Enterprises searching for proactive cybersecurity tools are looking for one essential outcome: stop scams before they result in credential theft, account takeover, or financial loss. This outcome is critically important because the financial stakes for failure are at an all-time high: according to IBM, the average cost of a data breach involving stolen or compromised credentials is a staggering $4.44M according
Businesses already invest heavily in takedown services, MFA, email filtering, fraud scoring, and threat intelligence, yet sophisticated scams still succeed. Why? Because most of these tools intervene only after a user has already engaged with a fake website or malicious flow. True proactivity is not early detection after damage has begun, but interception before compromise occurs. This marks the difference between expensive cleanup and true prevention.
What are proactive cybersecurity tools?
Proactive cybersecurity tools prevent compromise before credentials or sensitive data are exposed. Instead of triggering alerts once fraud is already underway, these solutions identify scam activity in real time, protect targeted users during authentication, and block unauthorised access attempts before an account is misused.
Why reactive security fails against modern scams
Most cyberfraud tool stacks are built to trigger only after a user has been deceived. Takedown services work after a phishing site has already stolen credentials. Threat feeds update after attackers have begun harvesting data. MFA alerts after a login attempt is already performed. Even fraud engines typically analyze behavior post-login, which means the attacker has already gained access. The defense begins too late in the kill chain, and the damage is already unfolding.
The high frequency of successful attacks confirms the failure of this reactive model. A 2024 report by Abnormal Security found that a shocking 83% of security professionals reported their organization was hit by an Account Takeover (ATO) attack at least once in the past year. This widespread failure demonstrates that the existing defense layers – designed for detection – are insufficient against modern scams designed for prevention bypass.
Related reading: What Domain Takedown Services Miss & How to Close Gaps
How enterprises should evaluate proactive cybersecurity tools
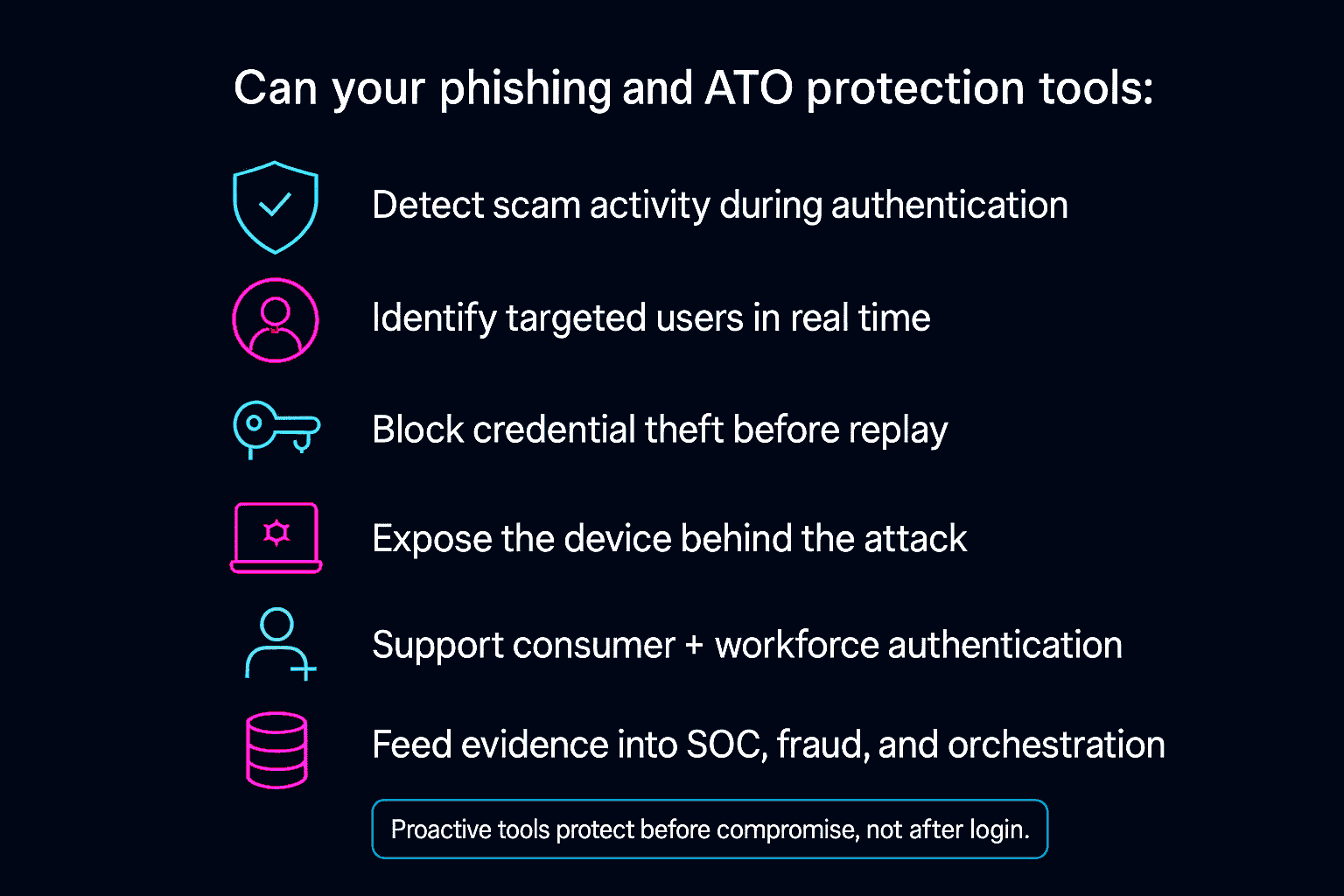
Proactive cybersecurity tools stop scams before damage occurs by detecting malicious activity during authentication, identifying targeted users and attacking devices in real time, and preventing credential theft or account takeover before access is granted.
To prevent scams before they cause damage, tools must provide visibility and control at the moment of interaction, rather than after compromise. The following criteria define genuine proactivity:
