The missing link in root cause analysis
Fraud analysts know the pattern too well. After an account takeover incident, the postmortem confirms what happened. A stolen credential was used. A bot executed a replay. A mule account attempted a transfer. Yet the origin of the compromise remains unclear.
The postmortem becomes an autopsy on a loss that already occurred.
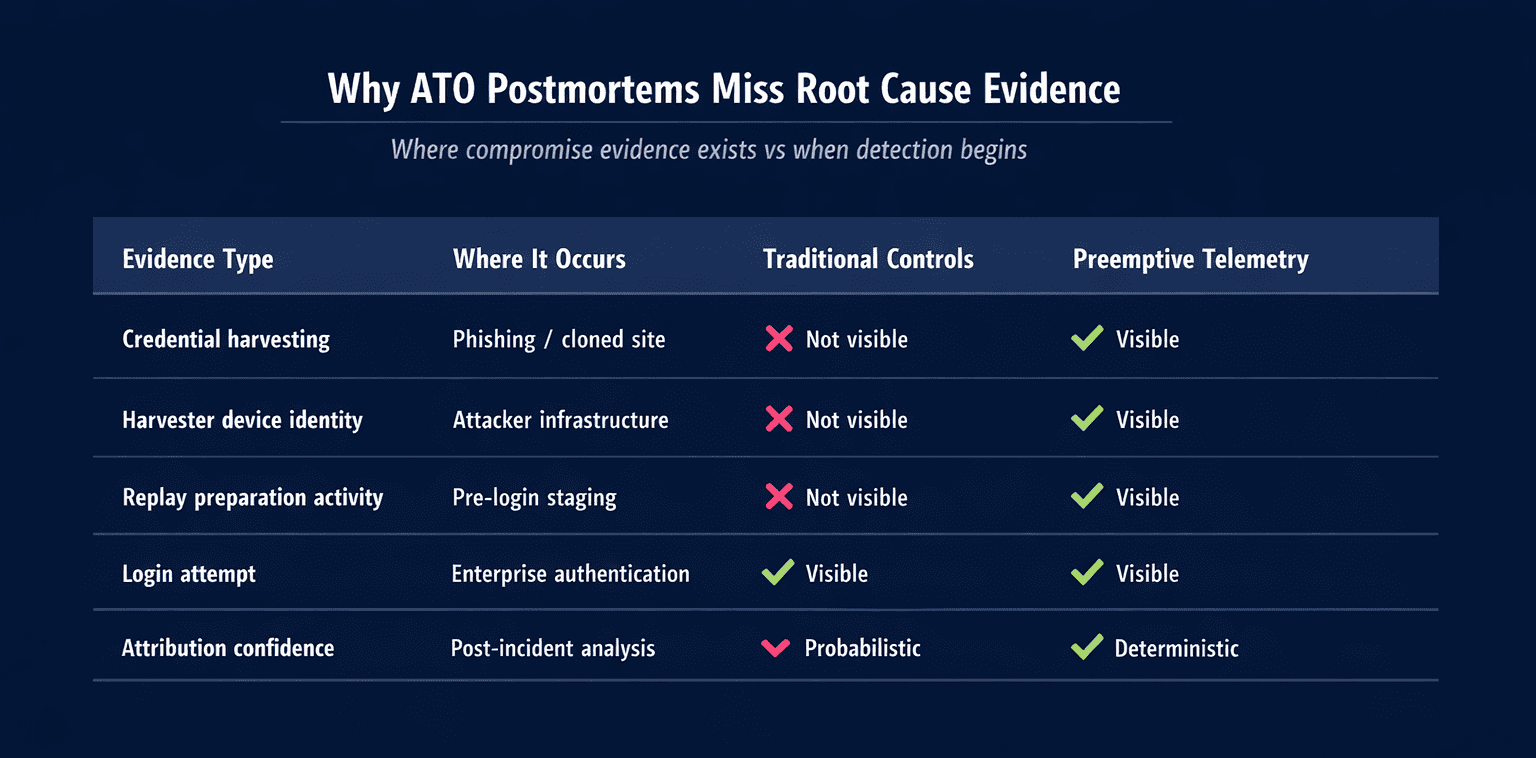
The core issue is the Window of Exposure. This is the period between the moment a phishing or cloned site goes live and the moment those harvested credentials are used against the real service. Every hour inside this window erases critical evidence that could reveal attacker behavior and the initial point of compromise. More on this exposure gap can be found in our guide on account takeover (ATO).
Traditional incident response waits until the attacker reaches your login page. By then, the blind spot has already consumed the most valuable forensic signals.
