For security teams, it’s no great revelation to say that DNS cache poisoning prevention is essential for guarding against attacks using that vector. But it’s easier said than done.
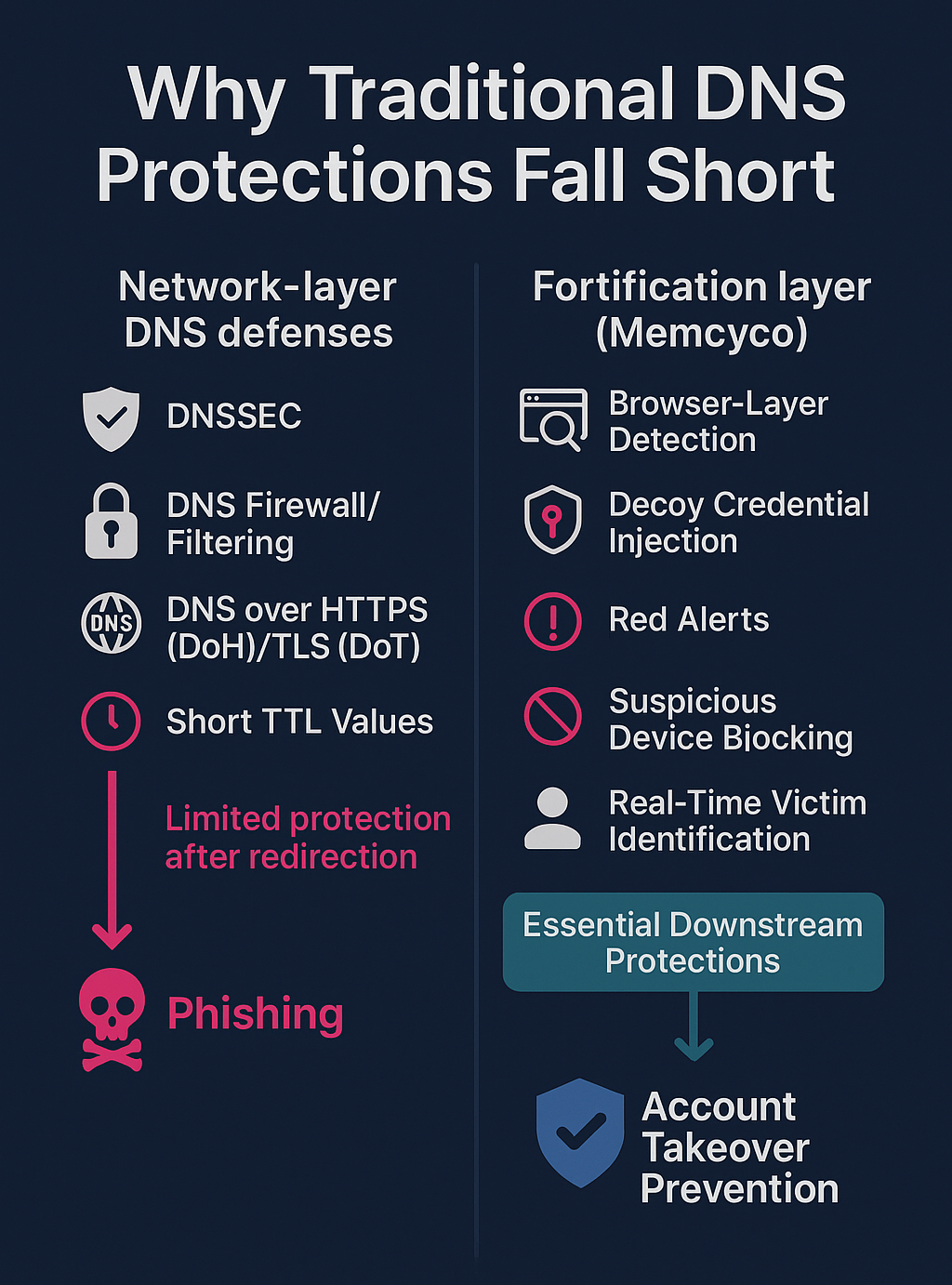
While traditional network-layer defenses like DNSSEC reduce poisoning risk, they can’t fully prevent it. Downstream – after redirection – bad actors await, ready to harvest credentials, bypass MFA, and take over accounts.