- Detect scam-related activity during authentication, not after login
- Identify targeted users in real time, not just the existence of an attack
- Block credential theft before credentials can be replayed
- Expose the device behind the attack, not only the IP or network origin
- Support both consumer and workforce authentication flows
- Feed incident evidence into fraud, SOC, and security orchestration systems
Related Reading: Advanced Device Fingerprinting for ATO Fraud Prevention
Beyond simply meeting the checklist, a genuinely proactive tool must offer high-fidelity signals that integrate seamlessly into existing security operations. For instance, exposing the device behind the attack is vital because attackers often rotate IPs, use VPNs, or compromise residential proxies, making IP blocking ineffective. The best proactive cybersecurity tools provide a persistent identifier for the attacking device itself.
Also, the ability to support both consumer and workforce authentication flows ensures a unified security posture across the entire digital estate, from customer-facing portals to internal VPNs and SaaS applications. When evaluating, demand evidence that the solution works before a user enters their final credential, making the difference between prevention and post-compromise detection.
Related Reading: Phishing Site Detection & Takedown: What to Look For
The Business Case: Quantifying the ROI of Prevention
The shift from reactive security to true proactivity is not just a technological upgrade, it is a critical business strategy with a measurable return on investment. The cost of an account takeover is exponentially higher than the cost of prevention. When a scam succeeds, enterprises incur direct financial losses from fraud, chargebacks, and regulatory fines, but the indirect costs often outweigh the direct ones.
Each successful scam generates a cascade of avoidable expenses: customer support time spent on account recovery, internal investigation hours for security and fraud teams, and mandatory compliance reporting. By stopping scams at the point of interaction, organisations drastically reduce the volume of compromised accounts. This leads to fewer customer support tickets, a lower burden on SOC analysts, and a clear reduction in brand and reputational damage.
Prevention removes the cycle of continuous cleanup and instead builds sustained resilience, allowing teams to redirect their time toward strategic risk management rather than constant incident response. The efficiency gained from eliminating repeat scams and reducing investigative workload is one of the most significant financial benefits of proactive defence.
The most effective proactive cybersecurity tools for scam prevention today
The following categories represent the tools that can meaningfully prevent scam-driven compromise. Each is defined by where it acts relative to the attack.
