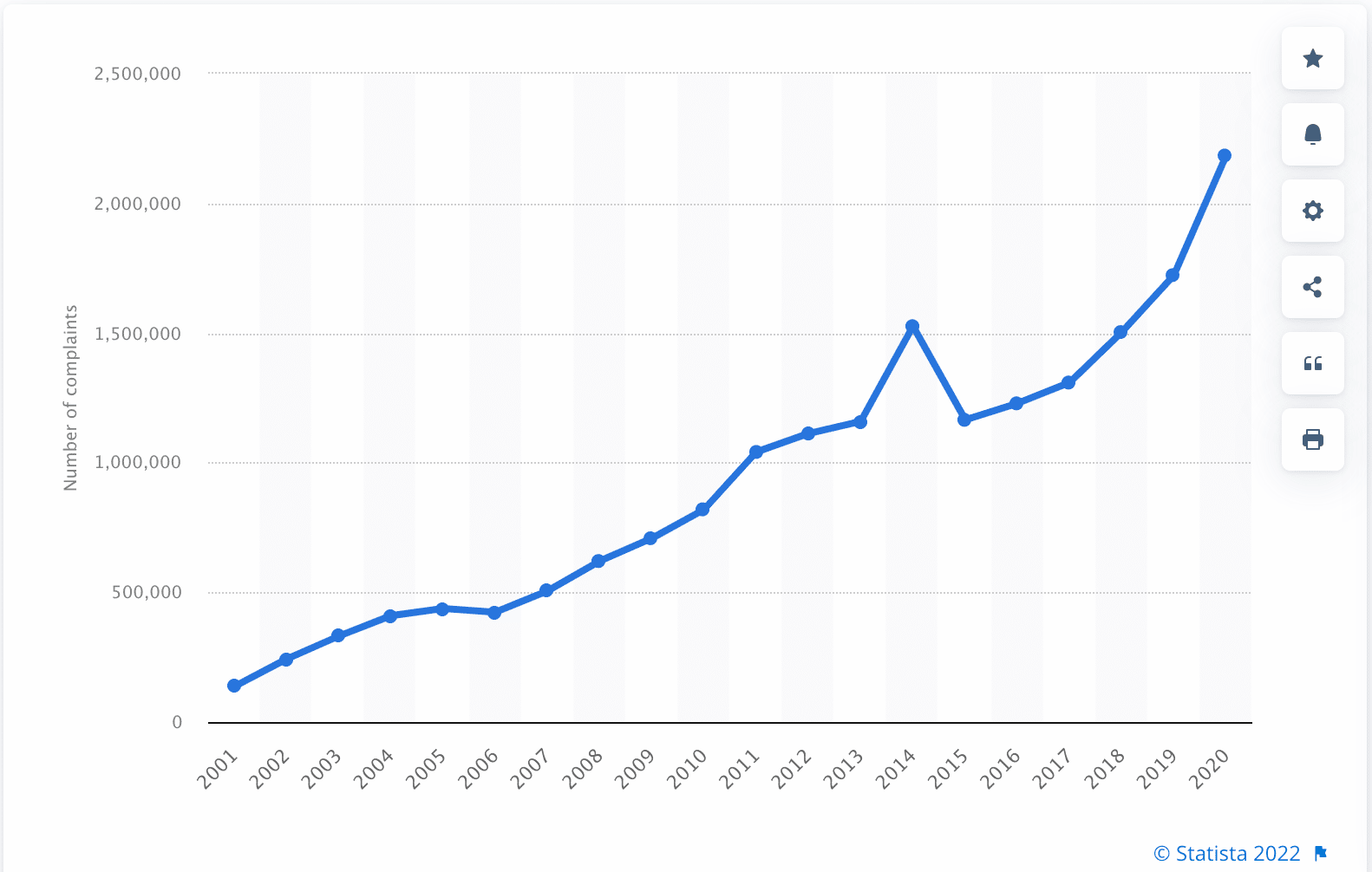
In 2021, consumers reported losing more than $5.8 billion to fraud (a 70% increase from the previous year), mainly due to impostor and online shopping scams. Malware, trojans, identity theft, website impersonation, and data breaches are just a few of the endless methods attackers use to execute such attacks successfully, which means that fraud detection has become critical for any business operating today.
The financial loss caused by fraud hurts not only consumers but also the brands that, unbeknownst to them, lose revenue and trust due to being associated with scams by those who fell victim to them. But fraud detection is no longer sufficient in today’s fast-paced digital world of real-time transactions. Fraud attempts have been increasing steadily for the past twenty years and show no signs of slowing down.
So how can consumer-facing businesses ensure their customers can conduct online transactions on their sites safely without fear of attackers stealing their data and accessing their credit cards?
Consumer fraud complaints with the U.S. Federal Trade Commission (2001 – 2020)
Real-Time Fraud Detection: What It Is And Why You Need It
As the different options for consumers to pay with the click of a button have expanded, attackers have seized on these opportunities with new and improved methods to steal their data and money–including fraud in real-time or at the moment of purchase. This leads us to the differences between traditional and real-time fraud detection.
Traditional fraud detection aims to prevent fraud by having the customer answer questions or enter one-time codes or passwords to verify and confirm an online transaction. However, these methods can be taxing on the user experience and fail to fully protect against certain types of fraud, such as website impersonation.
Real-time fraud detection, in contrast, leverages machine learning algorithms to detect suspicious online behavior associated with fraud as they happen, adding no friction for the customer.
