Cybercrime is on the rise, and no one is safe. Not global financial organizations, not small e-commerce businesses, and (obviously) not their customers. And everyone knows it, too.
62% of consumers considered fraud an inevitable risk of shopping online in 2022, and 59% of consumers are more concerned about becoming victims of fraud now than in previous years. As consumers prioritize security over convenience in online shopping and payments, brands will need to invest more in earning and maintaining digital trust.
In 2022, global businesses saw a significant increase in different types of cybercrime. Clickjacking stood out as one of the most worrying attacks, especially on e-commerce websites and financial services, because it is so hard for companies and consumers to detect or prevent it before the damage is done.
The cost and impact of clickjacking fraud are as hard to estimate as they are to detect. However, with almost a third (27.9%) of websites in the US vulnerable to clickjacking attacks, it’s vital that you take steps to prevent these attacks from impacting your website visitors and loyal customers.
What is clickjacking?
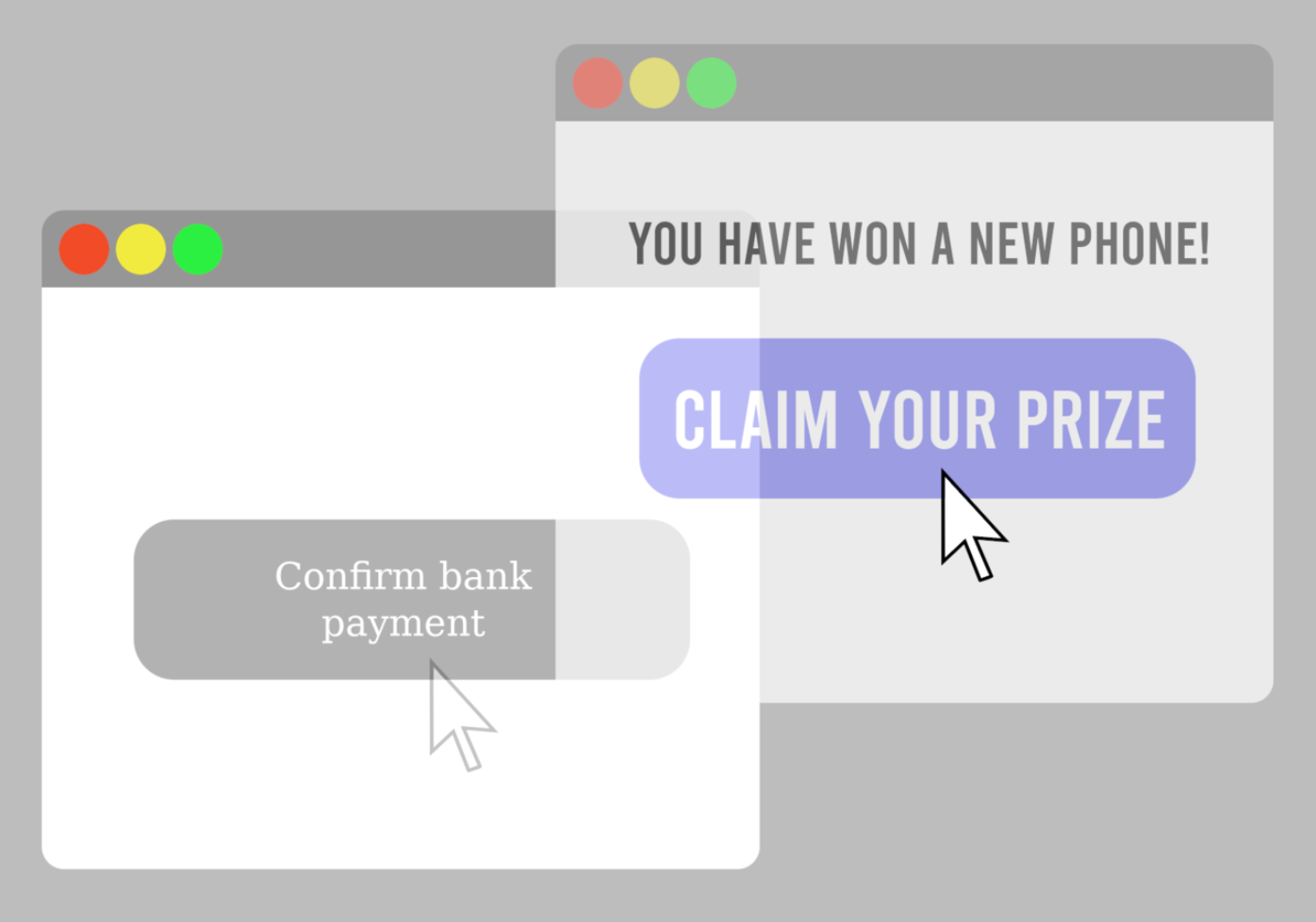
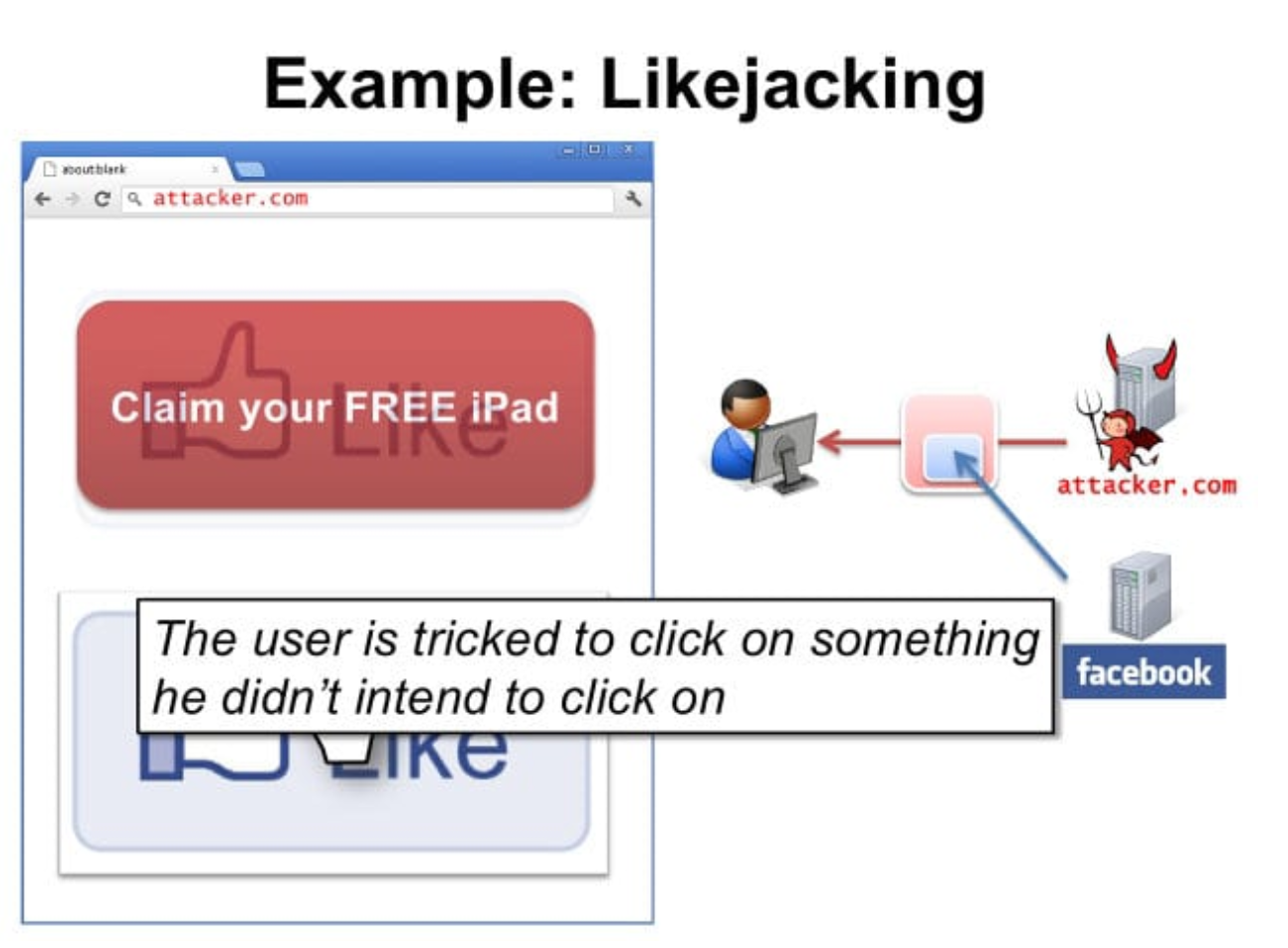
Clickjacking, also known as UI redress, click abduction, or tapjacking (in the context of mobile devices and applications), is a malicious technique for manipulating the behavior of a user on a website and tricking them into performing unintended actions. The most common form of clickjacking employs transparent or hidden hyperlinks over or under legitimate clickable content.
