Credential stuffing attacks are one of the most persistent and damaging account-based threats facing security teams – and one of the hardest to detect. In 2024, Akamai, a global leader in content delivery and cybersecurity, reported more than 26 billion credential stuffing attempts globally every month – a staggering volume that’s not slowing down.
Most enterprises rely on server-side, post-login detection, which captures only successful login attempts. Failed attempts remain invisible, slowing time-to-detection and increasing the risk of successful account takeovers (ATOs).
Why is this such a challenge? The reasons are many, as we’ll explore.
For a laser-focused breakdown of how account takeover attacks actually unfold in the modern era, and what your account takeover prevention model needs to adap, see our Account Takeover Fraud guide.
But first, here’s the opportunity: with the right technology, security teams can now identify both failed and successful login attempts directly at the browser level, in real time. By doing so, they can gain immediate insight into credential stuffing campaigns in progress. That means stronger detection signals, reduced false positives, and significantly faster mean time to detect (MTTD) and mean time to respond (MTTR). This blog explores how Memcyco’s browser-level approach addresses key blind spots in credential stuffing prevention.
What Is Credential Stuffing?
Credential stuffing is an attack that uses stolen usernames and passwords, often from data breaches, to attempt unauthorized access to user accounts. Akamai’s 2024 report counted approximately 26 billion credential stuffing attempts every month, representing a nearly 50% increase over 18 months. This scale is enabled by cheap credential combo lists, residential proxies, and CAPTCHA-solving services that make these attacks highly automated and cost-effective.
Many organizations rely on common strategies for credential stuffing defense, including behavioral and AI-driven bot detection. However, these approaches typically rely on monitoring request volumes or using access challenges, and may fail to detect credential stuffing attacks that use low-and-slow patterns or smart bots that mimic legitimate users.
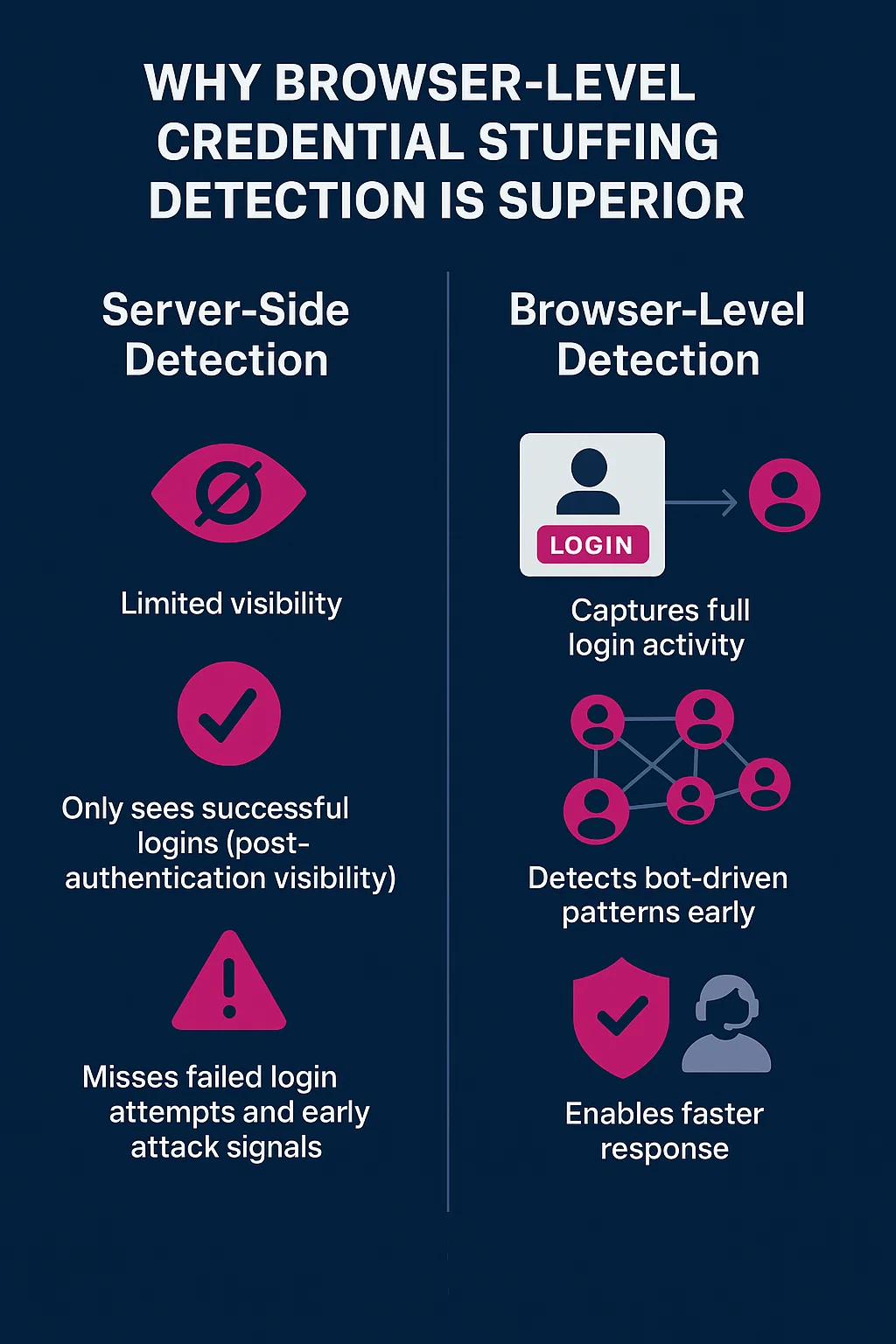
Why Server-Side Credential Stuffing Detection Falls Short
Conventional defenses depend heavily on post-login analytics. These systems:
- Monitor only successful logins
- Miss early-stage attack indicators, such as repeated failed login attempts
- Rely on backend logs, often introducing delays in detection
- Struggle to distinguish bots from real users, especially across multiple accounts