To prevent account takeover (ATO) fraud resulting from DNS poisoning, network-layer protections can be fortified with real-time defenses capable of detecting phishing attempts as users interact with malicious sites. These measures can neutralize stolen credentials using decoy data, disrupt attackers, and block suspicious devices, stopping attacks before account compromise occurs. Before we unpack the details, let’s cover the basics.
What Is DNS Poisoning?
DNS poisoning, also known as DNS cache poisoning, is a technique where attackers inject false information into DNS resolver caches. This causes internet users trying to visit legitimate websites to be redirected silently to fake, attacker-controlled sites. These malicious sites often look identical to the real ones, tricking users into giving up sensitive data like login credentials or payment details.
DNS poisoning exploits vulnerabilities in the DNS system to manipulate domain name resolution, enabling phishing and account takeover attacks without users realizing they’ve been redirected.
DNS Cache Poisoning Prevention: A Step-by-Step Attack Breakdown
Here’s how a typical DNS cache poisoning attack unfolds:
- The attacker identifies a vulnerable DNS resolver.
- They send forged DNS responses faster than the legitimate server.
The resolver caches the attacker’s false IP address. - A user enters a legitimate domain name.
- The browser connects to the spoofed IP address.
- The user is unknowingly directed to a fake website controlled by the attacker.
This entire sequence can unfold in seconds, redirecting users to a fake site before traditional defenses even register the threat.
Types of DNS Poisoning Attacks
Common DNS poisoning types include:
- Cache poisoning: injecting fake entries into resolver caches.
- DNS hijacking: altering DNS settings at ISP or router levels.
- ARP spoofing: tricking networks into associating malicious IPs with trusted devices.
All serve to reroute users unnoticed to spoofed sites. When they do, Memcyco’s real-time technology adds the extra-layer fortifications to protect credentials and accounts after users are redirected.
How DNS Poisoning Silently Leads to Phishing and ATO
The redirection sets up phishing:
- Users enter credentials unaware the site is fake.
- Attackers harvest data in real time, enabling account takeover.
- MFA codes, if used, are forwarded and replayed instantly via Man-in-the-Middle (MitM) tactics.
This bypasses many defenses: email filters, link scanners, and network-layer DNS protections that stop at redirection.
The 2025 DNS Threat Landscape by the Numbers
DNS attacks are no longer edge cases. They’re a daily reality for enterprise security teams, and a favorite tactic for phishing campaigns.
As of late 2024, 87% of organizations had reported DNS attacks in the prior year with each incident costing an average of $950,000. Source: Indusface, Dec 2024
While DNS-specific data remains scarce in major enterprise threat reports, recent research is starting to fill the gap. A 2025 academic study analyzing over 690,000 phishing domains found that attackers routinely register domains using cheap or alternative TLDs, with phishing sites often remaining online for over 11 days post-detection – well beyond when most defenses react.
Source: arXiv, “Analyzing DNS Abuse for Phishing Attacks,” Feb 2025
Meanwhile, broader industry reports back the trend:
- Verizon’s 2025 DBIR ranks phishing and pretexting among the top breach causes.
- ENISA (EU’s cybersecurity agency) lists phishing among the top eight threats across EU organizations.
As phishing tactics evolve, the weakest point in the chain is no longer the DNS layer itself, but the moment users interact with what appears to be a trusted site. That’s where visibility matters most.
Bridging the DNS Poisoning Phishing Blind Spot, After User Redirection
DNS manipulation doesn’t just reroute traffic, it reroutes trust. These attacks land users on clone sites with real-looking URLs, padlocks, and no obvious red flags. Once the redirect happens, network-layer defenses go silent.
Memcyco’s real-time solution detects DNS-based phishing attempts after redirection, when other tools stop watching.