For example, in May 2022, a researcher alerted PayPal of an unpatched flaw that could allow attackers to steal money from users with just one click by employing a simple clickjacking technique. The flaw was quickly patched, and PayPal awarded the researcher a bounty for reporting it.
How does clickjacking work?
It doesn’t take much for a malefactor to execute a clickjacking attack on a website. They don’t need access to the servers or an account on your platform. They only require a bit of CSS and JavaScript knowledge that is freely available online in multiple tutorials and guides.
The “classic” clickjacking attack involving a complete transparent iframe overlay will often look like this:
- The attacker will purchase a domain name or host their code on a free platform. Google Sites is particularly popular with cybercriminals.
- The attacker will use CSS and HTML to create a transparent iframe component to overlay the original and authentic website. The attacked website will then be displayed behind the transparent overlay and look normal to the visitor.
- Using social engineering, such as phishing, the attacker will attempt to get users to visit the fraudulent website. Thinking it is the authentic website of the brand they’ve been redirected to, users can be tricked into performing actions they did not intend. For example, instead of downloading a legitimate PDF document, after clicking the download link, they may instead be redirected to download a malware-infected file.
Cybercriminals’ techniques and approaches evolve over time, and today numerous tactics and types of clickjacking attacks serve the same purpose: tricking users into unintended action.
Cropping
This type of clickjacking attack overlays some of the UI of the original website by “cropping” it and leaving the user with a partial view. For example, the user might see the option to skip a video, but it is hidden with an iframe asking for their email address. The user can still see the original content but cannot interact with it.
Hidden overlay
One of the earliest recorded clickjacking attacks is the hidden overlay or invisible iframe. To execute it, the malefactor creates a 1×1 pixel iframe containing the intended attack and hides it directly beneath the cursor. Since the user cannot see it, they are very likely to click it. Through clever manipulation of divs, JS, and CSS, the malicious link is both invisible to the end user and unavoidable.
Click event dropping
In this attack, the malefactor creates a floating div tag that covers the target UI element completely. Then, by setting the CSS pointer-events property of the top of the page to none, all click events will register on the malicious page rather than the target UI element.
Rapid content replacement
Unlike the previous attack tactics in our list, this one (and the ones below) does not involve an iframe overlay or cropping. Rapid content replacement is a sophisticated tactic that entails automatic and quick content replacement just as the user makes an action. Users cannot detect or prevent this attack as the malicious system allows them to browse the website freely and only launches the attack once it predicts a click event.
Repositioning
The trusted content repositioning attack is an upgrade of the rapid content replacement attack. In this attack, the malefactor moves the UI element directly under the mouse cursor when the user is about to click. This is especially common in games or quizzes where the places users will likely click are easy to predict.
Scrolling
This type of attack uses another approach to hiding the authentic website UI: artificially scrolling off the display area of the target website or UI object. For example, the malefactor may leave the original UI component’s OK and Cancel buttons but hide the dialogue box’s content.
Drag and drop
The last clickjacking attack on our shortlist is not about clicking but rather dragging and dropping. In this case, rather than trying to get the end user to perform a click, the malefactor will try to trick the user into performing a drag operation. For example, instead of dragging an innocent-looking scrollbar, they initiate a drag action of confidential information they entered into a form on the authentic website.
