Man in the Middle (MiTM) Protection
Predict and combat advanced ATO attacks, with MitM countermeasures
Extend your ATO defenses and drive down the cost of advanced phishing attacks. Shield customer accounts proactively against network redirection and man-in-the-middle tactics.
Stop man-in-the-middle attacks that bypass your MFA-based defenses

Be Ready for
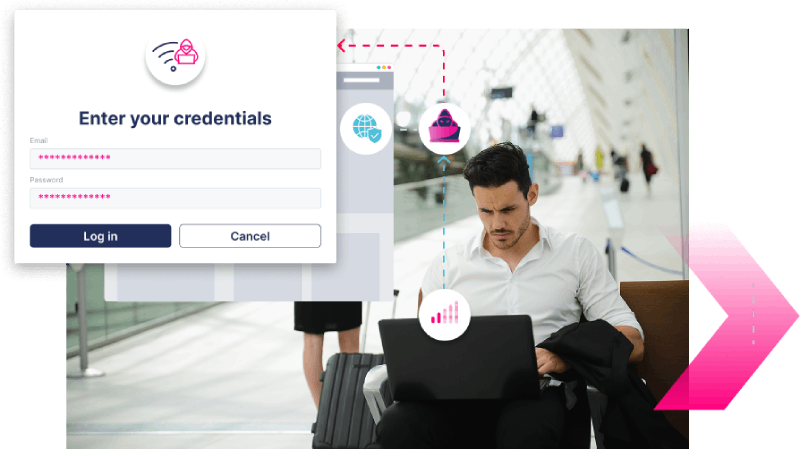
Reverse proxy phishing
How secure is MFA if attackers can capture and use credentials and OTPs in real time, just as customers log in? That’s how Real-Time Phishing Proxy attacks bypass MFA, redirecting victims to fake URLs designed to steal and relay login data instantly.