- Flags redirected users in real time
- Identifies spoofed domains and suspicious devices
Scrambles stolen credentials using decoy data
- Surfaces victim-level insights before harm is done
Where DNS Protections Stop (and Memcyco Continues)
DNS-layer tools focus on preventing redirection. But once that fails, users are on hostile ground. Memcyco doesn’t replace upstream DNS defenses – it completes them. By infiltrating the attack, it detects phishing as it happens and stops attackers from misusing stolen credentials.
| Before the user lands on a spoofed site |
After the user lands (Memcyco) |
| DNSSEC
Validates DNS responses to prevent cache poisoning before users are affected, but can’t stop attacks once redirection succeeds. |
Memcyco’s ‘Nano Defenders’ Detects phishing sites as they load in the browser after redirection and intervenes in real time to neutralize credential theft. |
| DNS over HTTPS (DoH) or TLS (DoT) Encrypts DNS queries to prevent interception during lookup, but offers no defense after the phishing site loads. |
Optional Red Alerts Displayed in-session, warning users from entering phishing sites that load after DNS resolution. |
| DNS firewall / filtering Blocks access to known malicious domains but often misses new or cleverly disguised phishing sites. |
Decoy credential injection Swaps at-risk credentials – entered on phishing sites – with marked decoy credentials, including disguised phishing sites. |
| Short TTL values for sensitive records Expires poisoned DNS records faster but not fast enough to stop ongoing phishing attacks in real time. |
Suspicious device blocking Blocks suspicious devices attempting unauthorized logins after successful credential harvesting. |
| Regular DNS hygiene audits Reduces misconfigurations and vulnerabilities but can’t detect or respond to active phishing incidents, or who was impacted. |
Real-time victim identification Identifies users exposed to phishing to enable rapid response and remediation. |
Why Memcyco Sees What DNS Tools Can’t
While DNS filtering and threat intelligence help block known domains, phishing sites built on new infrastructure often slip through.
Memcyco doesn’t just defend from the outside, it follows the attack, deploying real-time protections as the scam unfolds. By operating post-redirection, it delivers what network-layer tools can’t: visibility and control at the point of impact.
This attack-side positioning makes all the difference. When the user reaches the fake site, Memcyco is already there, watching, detecting, mitigating.
Start Closing DNS Poisoning Gaps Leading to ATO, with Memcyco
Memcyco doesn’t prevent DNS poisoning itself but stops phishing and damage caused by digital impersonation attacks after redirection.
- Unlock real-time visibility: into attacks, attackers, and each individual victim, detecting, protecting against, and countering scams as they unfold.
- Identify scam victims in real time: pinpoint the exact user redirected by DNS poisoning.
- Deploy marked decoy credentials: that neutralize stolen data, reveal attackers, and block unauthorized account access.
- Identify accounts likely targeted for takeover: using real-time behavioral signals and attack intelligence, enabling preemptive defense before impact.
- Launch Deception Campaigns: that overwhelm attackers with artificial decoy data, disrupting their campaigns.
By focusing on the critical moments after redirection, Memcyco effectively stops phishing and impersonation attacks from achieving their goal: stealing customer data and taking over accounts.
To see how Memcyco compares to traditional tools and newer vendors alike, check out this roundup of top anti-phishing tools 2025.
Book a Memcyco product tour today and discover how to add the long-overdue fortification layer your DNS poisoning defenses have been missing.
FAQs About DNS Poison Attacks
What is a DNS poisoning attack?
DNS poisoning is a cyberattack that corrupts DNS resolver caches with forged responses, redirecting users from legitimate websites to malicious clones. This redirection facilitates phishing campaigns aimed at credential theft and account takeover.
FAQ 2: How to prevent DNS poisoning?
Complete prevention of DNS poisoning requires layered defenses. Network controls like DNSSEC and encrypted DNS protocols (DoH/DoT) help secure DNS resolution. However, since no solution can guarantee full prevention, real-time detection and intervention are essential to detect and disrupt phishing attempts after redirection.
FAQ 3: What are the common types of DNS poisoning attacks?
Typical DNS poisoning techniques include cache poisoning (injecting fake DNS records into resolver caches), DNS hijacking (altering DNS settings at ISPs or routers), and ARP spoofing (tricking networks into misdirecting traffic). All these methods aim to redirect users without detection to phishing sites.
FAQ 4: How does Memcyco detect phishing sites from DNS poisoning?
Memcyco detects phishing sites in real time by monitoring user interactions on the legitimate site. It identifies visits to spoofed, cloned, and phishing sites – including those not yet listed in threat databases – enabling immediate protective actions.
FAQ 5: Can DNS poisoning be fully prevented?
No single measure can fully prevent DNS poisoning. While DNSSEC and other network-level protections reduce risk, attackers continuously evolve tactics. That’s why Memcyco’s real-time fortification layer – that fills post-redirect gaps left by network-level defenses – is critical for preventing ATO fraud resulting from DNS poisoning.