Digital Impersonation Protection
Stop online brand impersonation attacks from their inception
Only Memcyco tracks digital impersonation attacks in real-time
right form the pre-attack preparation phase, identifying each phase,
each individual victim, the attack device.
The evolving threat from online brand impersonation
Phase 1
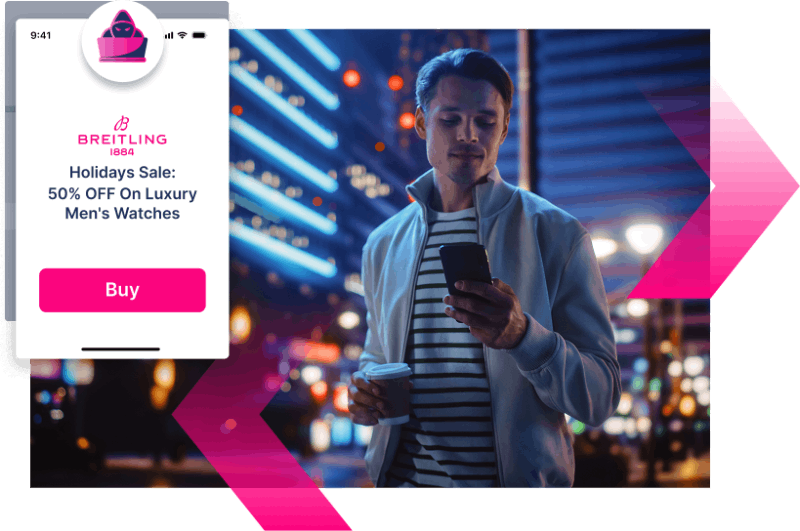
The malicious message
Your customers are targeted with deceptive messages that increasingly use Gen AI to trick them into taking the bait.

What if you could
Detect and neutralize impersonation scams right from their inception
- Spot phishing attempts by detecting malicious intent
- Identify suspicious messages before they lead to impersonation scams
- Safeguard customer accounts pre-emptively before scams go live

Phase 2
The Lure
Consumers click links to impersonating sites, while you’re in the dark about how, where and who got scammed.
What if you could
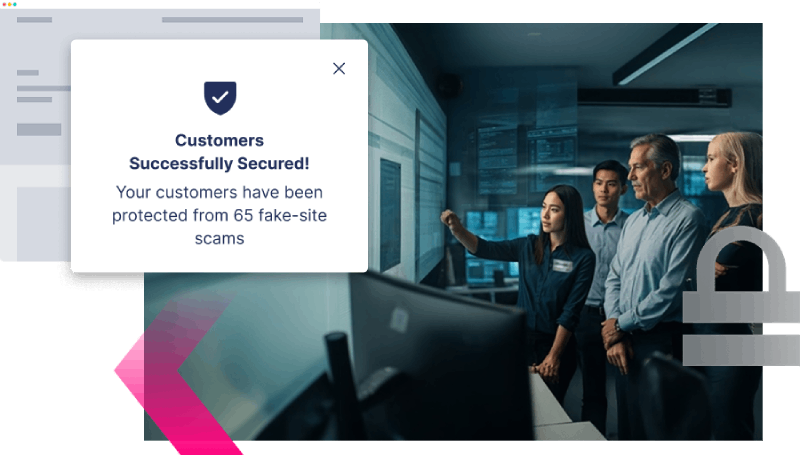
Shield customers from impersonating sites, and identify those that visit them
- Detect impersonating domains the moment they go live
- Warn users in real time when accessing fraudulent sites
- Deceive and disrupt attackers to minimize scam impact
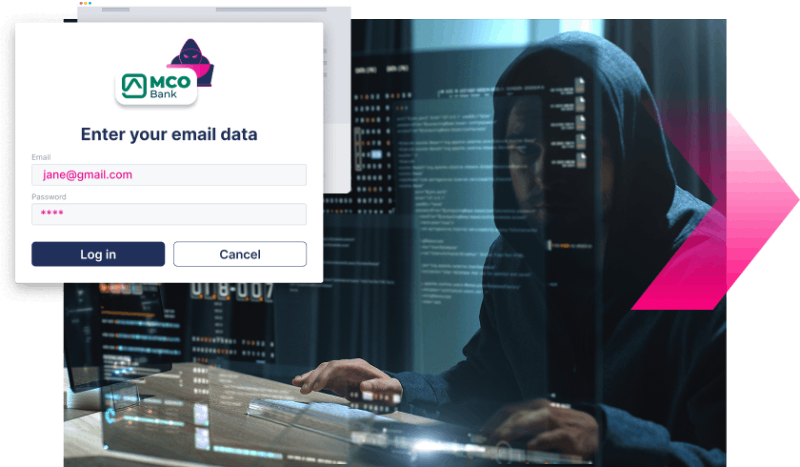
Trap A
Fake forms
Scammers clone or spoof data capture forms, targeting sensitive customer data.

