Memcyco Blog
Get the latest insights and protect your business and your customers from website spoofing fraud.
“Your entire company network was compromised, all through a single login.”
That’s the reality of an employee single sign-on (SSO) breach nightmare. Hackers create fake SSO login pages in order to steal employee credentials, which can literally give them “the keys to the kingdom” – access to the most sensitive data of the organization. From a disgruntled ex-employee to a compromised user, it can become a devastating security hole. It happens more than you think.
A recent report showed that 74% of all breaches are attributed to the human element, with the most common causes including the use of stolen credentials and privilege misuse. These massive security risks demand proactive action—that’s where User Access Reviews (UARs) come in.
Ensuring that only authorized users can access sensitive data and systems helps reduce identity-based cyber threats and safeguard your organization’s data, customers, and reputation. To protect your business, you’ll need a strategy combining strong UAR practices with a customized template to help protect against attacks targeted at your employees’ SSO credentials.
What is a user access review template, and why do you need it?
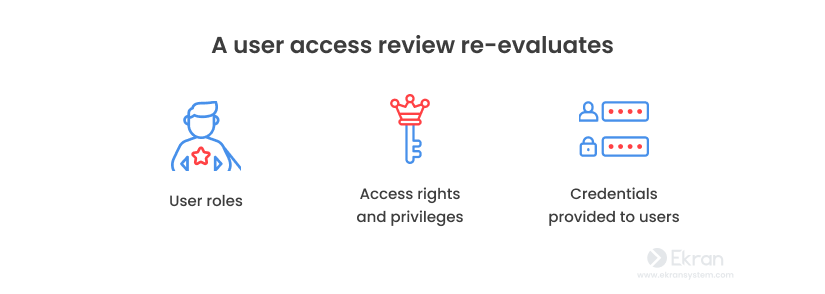
A user access review is a systematic process of periodically evaluating the access rights granted to individuals for various computer systems, networks, applications, and data within an organization. It’s a security audit for digital privileges that analyzes whether users still require the access they currently have and minimizes unnecessary access that creates potential vulnerabilities.
Regular UARs are your best proactive measure for uncovering overlooked vulnerabilities such as permission creep – a phenomenon that occurs when employee roles change, but temporary access lingers. These forgotten permissions become easy entry points for intentional or accidental breaches, and attackers can exploit them for initial access,
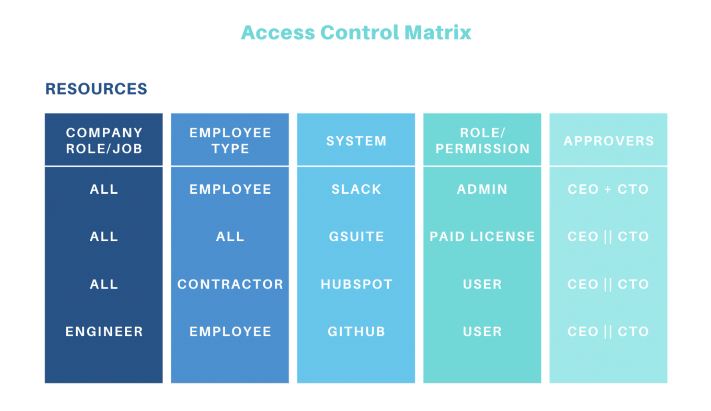
The user access review template is a document that provides a structured framework for this process. It helps minimize unnecessary risk, maintain tight security, and meet mandated regulatory compliance like SOC, GDPR, HIPAA, and NIST. A well-designed template streamlines UARs, giving you irrefutable evidence of secure security practices.
Source
Who is the user access review template for?
A user access review template isn’t just for passive reporting—it’s for those proactively driving a secure, risk-minimized infrastructure. Here are the key stakeholders that benefit from a user access review template:
- Identity and Access Management (IAM) Administrators: UAR templates help IAM administrators simplify workflows and boost overall security by helping to identify areas where access needs fine-tuning, revocation, or stricter monitoring.
- Security Analysts/Engineers (within SOC Teams): can proactively use UAR templates to uncover threats caused by privilege creep, dormant accounts, and misconfigured permissions. They can quickly assess the security implications of access settings.
- Vulnerability Management Specialists: use UAR templates to pinpoint prime targets for exploitation, highlighting accounts with excessive or outdated privileges. Templates also help prioritize risk mitigation and streamline remediation efforts.
- Information Security Officers and CISOs: employ UAR templates to support strategic decision-making and promote a responsible security posture. Using templates also demonstrates compliance and proactive risk management while easing audit processes with a clear history of access reviews.
What are the benefits of a user access review template?
