Account takeover prevention for credit unions has reached an inflection point. One concept underpins most modern failures: the timing gap, the period between a member engaging with a scam or impersonation interaction and the moment a security or fraud team becomes aware of risk. During this gap, access is often treated as legitimate even though compromise has already occurred. Despite stronger authentication, broader adoption of multifactor authentication (MFA), and growing fraud budgets, account takeover attacks continue to rise. The reason is not a lack of controls. It is a misunderstanding of when those controls engage relative to how modern attacks actually unfold.
Most account takeover (ATO) incidents begin long before a transaction is attempted or an alert is triggered. By the time traditional defenses respond, the compromise has already occurred. Understanding this timing gap is the key to preventing ATO attacks in 2026. Most security teams recognize this pattern instinctively, even if their tools do not.
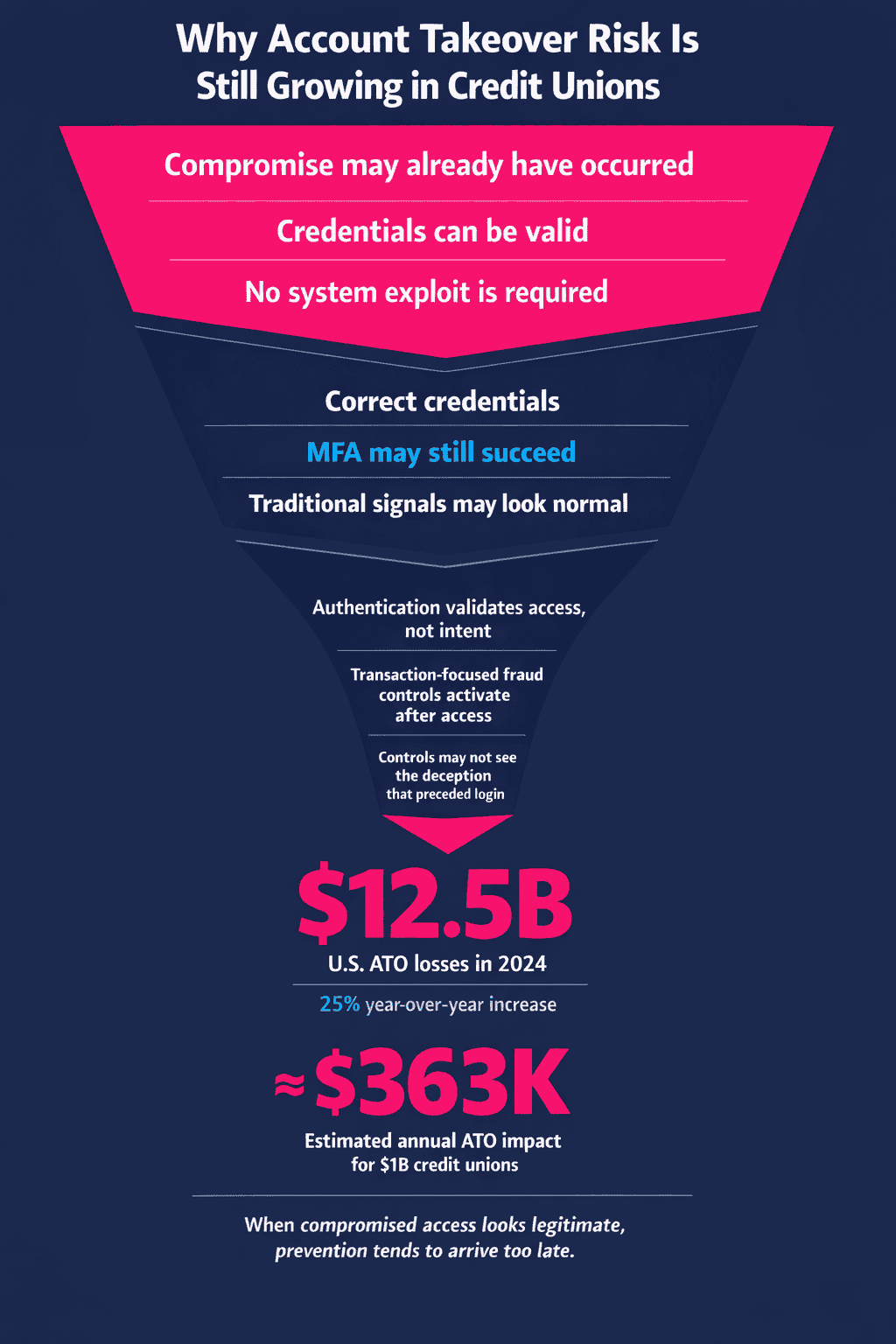
Why Account Takeover Risk Is Still Growing in Credit Unions
Credit unions face a unique combination of pressures. Member trust is central to the relationship. Digital channels are expanding faster than security teams can retool. At the same time, attackers are no longer trying to break into systems – they are deceiving users into handing access over voluntarily. That shift changes what “prevention” actually means.