What if you could
Detect and disrupt real-time phishing proxy attacks before attackers take control?
- Detect credential and MFA harvesting as they happen
- Identify and alert individual customers targeted by reverse-proxy phishing attacks
- Preemptively protect customer accounts before attackers complete the ATO
Defend Against
Evil Twin Scams
How safe are the Wi-Fi networks your customers recognize and trust when attackers can mimic them, gain control of the connection, and redirect them to credential-stealing sites? That’s an Evil Twin attack. These spoofed sites can capture both credentials and MFA codes in real time, turning trusted connections into full account compromise.
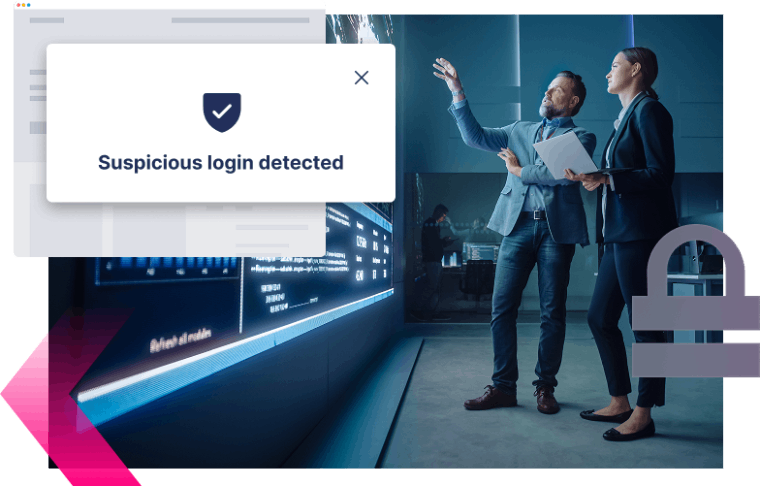
What if you could
Expose and block attackers exploiting Evil Twin network attacks?
- Detect and analyze sessions originating from rogue Wi-Fi access points, in real time.
- Identify customers targeted by Evil Twin redirection attempts
- Proactively disrupt credential harvesting attempts from rogue WiFi networks
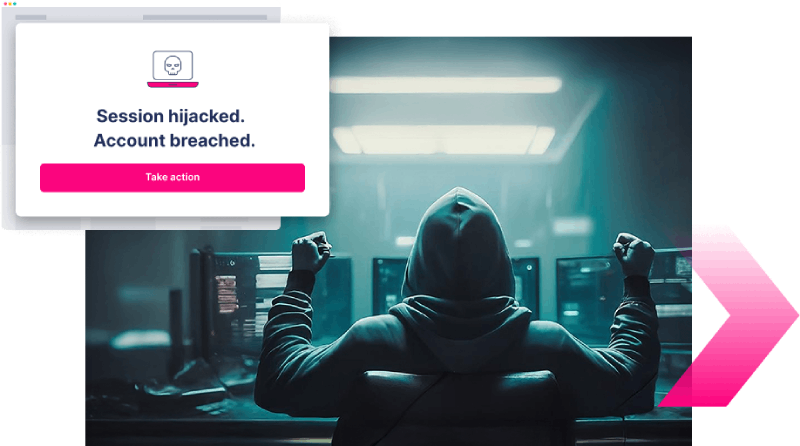
Effortlessly Combat
DNS Poisoning Attacks
How safe is a customer’s browser when attackers silently poison DNS and redirect them to spoofed sites, while your legitimate URL still appears in the address bar? That’s DNS poisoning. These fake sites can capture both credentials and MFA codes in real time, making trusted URLs a gateway to full account takeover.
What if you could
Effortlessly dismantle phishing and ATO attempts using DNS poisoning?
- Detect when customers land on spoofed sites via DNS poisoning
- Identify customers exposed to DNS-based redirection attacks
- Proactively block credential theft and account takeover attempts
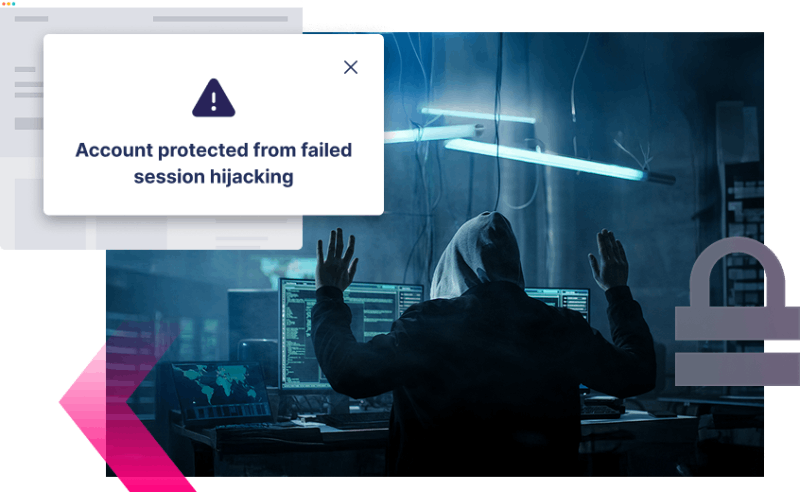
Effortlessly counter real-time phishing attacks that use MitM techniques
With Memcyco
Detect and disrupt MitM-driven phishing and ATO in real time
Captures browser-level activity and the visible footprint of network-layer attacks
Agentless, browser-based, no network integration required
Without Memcyco
Depends on logs and traffic. Threats surface post-compromise
Miss browser-level threats like phishing proxies and relays
Needs agents, proxies, or infrastructure tuning to be effective
Solution Brief
Discover why global enterprises replace their previous solution with Memcyco

Fight real-time phishing, with advanced Man-in-the-Middle attack protection
Reduce ATOs
by at least
50%
Reduce mean time
to detection to
Zero
Slash incident-related
expenses by
$Millions
Already solved MitM attacks? Solve more