This delay leaves security teams blind to attack build-up phases. By the time an attacker successfully accesses an account, it may be too late to prevent exploitation, exfiltration, or damage to the customer experience.
Server-side solutions also face a high false positive rate. Friction in the login process due to network instability, VPNs, or password resets may trigger alerts that are indistinguishable from malicious activity, adding to alert fatigue and lowering confidence in the signal.
This difficulty is compounded by the sophistication of modern credential stuffing techniques. As Security Boulevard notes, attackers mimic legitimate login traffic, using rotating IP addresses or employing bots distributed across multiple geographic locations to avoid detection.
This subtlety makes modern credential stuffing attacks notoriously hard to detect compared with brute force attacks, as attackers leverage real credentials and automation to blend in with normal user behavior.
This is a common pattern in how modern account takeover attacks unfold, with attackers operating upstream of authentication and inside the Window of Exposure (WoE), before traditional controls engage.
Detecting Credential Stuffing Attacks Earlier with Browser-Level Signals
Credential stuffing attack detection gains a fundamentally different vantage point when powered by browser-level signals. It captures login activity at the user interface, in real time, giving security teams visibility into both failed and successful login attempts, and enabling earlier, stronger signals.
Memcyco delivers this capability with advanced signals that help detect and block credential stuffing attacks before they succeed.
Here’s how browser-level detection gives security teams an advantage:
- Detects bot-driven patterns early: Identifies repeated login attempts across accounts or devices, enabling earlier intervention. This is critical given that credential stuffing bots often mimic legitimate user behavior, rotating IPs and distributing attempts across geographic regions to evade traditional detection methods.
- Enhances behavioral visibility: Provides granular signals on login attempt timing, device behavior, and cross-attempt patterns, enabling more accurate detection of subtle attack strategies.
- Improves signal accuracy: Device-level fingerprinting reduces false positives by linking anomalous login patterns to previously observed attack behavior.
- Shortens response times: Real-time browser-based telemetry enables security teams to act before attackers gain access.
This level of visibility strengthens credential stuffing attack detection across the stack, enabling earlier detection, faster response, and more effective protection against ATO.
