Modern security leaders know that account takeover detection (ATO) isn’t just about spotting a bad login. ATO attacks are part of a broader scam lifecycle – starting with phishing or impersonation, escalating into credential harvesting, and ending with unauthorized access. To stop ATOs effectively, security teams need visibility into this full progression, not just the login attempt. That’s why a true ATO prevention strategy starts long before a password is entered.
Where legacy systems react late, offering zero visibility of the attack, attacker or victims, Memcyco exposes digital impersonation, phishing and ATO attacks from their inception in real-time with a truly predictive, preemptive, and proactive model recognized by industry analysts. If you want to move faster than your adversaries, these are the five steps that matter.
For a broader breakdown of how modern account takeover attacks unfold, where traditional defenses fail, and how to preempt ATO attempts, read our Account Takeover Fraud Guide.
How to Detect Account Takeovers in 5 Steps
- Start by identifying phishing infrastructure early.
- Detect scam interactions before users reach the login screen.
- Track attacker devices and recurring behavioral patterns.
- Predict and intercept account takeover attempts in real time.
- Feed attacker intelligence into your existing fraud models.
Step 1: Start Account Takeover Detection at the Phishing Stage
Most fraud teams still rely on external vendors to scan the web for phishing sites and take them down. But here’s the catch: takedowns are often too late to stop fraud, and they tell you nothing about who was targeted, how users were deceived, or where credentials are headed. Even multifactor authentication and suspicious login verification, essential though they are, leave gaps of missing insight and vulnerabilities.
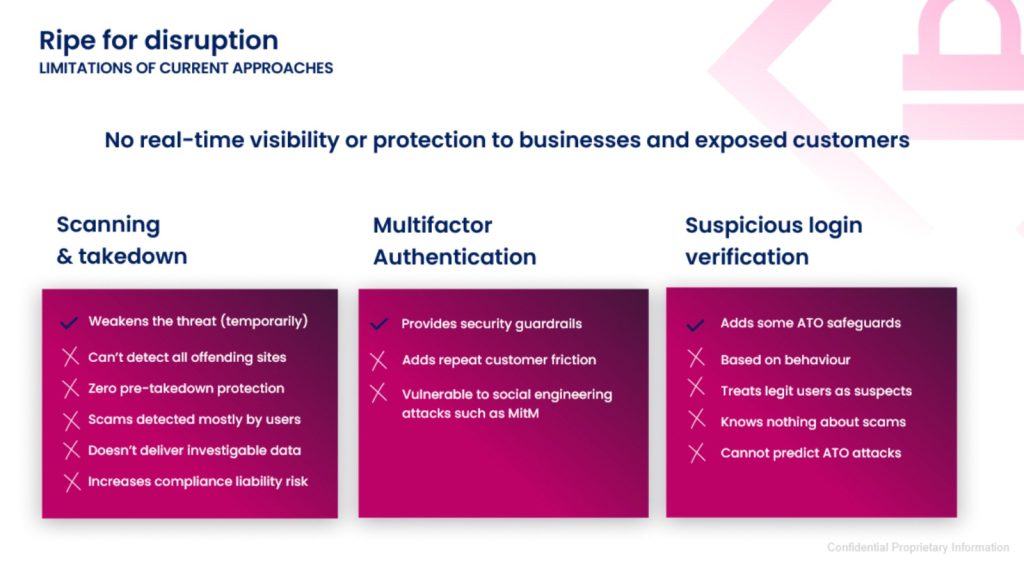
Memcyco flips that script. Instead of only taking down fake sites that are already defrauding customers, Memcyco’s proprietary ‘Nano Defender’ technology detects website and content impersonation attempts in real time. That means visibility into the phishing funnel before fake sites are even live. Combined with Memcyco’s advanced device fingerprinting that maps unique user-device pairings, Memcyco’s Nano Defenders can also help identify individual scam victims in real time, plus attack device attributes, blocking attackers pre-emptively. Needless to say, the impact on operational expenditure, caseload management, reputation, revenue and retention is profound.