Discovery of Your Hidden Risks
Forget random spot-checking. A well-structured UAR template gives you a comprehensive, repeatable snapshot of all permissions in place. Factors like dormant accounts, outdated access rights, forgotten privilege escalations, and mishandled credentials in a secrets manager all become risk points.
Clarity for Prioritization
Some permissions require immediate remediation, others less so. Your template should categorize potential risks with a focus on impact. It’s more than identifying issues; it’s about knowing what to fix when limited resources are a reality.
Proactivity Leading to Improvement
A robust user access review template can help you achieve more than identifying overly broad privileges. The proactive approach allows you to improve in several areas, including:
- Reducing security breach likelihood and impact – Regularly reviewing and removing unnecessary access minimizes potential entry points and the attack surface available to malicious actors.
- Shifting your security strategy – Rather than scrambling after a breach, you have clear indicators of weak points that require attention, such as internal permission creep or the risks of compromised employee SSO credentials.
- Audit Preparation – Thorough, template-driven reviews create audit trails to prove continuous assessment and remediation of your access landscape.
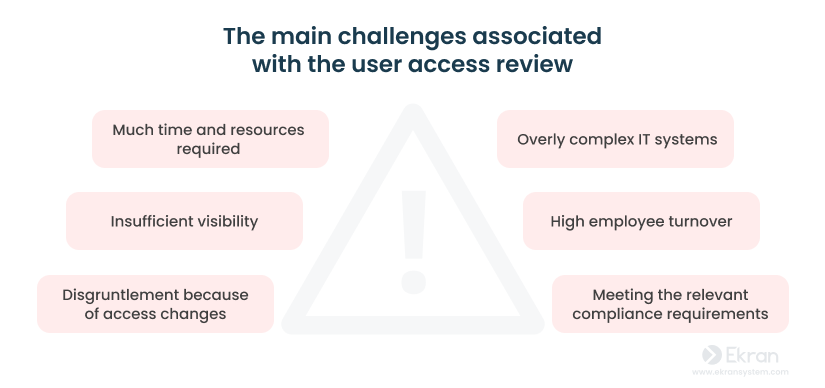
What are the challenges of the user access review process?
UARs are a crucial security tool, but their successful execution can sabotaged by:
Data Sprawl, Including SSO Permissions
Modern IT environments with cloud applications and legacy systems have dispersed user permission schemes. Understanding the risks in this disjointed landscape is crucial for a thorough UAR. Inconsistent data handling standards or accidental exposure jeopardize the trust you’ve established.
Lack of Centralization
The organizational adoption of SaaS often results in fragmented access rights management, limiting visibility and hindering effective user access reviews. Achieving consistency and oversight requires a centralized approach to regain control over permissions, regardless of where SaaS applications reside.
Source
Resource Bottlenecks
Manually conducting UARs is time-consuming. Implementing a DevSecOps Maturity Model (DSOMM) with automation tools increases the efficiency of UARs and frees up security team resources. DSOMM creates space for in-depth reviews that significantly elevate your security posture.
The Need to Meet Regulatory Mandates
Many regulations (such as GDPR and HIPAA) emphasize the importance of user access reviews. Your process must meet their requirements for robust compliance, including comprehensive audit preparedness.
Audit-Readiness Stress
Rushed, sporadic reviews often lead to reduced quality of the documented procedures and evidence of rigor that auditors demand. A methodical UAR cycle demonstrates control over access, maximizing trust during compliance audits.