Account takeover fraud in credit unions is now dominated by scam-driven attacks, including phishing and impersonation. High-fidelity impersonation sites, cloned login pages, and automated phishing kits allow attackers to harvest valid credentials at scale. These credentials are then reused immediately, often before the member realizes anything is wrong.
Overall U.S. ATO losses hit $12.5 billion in 2024, marking a 25% year-over-year surge, with credit unions reporting seven-figure incidents from social engineering alone, according to national trade association, America’s Credit Unions.
From the system’s point of view, the login looks legitimate, even though the access itself may already be compromised. To a fraud team reviewing logs later, it often looks legitimate too. The credentials are correct. MFA challenges are completed. Traditional signals offer little reason to intervene
According to Allure Security’s 2025 report on ATO fraud, credit unions can see revenue losses of up to 11% from ATO; for a credit union with $1 billion in assets, this is illustrated as roughly $363,000 in lost revenue per year.
Fundamentally, these attacks follow the same account takeover patterns explained in our breakdown of how most modern ATO fraud occurs, but manifest differently in different scenarios.
The Defense Gap Most Account Takeover Strategies Miss
Most ATO strategies assume the attacker’s challenge is authentication. That assumption feels reasonable, until you look at how these attacks actually unfold.
The attack happens outside the enterprise
Credential harvesting often occurs on fake domains and impersonating pages that sit entirely outside the credit union’s environment. There is no malware, no exploit, and no perimeter breach to detect.
Login controls validate access, not intent
MFA confirms that a user can complete a challenge. It does not indicate whether credentials were entered freely, harvested minutes earlier, or replayed as part of a scam-driven workflow.
Fraud detection engages after access
Transaction monitoring and behavioral analytics are designed to detect misuse. They activate only after access has already been treated as legitimate. At that point, prevention has given way to response.
This misalignment explains why many well-defended credit unions still experience successful account takeovers.
Scanning and takedown sees only the symptoms
Scanning and takedown services are useful for dismantling scam infrastructure, but often it’s temporary with phishing sites often reappearing under a different domain. Additionally, scanning and takedown offers no attack insight or user protection while users are being lured.
For a deeper look at why traditional brand protection and takedown strategies still leave institutions exposed during active scams, read: What Domain Takedown Services Miss and How to Close the Gap
What Actually Needs to Be Detected Earlier
Effective account takeover prevention for credit unions depends on recognizing signals that appear before access is treated as legitimate.
Scam-driven credential harvesting
Modern phishing campaigns replicate real credit union sites with precision. Credentials entered on these pages are immediately usable elsewhere.
Credential replay attacks
Attackers reuse stolen credentials at speed, often pairing them with real-time MFA relay techniques. The goal is not persistence, but rapid access.
Suspicious device and session context
The risk signal is often tied to the device and session attempting to authenticate, especially when linked to prior phishing interactions or known scam patterns.
Preventing scam-driven account takeover requires visibility into these moments, not just the final login event.
For a technical breakdown of how earlier signals surface during authentication rather than after compromise, see: How Browser-Level Signals Help Prevent Credential Stuffing Attacks
Why Legacy MFA Alone Cannot Stop Account Takeover Attacks
Legacy MFA methods such as SMS codes, one-time passwords, and push-based approvals remain important safeguards, but they are not designed to detect deception. Most credit unions already recognize this, which is why MFA adoption has been so widespread.
These methods verify that a user can complete an authentication challenge. They do not indicate whether credentials were compromised moments earlier through phishing or whether an attacker is replaying them in real time as part of a scam-driven workflow. When authentication success is treated as proof of legitimacy, access is trusted too early and attackers can pass through controls without resistance.
This is not a failure of MFA as a concept. It is a limitation of what legacy MFA was built to do.
Why doesn’t MFA stop account takeover attacks?
MFA verifies that a user can complete an authentication challenge, but it does not indicate whether credentials were stolen moments earlier through phishing. When attackers replay valid credentials and MFA codes in real time, authentication succe eds and access is treated as legitimate rather than suspicious.