How can you detect clickjacking attacks?
One of the reasons clickjacking attacks are so concerning is that they are notoriously difficult to detect. The only way to discover clickjacking attacks performed against your website is through active inspection of server-side logs to detect suspicious activity patterns and requests.
The majority of tools available today fall short because they can only detect attacks after they’ve been executed and the damage has been done. Though you are unlikely to discover these attacks as they happen, you can be confident that cybercriminals will look for opportunities to launch them and abuse the trust your clients have in your brand. You can use scanning tools to pentest your website regularly for vulnerabilities that enable clickjacking and other types of fraud.
What are the consequences of a clickjacking attack?
Though there are many types of results to clickjacking attacks, the motives are usually financial gain. For the end user, a successful clickjacking attack can result in:
- False product purchasing
- Downloading malware
- Unauthorized transfer of funds
- Hijacking of API tokens
- Stolen credentials
- “Likejacking” on social media to fraudulently grow the audience of a page or account
It’s important to remember that in addition to fraud, clickjacking can be used as part of a larger scheme that may result in identity theft, bullying, “doxing,” stalking, and blackmail.
From the website owner and brand perspective, the damage is harder to predict as it can come from many different sources. Among these sources are:
- Loss of customer trust in the brand
- Marketing budgets lost to clickjacking ad-fraud
- Compromised user accounts that demand immediate attention and remediation
- Increased pressure and workload on website customer service and technical support
8 steps to clickjacking prevention
As noted above, there are tools that you can use to pentest your website against clickjacking attacks. These tools will help you discover server-side vulnerabilities but will not remedy them.
To curb clickjacking fraud on your website, you can take preventative measures on two main fronts: the server side and the client side. It’s worth noting that server-side vulnerabilities are much easier to detect and fix than those on the client side. When it comes to clever deceit and social engineering, there are limited ways to protect your clients from clickjacking.
Server-side clickjacking prevention methods
1. Use the “X-Frame-Options” HTTP response header
The X-frame option is an HTTPS response header that helps protect websites against clickjacking by setting whether a page can render within an iframe.
There are three X-Frame-Options commands that you can use:
- DENY to disallow all sources from displaying your content in a frame
- SAMEORIGIN to allow only the current website to frame its content
- ALLOW-FROM to allow framing on pages hosted on specific URLs
2. Add a Framekiller to the website
Framekilling or framebusting is the practice of including simple JavaScript code in the page source code that supposedly prevents other pages from framing it. This is a very antiquated approach that has proven to be easy to circumvent.
3. Employ a security policy to specify which domains are allowed to frame your pages
One of the approaches on top of OWASP’s list of recommendations for clickjacking prevention is the implementation of a Content Security Policy (CSP) frame-ancestors directive. You can use the frame-ancestors CSP frame directive to instruct the browser to disallow framing from unspecified domains.
4. Keep your system patched
This step is especially relevant for e-commerce websites that use popular frameworks to operate online shopping venues. Malefactors are actively looking for flaws in popular frameworks (WordPress, Marketo, Shopify, and WooCommerce, to name a few) that will enable them to execute clickjacking attacks.
Fortunately, software service providers are relatively quick to patch flaws that affect many of their users (that’s you). Your role is to ensure that the framework and platform your business depends on are up to date and patched for vulnerabilities.
5. Continually check if your website is vulnerable to clickjacking
Pentesting tools are one of the most common ways to check if your website is vulnerable to clickjacking. Alternatively, you can create an HTML page on your machine and try to insert one of your web pages into an iframe. You can go even further to emulate a clickjacking attack by executing code on a different web server.
Client-side clickjacking prevention methods
6. Perform relevant security awareness training
It’s worth starting with the obvious: end-user education. However, making your customers aware of the dangers of clickjacking is a double-edged sword. While making end-users suspicious of being defrauded will make them more vigilant and careful on potentially dangerous websites, it may also have a “phishing fear syndrome” effect when interacting with your authentic communications.