What if you could
Shield customer credentials and card data, no matter how many scams they fall for
- Secure accounts while scams are live, and after they’re taken down
- Reduce incident-related investigation, remediation and expenses
- Optimize Internal Controls and improve compliance posture

Trap B
Fake stores
Brand abusers steal revenue with fake online stores that use SEO poisoning and fake paid ads to steal traffic.

What if you could
Protect revenue, brand equity and customer loyalty from fake stores
- Detect fake stores as soon as they go live
- Stop fake stores repeatedly popping back up under a different URL
- Automatically disarm SEO poisoning and fake paid ads

Trap C
Fake news
Fraudsters launch media sites that spread fake news about your business and C-level executives.

What if you could
Safeguard share price and business credibility from malicious information
- Prevent PR disasters and loss of trust from investors
- Maintain business continuity while fake news sites are automatically neutralized
- Protect your leadership team from misinformation that harms their career
Real-time online brand impersonation detection and disruption
With Memcyco
Immediate, granular and accurate detection of fake sites
Stop customers falling for scams, no matter how long they’re live
Actively disrupt scammers while identifying and protecting victims
Without Memcyco
Periodic scanning and partial detection of fake sites
Customers lured and defrauded by fake sites while they’re taken down
No proactive measures, no insight into impacted customers and which fake sites they visited
Discover why global brands replace their previous solution with Memcyco

Keep damage from brand scams under control, permanently
Proven first year
ROI of over
10x
Reduce mean time
to detection to
Zero
Instant fake site
detection rate of
>80%
Already neutralizing digital impersonation in real time? Solve more

Man in the Middle (MiTM) Protection


Digital Impersonation



Credential Stuffing



Fake e-shops, purchase scams, gift card scams

Get a Custom Demo
See it in action and discover why others switch to Memcyco
Get a demo to learn how Memcyco customer :
-
Identify individual scam victims in real-time
-
Predict and preempt ATO incidents
-
Deceive threat actors
Frequently asked questions
What is online brand impersonation, and how does it affect businesses online?
Online brand impersonation, also known as digital impersonation, occurs when attackers create fake websites, forms, or messages that mimic legitimate brands to deceive customers. This leads to account takeover (ATO), lost revenue stolen credit card data, lost revenue, damaged brand reputation, and increased regulatory risks. It can also erode customer trust, making it vital for businesses to have robust protection measures in place.
How can businesses detect fake websites in real time?
Businesses can use advanced tools powered by AI and behavioral analysis to monitor suspicious domains and identify impersonating websites as soon as they go live. Memcyco provides this capability with its instant digital impersonation detection and protection technology, which flags threats proactively to prevent scams before they escalate.
How can businesses protect customer accounts from impersonation scams?
To safeguard customer accounts and sensitive data, businesses need solutions like Memcyco’s real-time detection and preemptive security measures. These tools shield credentials and PII even if customers interact with malicious sites or forms, ensuring data remains secure while reducing incident-related costs.
How to protect customer credentials from phishing and fake websites?
Yes, real-time brand impersonation protection can safeguard user credentials by identifying and neutralizing fake websites, phishing attempts, and malicious forms before customers fall victim. Memcyco’s advanced detection technology and device fingerprinting ensures that sensitive data, such as login credentials and personal information, remains secure, even if customers engage with fraudulent sites. This proactive approach prevents data theft and minimizes the impact of impersonation scams.
What are the key differences between traditional and real-time impersonation detection?
Traditional detection relies on periodic scans, identifying fake sites after damage is done. Memcyco’s real-time detection uses AI to instantly identify threats, provide detailed insights into malicious activity, and actively disrupt scams before they harm customers. This proactive approach reduces risks and improves operational efficiency.
How can companies reduce costs related to phishing investigation and remediation?
Memcyco helps companies lower costs by offering instant fake site detection, automated takedowns, and granular attack insights about the attack, the attacker and even individual victims. These features reduce the need for lengthy investigations, enabling faster resolutions and minimizing resources spent on remediation, all while enhancing fraud prevention.
Which industries are most vulnerable to online impersonation scams?
Industries with high online customer engagement—such as retail, finance, healthcare, and technology—are particularly vulnerable. These sectors often deal with sensitive data, making them prime targets for impersonation attacks. Memcyco’s real-time detection and prevention capabilities provide real-time, AI-driven solutions that offer previously unobtainable attack insight and protection for these industries.