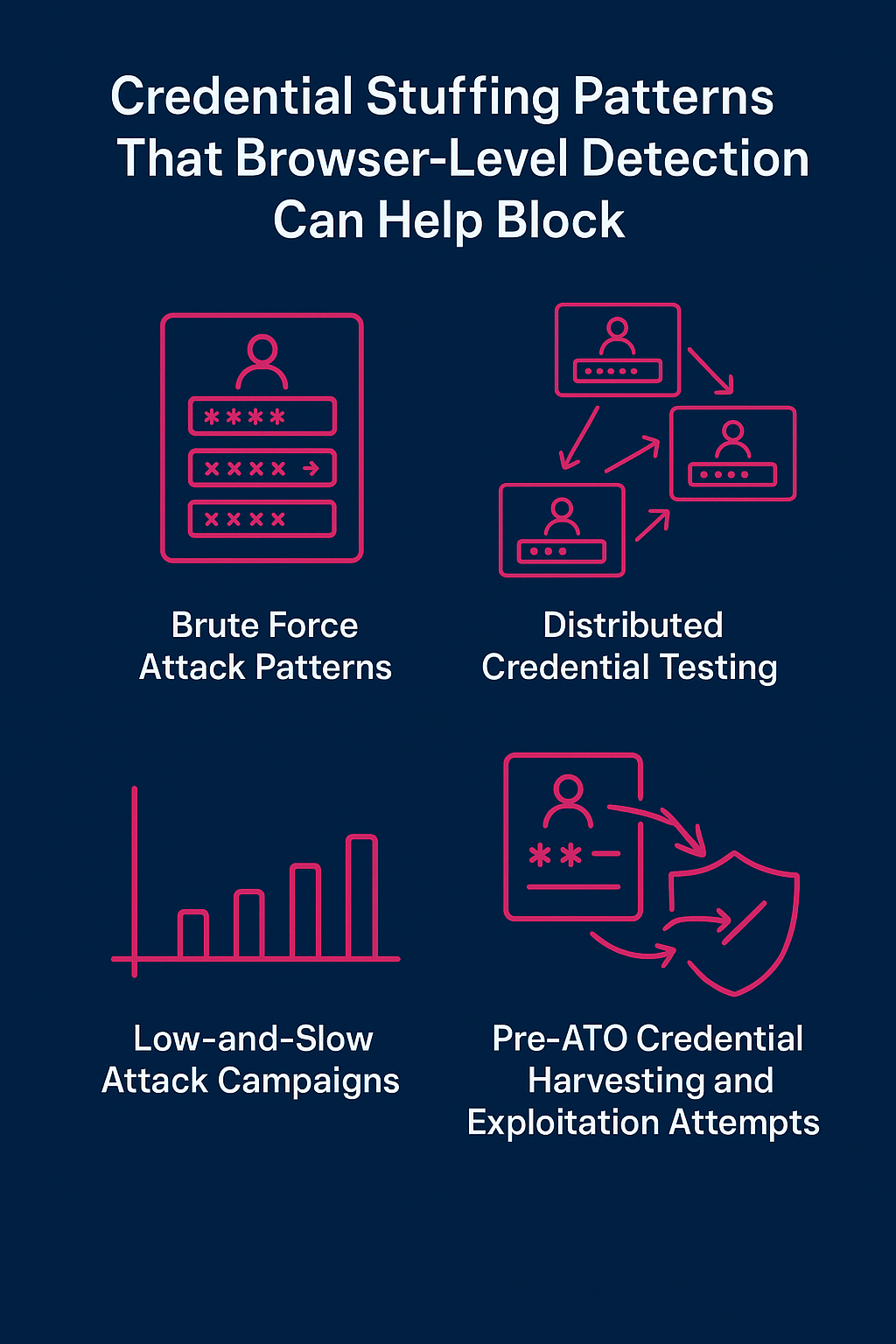
Credential Stuffing Attack Patterns That Browser-Level Signals Help Block
Browser-level detection gives security and fraud teams new visibility into attack patterns that server-side tools often miss.
Here are key credential stuffing tactics Memcyco helps detect and stop:
1. Brute Force Attack Recognition
Detect repeated login attempts on the same account with varied credentials or small permutations – a clear signal of brute force behavior. Browser-level detection spots this at the point of interaction, before the server authenticates anything.