Furthermore, customers often feel that cybersecurity awareness education on behalf of brands and organizations is a way of offloading the responsibility for the attacks onto the victims. Since clickjacking attacks are often sophisticated enough to be completely invisible to the user, training and education can do very little to protect your customer from them.
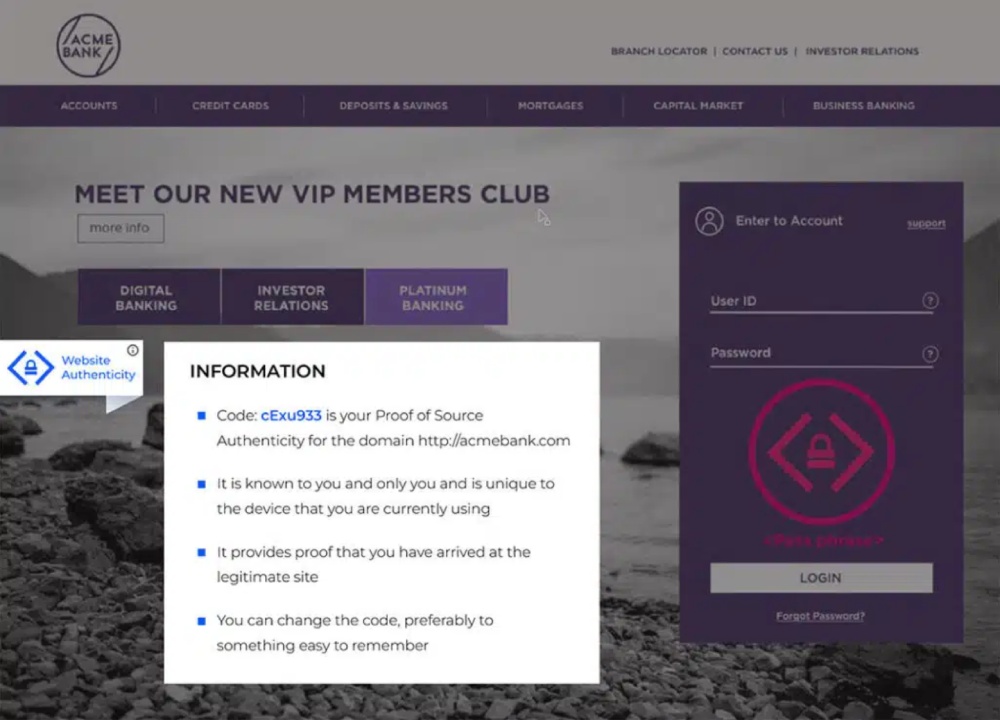
7. Install a website authenticity indicator
When customers log onto your website, they use (at the very least) an account name and password to identify and authenticate their identity. But how can they know that your website is indeed yours? To show your website visitors and clients that the page they see is genuine and unaltered, you can employ Memcyco’s Proof of Source Authenticity (PoSA) interactive watermark.
With the PoSA watermark, you needn’t educate your website’s visitors or customers on how to recognize potential attempts to defraud them. Instead, you’re providing them with a visual means of identifying your authentic website.