For example, when customers make a purchase from an eCommerce site or users log in to their bank accounts, real-time fraud detection identifies if a credit card purchase falls into the range of normal activity or anomalous behavior based on things such as that person’s history of activities and location. Something similar happens when hackers are cloning a website (which is where most significant fraud occurs). Real-time fraud detection happens at the point of impact, meaning that if an anomalous behavior occurs then the security solution must warn both the organization and the user immediately.
This significant advance in fraud detection is possible as storage space for data has become more affordable and processing time has gotten faster, empowering algorithms to process and analyze behavioral data at scale, very quickly. Real-time fraud detection takes place in milliseconds, which is much more suitable for stopping attackers at the point of payment.
For example, what happens if a user follows a fake eCommerce link that leads to an identical-looking fake website? Memcyco detects it at the point of impact to warn the user of what just happened before it’s too late.
“Torture the data, and it will confess to everything.” — Ronald Coase, the Nobel Memorial Prize in Economic Sciences winner in 1991.
The Most Common Types of Online Fraud
As transactions between businesses and customers moved online, fraud attempts and detection mechanisms have followed suit. Some of the most common types of fraud in e-commerce, finance, and online payments include:
Spoofing:
Attackers attempt to send emails on behalf of a company, or a target domain, using deception to appear as another person or business.
Impersonation:
Attackers use fake websites that look and feel like a well-known brand to lure customers into revealing sensitive data, transact with them, or infect a company’s infrastructure with malware.
Cloning:
Cybercriminals succeed at taking over a brand’s website or corporate email address and copy or “clone” it to phish sensitive information such as credit card numbers from victims.
Account takeover:
Fraudsters gain access to corporate accounts that do not belong to them, alter information within the account, and then successfully gain control of the account to use it for making non-authorized transactions.
Business email compromise:
Attackers use emails of C-level or other high-level employees to attempt to wire funds directly to the attacker’s account.

As a result of increasing online fraud, companies are losing customers’ trust. Already 80% of people hesitate to click on links because they suspect the site, email, or SMS may be fake. How can we revert this trend and create a world where businesses and customers can interact online without fear?
4 Methods to Protect Your Online Shoppers
From website landing pages to ads and emails, companies today need a way to verify their digital assets at every point of their communication with customers. Memcyco’s PoSA™ (Proof of Source Authenticity) solution combines a patented digital watermark with a real-time fraud detection and alert system.
It gives users the highest level of trust they need to ensure that the websites they visit are authentic, whether they access them directly or via links in emails, text messages, or scanning QR codes. The solution provides instant trust for users at the exact point of impact between brands and end-users, so they know that all websites and correspondence are all from your brand (emails, text, and websites).
In addition to monitoring, it delivers full visibility to both security teams and customers with a detailed report that details the scope of the damage (such as how much was stolen from the victim during a successful attack) and categorizes the attacks by type (e.g., imposter site attack, imposter/end-user profiling, reverse engineering, and spoofing). The reports also detail the number of victims affected by each attack, location, and names.
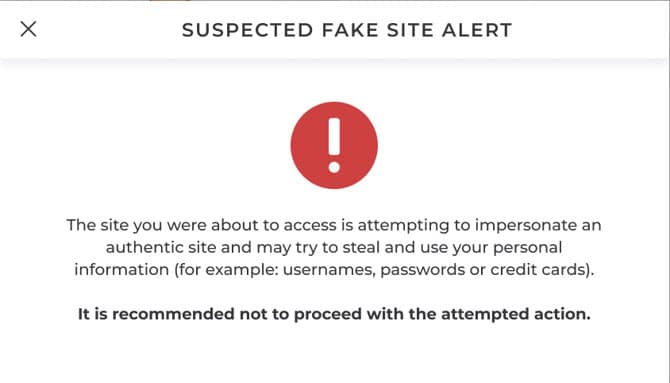
Here are a few of the methods it uses to protect online shoppers:
1. Real-time unknown workstation detection:
Alerts users at the moment they arrive at a cloned or copied website trying to impersonate a major trust brand before they enter their sensitive information, such as passwords, codes, credit card information, and more.
2. Multiple credentials attempt detection:
Detects attempts at ATO (account takeover), where malicious threat actors successfully enter an account of a major brand to make unauthorized transactions and alerts security teams to multiple login attempts in real time.
3. Reverse-engineering alerts:
One of the first steps in website impersonation is to copy the website code. PoSA™ alerts security teams whenever a user attempts to open developer tools on the website code–a forewarning of possible attempts to impersonate their brand. Brands can choose to hide all client-code/logic from the eye of the user by encrypting it.
4. Red alert to end-users on impostor site attack:
Since PoSA™ runs in select mode and monitors activity at user endpoints of the brand’s site, it also alerts customers of attempted attacks. This means it takes a proactive approach to phishing and counterfeit sites, keeping users from accessing fake sites in the first place and blocking access from untrusted devices.
Protecting Online Shoppers in Real-time
Although brands may have traditionally relied on fraud detection services, these methods are not enough to defend them against fraudsters’ new and evolving malicious attempts. With increasing ways for customers to purchase and transact instantly, real-time fraud detection is critical. Responding to this need with its combined detection and alerts system and digital watermark, Memyco’s PoSA™ can be deployed without any need for coding or software installation. The brand need only insert the code on the HTML file of their website to reap the rewards, while their end users do not need to install anything at all to benefit from the solution by default. In just a few minutes, your organization can have strong and secure proof of website and communication authenticity to protect your users against imposters in real time.
Want to learn more about Memcyco’s Proof of Source (PoSA™) Identity solution? Download the datasheet here.