Memcyco protect customer accounts from takeover fraud?
Memcyco blocks suspicious logins in-session, replaces entered credentials with traceable decoy credentials on spoofed sites, and warns users in real time. This keeps stored value secure before losses occur.



