8. Employ defensive code in the user interface
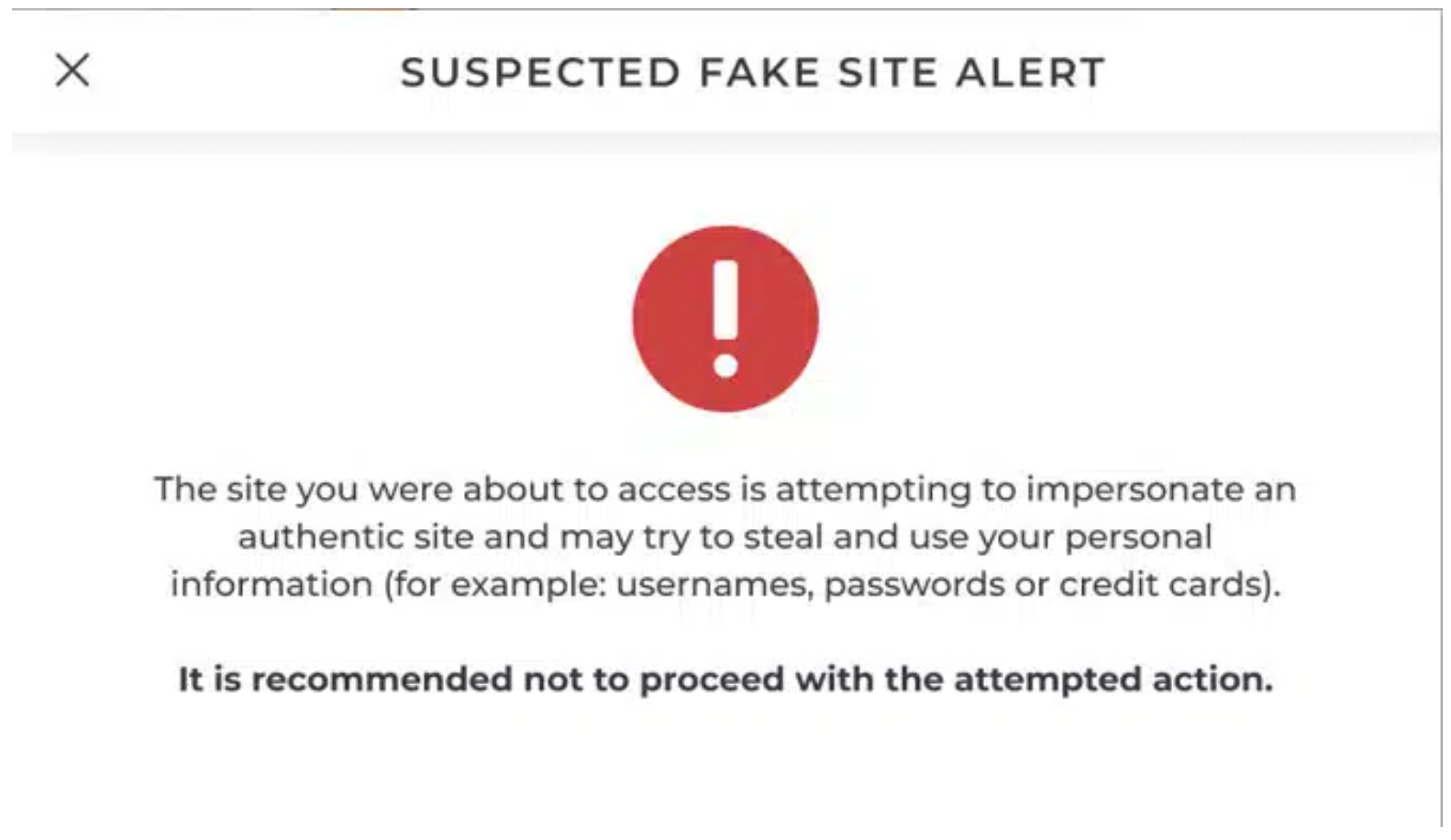
Another feature of the PoSA solution is an integrated behind-the-scenes defensive component in your website infrastructure. With PoSA active on your website, spoofing, cloning, or manipulating its code for clickjacking becomes significantly more challenging for fraudsters.
Among the features hidden in the defensive code is the “Red Alert” warning displayed to users when they are shown an altered or spoofed version of your website.
Unjacking click fraud
Whose job is it to fight cybercrime? In a sense, it’s everyone’s job. For websites and brands that want to curb cyberattacks against their customers, it’s a fairly new and unfamiliar role. Clickjacking is only one of many sophisticated attacks that endanger not just end users but also the hard-earned reputation of brands and e-commerce companies.
Book a demo with our brand protection experts to discover how easy it is to protect your website and visitors against clickjacking and brandjacking threats with Memcyco’s Proof of Source Authenticity (PoSA™) Suite.

















![Directory Traversal Cheat Sheet for 2024 [PDF Download]](https://www.memcyco.com/wp-content/uploads/2023/10/website-post-Thumbnail_-Directory-Traversal-Cheat-Sheet-for-2024-PDF-Download.png)