Learn more about the how attackers exploit MFA, and how to fortify authentication without adding user friction in our guide: MFA Isn’t Enough: How Attackers Bypass Authentication and What Actually Stops Account Takeovers
Reframing Fraud Detection in the Context of ATO
Authentication standards such as FIDO2 passkeys significantly reduce credential theft risk and represent an important step forward. However, contrary to popular belief, FIDO2 passkeys do not eliminate impersonation-driven account takeover entirely. Device enrollment, account recovery flows, session hijacking, and network-level deception can still create windows where unauthorized access occurs without user awareness.
Many teams search for fraud detection tools for credit unions when addressing account takeover. This creates confusion. It is an understandable confusion, but an important one to clear up.
Fraud detection systems are optimized for transactions. They identify anomalous behavior after access is granted. Account takeover prevention requires controls that operate earlier, during the transition from deception to authentication.
Already using FIDO2 passkeys? Find out why passkeys aren’t phishing-proof, and the fortification layer required to ensure that they are, in our 5-page report: FIDO2 ‘Passwordless’ Authentication: Ending Credential Phishing?
What Effective ATO Prevention Looks Like in Practice
Preventing account takeover in 2026 is less about adding controls and more about placing them correctly.
Effective strategies share several characteristics:
- Visibility into scam and impersonation interactions that precede login
- Detection of stolen or replayed credentials during authentication
- Session and device risk awareness tied to known scam behavior
- Targeted blocking that stops attackers without disrupting legitimate members
This approach reduces downstream fraud exposure while minimizing false positives and operational burden.
Where Memcyco Addresses the Account Takeover Gap
Up to this point, the challenge has been structural rather than vendor-specific. That distinction matters, because no single control fixes a timing problem.
Memcyco’s preemptive solution addresses the timing gap that traditional ATO defenses leave exposed by focusing on scam-driven account takeover attempts as they transition back to the genuine site. Rather than relying on post-login or transaction-stage signals, it surfaces risk during authentication, before access is treated as legitimate, when stolen or replayed credentials are first reused.
This approach does not replace, but rather compliments, modern authentication initiatives such as multifactor authentication that becomes selectively applied rather than universal, and FIDO2 passkeys that aren’t ‘phishing proof’ as the market hype suggests.
In short, Memcyco provides real-time visibility and intervention for attack paths that occur before, around, or despite authentication, reducing the number of incidents that downstream fraud systems are forced to handle.
Why This Shift Matters for Credit Unions
Credit unions operate on long-term trust. Excessive friction, account lockouts, or delayed response erode that trust quickly.
Earlier intervention delivers tangible benefits:
- Fewer unnecessary member lockouts
- Reduced investigation volume for SOC and fraud teams
- Lower downstream fraud exposure
- Faster containment during phishing waves
Account takeover prevention that engages earlier strengthens both security posture and member experience.
Account Takeover Prevention Is a Now a Timing Problem
Account takeover prevention for credit unions in 2026 and beyond will not be defined by stronger passwords, more MFA prompts, or heavier transaction models. It will be defined by when protection engages.
In practice, that means protecting members in real time while they are being deceived, and as long as their stolen credentials are able to be used for account takeover – not after stolen access is already treated as normal behavior.
As long as defenses wait for login completion or transaction intent, attackers will remain one step ahead. Shifting protection earlier in the attack lifecycle is the only way to close the gap without increasing friction or operational cost.
What to Ask When Evaluating Your ATO Strategy
It is worth asking a harder question. If your ATO strategy begins at login or ends at transaction monitoring, you are already reacting.
The harder question is whether you can detect and stop account takeover while members are interacting with scams, before access is treated as legitimate.
FAQs
How do credit unions prevent account takeover attacks?
By detecting scam-driven credential theft and stopping credential replay attempts during authentication, before fraud detection systems engage.
What causes account takeover in credit unions?
Most incidents originate from scams and credential harvesting, including phishing and impersonation, not password guessing or system breaches.
Why doesn’t MFA stop account takeover?
MFA confirms possession, not intent. It cannot identify when valid credentials are being replayed after phishing.
How can credit unions detect account takeover earlier?
By monitoring authentication-stage signals linked to scam activity, including credential misuse and suspicious device sessions.
What is credential replay in account takeover attacks?
Credential replay occurs when attackers reuse stolen credentials and authentication codes to access legitimate accounts without triggering traditional alerts.



