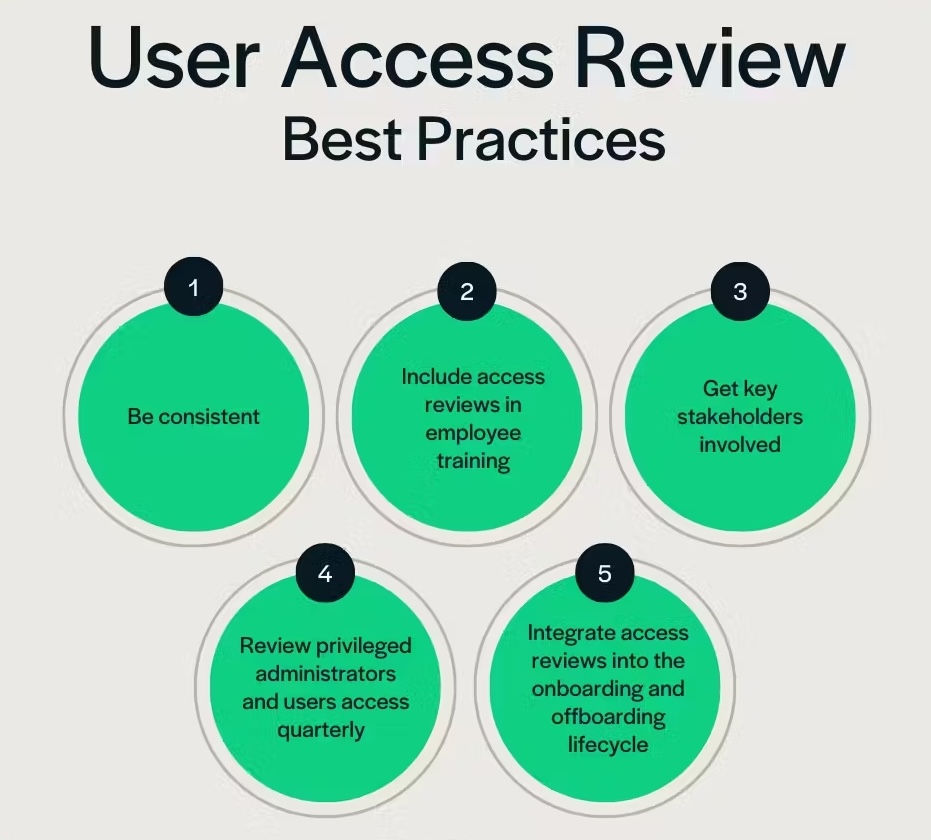
6 Essential Best Practices for User Access Reviews
A well-structured User Access Review process is essential to achieving a strong security posture. The following nine foundational tactics set the stage for a risk mitigation tool that delivers both proactive protection and compliance confidence:
1. Establish Clear Ownership
Designate accountability, ensuring every layer of your human firewall—from those performing reviews to those driving remediation—has clear responsibilities. Determine escalation points to avoid ambiguity or paralysis.
2. Define Your Review Scope
Full UARs at high frequency can become unsustainable. Choose an initial depth (per system, per app, etc.) that suits your environment and balances practicality with thoroughness.

Source
3. Prioritize Based on Risk
Target high-value assets, access to sensitive data, and accounts at higher risk (frequent job changes, broad privilege sets). Don’t treat all systems and users as equal.
4. Leverage UAR Templates and Tools
Reduce manual review effort and speed analysis by choosing dedicated audit tools, scripts, or a user access review template to minimize reliance on raw data combing.
Pre-defined user access review templates improve data quality, guide decision-making, and aid comparison between cycles to track progress in reducing risk. They help you track approvals, actions, and the reasoning for decisions regarding permissions. Using a template aids in preparation for compliance audits while streamlining UARs over time.
5. Adopt the Principle of Least Privilege
Enforce a culture where users have only the minimal access level required to perform their job functions. The Principle of Least Privilege substantially reduces the potential attack surface and the impact of accidental or malicious misuse of permissions.
6. Detect and Respond to SSO Credential Abuse
While UARs are vital for managing internal permissions, attackers increasingly focus on stealing and misusing valid employee SSO credentials. These attacks can happen through phishing, credential leaks, or disgruntled ex-employees.
To effectively detect and respond to SSO credential abuse, organizations should focus on a streamlined approach that includes:
- Anomaly Detection: Utilize User Behavior Analytics (UBA) and threshold alerts to identify unusual login patterns or multiple failed login attempts.
- Leveraging AI: Employ artificial intelligence and machine learning for predictive analysis and to automate threat responses, reducing the attacker’s window of opportunity.
- Enhanced Security Measures: Implement Multi-Factor Authentication (MFA) and enforce regular password changes to strengthen credential security.
- Regular Security Assessments: Conduct vulnerability assessments and penetration testing to identify and mitigate potential attack vectors.
- Employee Training: Provide ongoing cybersecurity awareness training and conduct simulated phishing exercises to enhance staff awareness and preparedness.
- Incident Response Planning: Develop and regularly update a comprehensive incident response plan, including swift actions to contain and resolve incidents.
- Threat Intelligence Sharing: Participate in industry forums to exchange information on emerging threats and best practices.
- Secure Session Management: Implement session timeout policies and monitor active sessions for signs of unauthorized access.
- Enhanced Privilege Escalation Monitoring – Using Privileged Access Management designed for automated tracking of access rights across diverse platforms can offer a detailed view of potentially inappropriate permissions increases and alert your security team for fast investigation and potential corrective actions.
Protect Your Website from Unauthorized Access
The hidden cracks in your access landscape can expose your organization to breaches from leaked data due to forgotten permissions or to attackers using stolen employee credentials on spoofed SSO login pages.
User access reviews driven by a comprehensive template are a crucial step in reducing identity-based cyber attacks.