Man in the Middle (MiTM) Protection





Credential Stuffing



Fake e-shops, purchase scams, gift card scams

Get a Custom Demo
See it in action and discover why others switch to Memcyco
Get a demo to learn how Memcyco customer :
-
Identify individual scam victims in real-time
-
Predict and preempt ATO incidents
-
Deceive threat actors
Frequently asked questions
What is a Man-in-the-Middle attack?
A Man-in-the-Middle (MitM) attack occurs when a cybercriminal secretly intercepts and manipulates communication between two parties, often to steal login credentials, financial data, or sensitive information. These attacks can occur over compromised networks, infected devices, or manipulated browsers.
What are the types of Man-in-the-Middle attacks?
MitM attacks come in various forms, each exploiting different vulnerabilities:
- Session Hijacking – Attackers steal active session tokens to take over user accounts.
- Evil Twin Attacks – Fake WiFi hotspots trick users into connecting, allowing attackers to intercept data.
- DNS Poisoning – Attackers manipulate DNS records to redirect users to fraudulent websites.
- Man-in-the-Browser (MitB) Attacks – Malware alters transactions or captures credentials within the browser.
- TLS Stripping – Downgrades secure HTTPS connections to unencrypted HTTP, exposing user data.
Each of these techniques can be used to steal credentials, bypass security defenses, or manipulate sensitive transactions.
Does a VPN protect against Man-in-the-Middle attacks?
A VPN (Virtual Private Network) encrypts your internet traffic, making it harder for attackers to intercept data on unsecured networks. However, it does not protect against all MitM attacks—especially those that exploit compromised browsers, infected devices, or rogue access points.
MitM threats like DNS Poisoning, Evil Twin, or Man-in-the-Browser attacks work in the background, making them almost impossible to detect without a dedicated security solution that detects manipulation in real time.
How to detect a Man-in-the-Middle attack?
Detecting a MitM attack can be challenging because attackers operate stealthily. However, signs of an attack include:
- Unexpected security warnings – Frequent HTTPS errors or browser certificate warnings.
- Slow or altered website behavior – Pages loading incorrectly, redirects to strange domains.
- Duplicate WiFi networks – Multiple networks with similar names in public places.
- Unusual login attempts – Receiving login alerts from unknown devices.
To stand any chance of identifying Man-in-the-Middle attack, it’s important to establish a threat intelligence framework to help recognize patterns and anomalies. Even once you establish one, you may only detect MitM attacks once the damage is done. For pre-emptive prevention, you’ll need real-time capabilities.
How to prevent a Man-in-the-Middle attack?
Preventing MitM attacks requires a combination of security best practices and real-time detection:
- Use encrypted connections – Always verify HTTPS and avoid unsecured WiFi.
- Enable MFA (Multi-Factor Authentication) – Adds an extra layer of security.
- Monitor for unusual login behavior – Attackers often attempt to use stolen credentials quickly.
- Deploy real-time MitM detection – Security solutions that identify session hijacking, rogue WiFi, and DNS manipulation can block threats before damage occurs.
By implementing these measures, individuals and organizations can significantly reduce their risk of MitM attacks.
What to look for in a MitM prevention solution?
An effective Man-in-the-Middle attack prevention solution should offer:
- Real-time detection – Identify and stop attacks before they compromise data.
- Protection beyond network encryption – VPNs and HTTPS aren’t enough; solutions should detect browser and session-level threats.
- Agentless deployment – Avoid friction with seamless browser-based protection.
- Comprehensive threat coverage – Should defend against Session Hijacking, Evil Twin, DNS Poisoning, and Man-in-the-Browser attacks.
Organizations need solutions that go beyond traditional network defenses to provide proactive protection against evolving MitM threats.
How common are Man-in-the-Middle attacks?
MitM attacks remain a significant cybersecurity threat, particularly in public WiFi environments, phishing campaigns, and credential theft operations. Cybercriminals frequently use these techniques to bypass security defenses like MFA, hijack sessions, and steal credentials.
As attackers evolve their methods, real-time MitM detection and prevention have become essential for businesses and individuals alike.