Step 2: Detect Scam Interactions Before Login
Traditional ATO tools flag “suspicious” logins based on IPs or behavioral anomalies, but attackers know how to stay clean. When they come in using valid credentials on a seemingly normal device, traditional detection systems often miss them entirely.
For example, if a user’s account is accessed from a device in the same country with familiar behavioral patterns, most systems will assume it’s safe. But Memcyco sees more, detecting if that user previously visited a phishing site or displays indicators of spoofed identity, revealing an attack that would otherwise go unnoticed.
Memcyco’s Device DNA links users to trusted devices and builds a behavioral profile that can detect when an unknown or mimicking device appears at the point of credential use. Even when credentials are correct, if the device is suspicious, Memcyco flags the activity and enriches your fraud systems with high-fidelity signals, helping your team act faster and more precisely.
Step 3: Track Attacker Devices and Patterns
Why wait for a login attempt when you can see the attack coming?
Memcyco next-gen solution uses a combination of phishing infrastructure mapping, device behavior profiling, and risk signals to anticipate ATO attempts before credentials are used. Memcyco detects when a user is actively being scammed, links that to broader campaign patterns, and enables early intervention—often before the fraud team even knows an attack is underway.
That’s not just detection. That’s prediction, and it changes everything.
Step 4: Predict and Intercept ATO Attempts
In most environments, you only know a user has been phished after their account is compromised. At that point, the damage is done, and recovery becomes expensive, slow, and reputation-draining.
Memcyco identifies fake site visitors in real time. That means you can isolate at-risk users, protect their accounts, and apply additional verification steps before their credentials are ever misused. It’s how you turn a potential ATO incident into a non-event.
Step 5: Feed Findings into Your Fraud Models
Even if your fraud stack is solid, most systems operate with limited upstream data. You might catch a fraudulent transaction, but you don’t know where it came from, who else was targeted, or what attacker infrastructure was involved.
Memcyco delivers that intelligence. The platform pushes real-time telemetry, including attacker device fingerprints, victim journey data, and campaign-level patterns, directly into your risk models. That means better decisions, fewer false positives, and faster mitigation.
To achieve these five steps, research the top account takeover solutions and ask vendor teams if they’re able to offer the capabilities discussed in this article.
Frequently Asked Questions (FAQs)
How can I detect an account takeover attack before it happens?
Account takeover detection before an attack occurs requires proactive monitoring for unusual behavior — such as logins from unfamiliar devices or locations, behavioral deviations, and multiple failed login attempts. Techniques like real-time browser-level detection, device fingerprinting, and behavioral biometrics can help surface threats before credentials are exploited.
What’s the difference between ATO detection and ATO preemption?
ATO detection typically refers to spotting suspicious activity after login attempts begin. ATO preemption focuses on identifying phishing scams, compromised users, and attacker infrastructure before credential use. Memcyco enables both — but was purpose-built to prioritize preemptive protection.
How does Memcyco help prevent account takeover fraud?
Memcyco prevents account takeover fraud by exposing phishing sites, scam interactions, and suspicious devices, tracking attacks from inception to execution in real-time. Memcyco’s agentless solution uses browser-level detection, decoy credentials, and device DNA to pre-empt account takeovers empowering security teams to protect users and block fraud before damage occurs.
Stay Ahead of ATO: What Truly Proactive ATO Prevention Really Looks Like
Account takeover fraud doesn’t start with a login. It starts long before, with phishing, impersonation, and social engineering campaigns that slip past scanners and exploit customer trust.
Memcyco was built to stop ATOs not just before they succeed, but while the digital impersonation scams at their root are being planned. If your current tools only act after the fact, or can’t identify attackers or victims, it’s time to rethink what ATO prevention really means.
Book a product tour and discover Memcyco’s award-winning technology, and how it’s helping global enterprises save millions annually on scam-related expenses.



