2. Distributed Credential Testing
Attackers often test stolen credentials across multiple user accounts to avoid triggering rate limits. Memcyco detects these patterns based on device and behavior, not just account activity.
- Pre-login threshold-based blocking: While rate-limiting and CAPTCHA throttle attack volumes, Memcyco’s browser-level signal adds a real-time pre-login block, maintaining user experience while sharply reducing bot throughput.
3. Low-and-Slow Attack Campaigns
Rather than rapid-fire attempts, some attackers use low-volume, stealthy login attempts over extended periods. Browser-based credential stuffing detection enables continuous visibility into these subtle signals.
4. Pre-ATO Credential Harvesting and Exploitation Attempts
By identifying and blocking malicious credential harvesting and exploitation patterns before attackers successfully access accounts, Memcyco minimizes incident response cost, reduces fraud losses, and prevents downstream ATO damage.
Beyond Detection: Actionable Insights and Lockout
Memcyco doesn’t stop at detection. Once potential credential stuffing patterns are identified:
- Auto-lockout mechanisms can block access from suspected attack devices
- Real-time alerts are pushed to SOC teams for immediate investigation
- Per-device profiling helps identify whether the same attacker is targeting multiple accounts
- Forensic detail is preserved, enabling incident reconstruction and future tuning of fraud models
By incorporating device fingerprinting, Geo-location Based Anomaly Detection, and behavioral heuristics before login submission, Memcyco provides pre-login context that complements rate-limiting, CAPTCHA or blocklist solutions, enabling stronger bot mitigation with fewer false positives.
This level of context reduces MTTD and MTTR, helping SOC and fraud teams operate with higher confidence and efficiency.
Complementary to Existing Infrastructure
Memcyco integrates with your existing stack via:
- SIEM enrichment: Feed browser-level detection signals into your SIEM for correlation and alerting
- Risk engine augmentation: Enhance fraud scoring models with high-fidelity attack data
- No user friction: Detection is entirely agentless and invisible to the end user
Browser-level signals strengthen the entire fraud prevention architecture, particularly for enterprises operating in high-risk industries like fintech, e-commerce, and digital services.
Closing the Visibility Gap in Credential Attacks
Credential stuffing remains one of the fastest paths to account takeover. And while many organizations deploy defenses like MFA, CAPTCHA, and rate limiting, most still monitor only what happens after login, missing the opportunity to detect and block attacks earlier in the process.
Memcyco closes that gap. By bringing real-time, browser-level visibility into credential stuffing attacks, we help security and fraud teams detect malicious activity early, block attackers before they succeed, and stop credential stuffing campaigns before they result in account takeover.
Get a product tour and see for yourself how Memcyco strengthens your credential stuffing prevention strategy.
FAQs: Credential Stuffing Prevention
What is credential stuffing attack?
A credential stuffing attack uses stolen usernames and passwords, often from data breaches to attempt unauthorized access to user accounts. Attackers deploy bots to test large volumes of credentials across online services, exploiting password reuse and weak detection mechanisms.
How to detect credential stuffing?
Credential stuffing detection relies on monitoring for patterns of automated login attempts, such as rapid retries, distributed credential testing, and low-and-slow attacks. Memcyco detects these patterns directly in the browser, giving security teams earlier and stronger signals than server-side monitoring alone.
How to stop credential stuffing?
Stopping credential stuffing requires detecting and blocking attack attempts before account takeover occurs. Memcyco’s browser-level detection identifies both failed and successful login attempts in real time, enabling pre-login blocking of malicious traffic and automated lockout of attack devices.
How does Memcyco detect brute force attacks?
Memcyco identifies repeated or unusual login attempts from the same device or across accounts, using behavioral analysis and advanced device fingerprinting to detect and block brute force patterns.
Can Memcyco block credential stuffing in real time?
Yes. Once an attack pattern is identified, Memcyco can automatically block suspicious devices and alert security teams, stopping attacks before account takeover occurs.
How does this reduce false positives?
Memcyco improves detection accuracy by combining browser-level data with behavioral patterns and device intelligence, ensuring legitimate user issues aren’t misclassified as fraud.



