Website impersonation and phishing interception platforms
These tools detect when users are redirected to or interact with fraudulent websites, helping protect customers from cloned login pages and fake recovery flows. Their strength lies in identifying impersonation campaigns in real time rather than waiting for user reports.
Real-time login and session-integrity solutions
These platforms analyse authentication flows for signals that indicate scam involvement, such as suspicious referral sources, unusual device context, or replayed credentials. Their value is in preventing access before the attacker reaches the account dashboard.
Device analytics for high-risk login attempts
Device-context-based risk decisions offer higher fidelity than IP-based checks. They allow enterprises to identify devices involved in credential theft, stuffing, or brute-force activity, even when the IP changes, VPNs are used, or location appears normal.
Deception-based scam disruption
These solutions introduce decoys and controlled data that reveal attacker intent and infrastructure. They prevent criminals from using stolen credentials successfully and create evidence for fraud, SOC, and threat-hunting teams.
Mobile authentication protection
Scam interception is no longer only a web problem. Mobile-specific protection tools detect risky logins and credential replay attempts coming through apps, helping enterprises maintain continuity of protection across channels.
Where proactive tools outperform traditional fraud prevention
| Reactive model | Proactive model |
| Detects after compromise | Prevents credential theft at point of interaction |
| Blocks login attempts after takeover | Blocks malicious attempts during authentication |
| Depends on behavioural analysis post-login | Depends on real-time signals during authentication |
| Limited visibility into individual victims | Full visibility into targeted users and attack devices |
| Useful for investigation | Useful for prevention |
The business impact of this shift is measurable: fewer compromised accounts, fewer customer support investigations, reduced fraud loss exposure, and faster incident resolution.
How to select the right proactive cybersecurity tool
A technology is genuinely proactive if it can answer yes to the following questions:
- Can it detect scam-originated interactions before credentials are stolen?
- Can it identify which individual users are being targeted in real time?
- Can it prevent credential replay attacks rather than flag them after login?
- Can it expose the device behind the attack to support escalation and blocking?
- Can it provide evidence that helps fraud, SOC, and security analysts act quickly?
Tools that do not meet these criteria will continue to allow scams to succeed even if they claim to be proactive.
Where Memcyco fits into the proactive stack
One category in this landscape focuses specifically on real-time scam interception, protecting customers and employees by detecting impersonation activity and credential theft attempts during authentication. This is the space where Memcyco operates. Memcyco’s preemptive cybersecurity platform provides enterprises with visibility into targeted users and attacking devices in real time, blocks credential theft attempts before misuse, and enriches fraud, SOC, and risk systems with actionable evidence. It closes the gap where most scams succeed: the moment a user unknowingly interacts with an attacker.
Read the case study: How Memcyco Helped a Global Bank Slash ATOs by 65%
Final thought: Proactive tools are great. But proactive tools that act when it counts are better
The question is not whether you’re leveraging a solution that claims to be proactive. The question is whether it can detect the telltale signs and act early enough to stop scams before credentials are stolen or accounts are accessed.
If security tools begin working only after a user has already interacted with a scam, the defence is already late. True proactivity means detecting and blocking malicious activity during authentication before credentials are stolen or accounts are accessed. The organisations that shift to this model reduce fraud risk, protect customers and employees, and gain earlier visibility into attackers and victims across digital channels.
Related Reading:
- How to Run a Domain Spoofing Check & Stop Fake Sites
- Why Website Cloning Attacks Evade Brand Protection (and How to Stop Them)
- How To Prevent Loyalty Account Takeovers in Real Time
FAQs
What are proactive cybersecurity tools?
They are technologies that prevent compromise before credentials, data, or account access are provided to attackers.
Do proactive security tools replace MFA?
No. MFA protects access, while proactive tools prevent credential theft and scam-initiated login attempts before authentication takes place.
Can proactive cybersecurity stop phishing scams?
Yes, when visibility and control happen during authentication rather than after a login attempt or fraud event.
How long does it take to implement proactive scam-interception tools?
Implementation varies by vendor, but modern solutions typically take days rather than months.
Is proactive cybersecurity better than reactive cybersecurity?
It is not a replacement, but it prevents the most damaging part of a scam: credential theft and account takeover.



