The blind spot: why firewall logs are not enough
Most account takeover fraud prevention programs still start at the perimeter. Teams examine login errors, velocity spikes, device mismatches, and behavioral anomalies. These insights are useful, but they all share the same flaw. They only appear once the attacker is already in execution mode.
From the adversary’s perspective, reconnaissance and harvesting are the decisive phases. Once those succeed, replay attempts are easy. As we detail in the guide to website spoofing, this is precisely where most organizations lack visibility.
When the attack finally hits your firewall, the attacker has already won the opening half of the kill chain. This is the blind spot: the lack of insight into upstream compromise activity. It limits postmortems to describing the symptom, not the source.
Shift left: gaining forensics from the phishing site
Closing this blind spot demands telemetry from the attacker’s environment, not only your own.
Preemptive telemetry captures activity inside cloned pages and lookalike domains. Instead of waiting for an ATO attempt, teams gather intelligence at the moment adversaries interact with the fake site. This includes device ID, IP behaviors, harvesting patterns, and kit fingerprints. For reference, see how Memcyco detects digital impersonation in real time.
This inside-out visibility turns phishing infrastructure into a forensic asset. Analysts can correlate recurring device DNA with broader campaigns. Our research on website cloning attacks illustrates how repeated kit signatures expose organized criminal groups.
Early intelligence like this transforms incident response. Instead of asking where stolen credentials came from, teams know the exact clone, timestamp, and device responsible.
What lessons can be learned from improving account takeover fraud detection after incidents?
Traditional post-incident analysis is probabilistic. Analysts infer intent based on suspicious sequences. Useful, but incomplete. Preemptive intelligence turns fraud analysis deterministic.
Decoy data as conclusive evidence
Injecting marked or decoy credentials into cloned environments ensures that when those credentials surface later, they serve as proof. This creates a verified link between the harvesting event and the login attempt. It is the foundation of Memcyco’s real-time ATO prevention methodology.
The result: postmortems shift from we think this was an attacker to we know exactly who harvested this credential and when.
Tuning risk logic with zero false positives
Deterministic attacker fingerprints feed directly into risk engines. Because the signals come from confirmed malicious behavior, rules can be tightened without fear of false positives.
This is one of the key advantages of browser-based detection and real-time protection models. They offer evidence, not guesswork.
Risk logic becomes sharper, lighter on customers, and focused entirely on verified threats.
The preemptive postmortem
Postmortems can no longer be backward-looking summaries of damage. With preemptive telemetry, they become forward-looking intelligence reports that analyze attacks neutralized before they ever reached the customer.
The operating model must shift from measuring dwell time to tracking Time to Detect Clone and Time to Intercept Harvesting. Both metrics appear throughout our state of digital impersonation fraud report and serve as early indicators of operational maturity.
Preemptive postmortems do more than improve detection. They redefine what an incident is, and more importantly, when it begins.
Stop performing autopsies. Start preventing attacks.
Preemptive telemetry gives your fraud and SOC teams the upstream visibility legacy tools cannot deliver. See how Memcyco provides real-time detection of cloned sites, deterministic attacker attribution, and ATO prevention that operates before login attempts ever occur.
Protect your digital ecosystem with real-time impersonation defense
Frequently asked questions
1. How does preemptive telemetry improve account takeover fraud prevention?
Preemptive telemetry captures attacker signals at the moment a phishing or cloned site becomes active. This gives fraud and SOC teams evidence about harvesting activity long before a login attempt occurs, allowing prevention rather than downstream mitigation.
2. What types of attacker data can be collected from cloned or spoofed sites?
Teams can gather device fingerprints, IP intelligence, interaction patterns, harvesting behavior, and phishing kit signatures. This intelligence forms the basis for deterministic attribution and more accurate risk scoring.
3. How does decoy data help confirm attacker activity?
Decoy or marked credentials are injected into cloned environments. When an attacker later attempts to use those credentials, it provides conclusive proof of malicious intent. This eliminates guesswork and accelerates investigations.
4. Why are traditional firewall and login-based signals insufficient for modern ATO detection?
Perimeter signals appear only after attackers complete reconnaissance and harvesting phases. By the time an ATO attempt reaches the authentication endpoint, critical forensic evidence has already been lost, creating a significant blind spot.
5. How can organizations operationalize preemptive postmortems?
Organizations should measure Time to Detect Clone, integrate deterministic signals into SIEM or SOAR workflows, and tune risk logic using confirmed attacker fingerprints. These steps convert postmortems from reactive reports to proactive intelligence cycles.