Cybersecurity teams are under immense pressure in 2024. They need to be more efficient than ever to stay ahead of evolving threats. This means embracing new technologies, strategies, and frameworks. One powerful tool in their arsenal is the threat intelligence lifecycle—a vital but challenging aspect of proactive cyber defense.
Forward-thinking enterprises understand the value of a structured approach to threat intelligence. Surveys show that 72% of businesses now use a formal threat intelligence lifecycle model. Why? Because it helps them stay ahead of cyberattacks that could lead to expensive data breaches or crippling service outages.
Creating and maintaining an effective cyber threat intelligence program requires an in-depth understanding of the threat intelligence lifecycle and its stages.
What is the threat intelligence lifecycle, and why is it important?
The threat intelligence lifecycle, sometimes called the cyber threat intelligence (CTI) lifecycle, is the structured and continuous process of producing actionable cyber threat intelligence from raw data by processing and analyzing it. This iterative cycle, usually designed and overseen by CISOs, empowers SecOps and CTI analyst teams to forecast, detect, and respond to potential risks and threats to the organization’s overall security posture.
The base for the threat intelligence lifecycle model is guidelines and recommendations from national cybersecurity organizations like NIST and CTI industry experts. This model can be instrumental in planning and designing your own CTI processes for gathering, analyzing, and distributing threat intelligence insights to relevant stakeholders in the organization in a way that enables them to defend against rising cyber threats proactively.
The threat intelligence lifecycle is an ongoing process, rather than one with a beginning and end, and should be implemented as part of your overall CTI strategy.

Who benefits from the threat intelligence lifecycle?
The threat intelligence lifecycle is a foundational framework that empowers many organizational stakeholders, regardless of a company’s overall cybersecurity maturity. Here’s who it benefits and how:
SOC and InfoSec Teams
- Enhances threat detection capabilities through the use of cutting-edge threat intelligence tools and platforms
- Expedites threat response with automated remediation and clear, detailed reports on the attack scope
- Provides practical and relevant suggestions at the right time which makes the difference between successfully defending against a threat and dealing with a costly data breach.
Fraud and Risk Teams
-
- Provides Fraud and Risk teams with a continuous stream of real-time threat data that can be directly integrated into fraud risk engines, enhancing their ability to detect and prevent fraudulent activity. For example, information about stolen credentials or new account takeover tactics can be used to update fraud rules and filters in real-time, proactively stopping fraudulent transactions.
- Shares threat intelligence across departments fosters better communication and collaboration between Fraud and Risk teams and other areas of the business, such as customer service. By being aware of emerging threats and potential attack vectors, these teams can proactively prepare for increased fraudulent activity and take preventative measures. For instance, knowledge of a data breach can prompt customer service teams to warn customers about potential phishing attempts or unauthorized account access attempts.
- Empowers Fraud and Risk teams to conduct more thorough due diligence and create more accurate risk assessments by understanding the latest fraud tactics and attacker behaviors. This intelligence allows them to identify vulnerabilities in the organization’s systems and processes, ultimately strengthening their overall fraud prevention posture.
Business Leaders
- Proactively prepares businesses for sophisticated and spear-targeted threats by identifying vulnerabilities and implementing mitigation strategies before attacks occur.
This benefit is especially valuable for large organizations and financial institutions facing website spoofing or attempts to infiltrate company systems through impersonation attacks on single sign-on (SSO) login pages.
Everyone
Security teams, IT staff, department heads, and even non-technical employees (who can be targeted in social engineering attacks) gain access to contextual and actionable insights that guide decision-making across the organization, helping create cyber resilience and bolstering your human firewall.
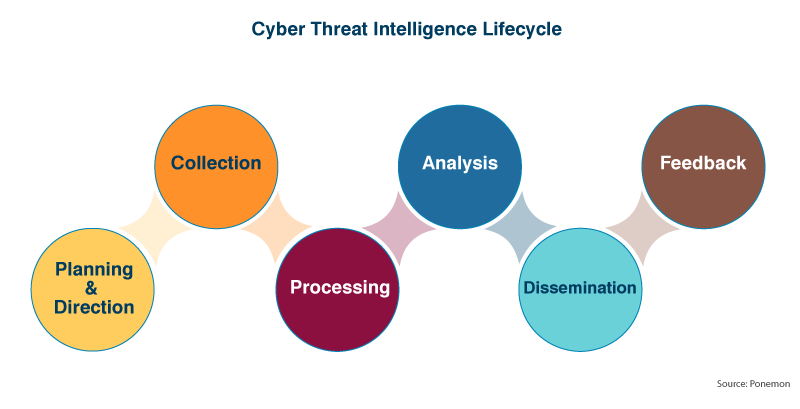
The 6 Stages of the Threat Intelligence Lifecycle
1. Direction and Planning
The threat intelligence lifecycle consists of six distinct and iterative stages. Before launching a successful CTI operation, security teams need a comprehensive plan. This plan is the foundation for your entire effort—it sets the direction, identifies key players, and outlines the specific threats you’ll be targeting.
Here’s a breakdown of the planning process:
1.1 Identifying Threats and Risks
- Risk Assessment: This involves analyzing potential threats to understand the likelihood and potential damage they could cause.
- Prioritization: Not all threats are created equal. Use scoring and prioritization methods to identify your organization’s most critical risks.
1.2 Building Your Team
Identify key stakeholders and personnel who need to be involved in the CTI operation, including security analysts, fraud managers, IT staff, and even business leaders.
1.3 Defining the Scope and Timeline
- Scope: Determine the extent of your operation. Will you focus on a specific department, system, or type of threat?
- Timeline: Estimate the duration of your initial CTI lifecycle iteration (the gathering, analysis, and action phases).
1.4 Aligning with Business Goals
- Business Risk Management: To maximize effectiveness, ensure your CTI plan aligns with your organization’s overall risk management objectives.
- Attack Surface: When defining your plan, consider your entire attack surface (all the potential entry points for threats).
By creating a well-defined plan, you’ll be setting your CTI operation up for success. This plan will direct your team throughout the threat intelligence lifecycle, ensuring you focus on your organization’s most critical threats.
2. Collection and Compilation
With the requirements and direction planned out, you can gather all the information relevant to the specific goals and objectives you’ve set. This process will include data from internal sources (like network traffic logs and metadata) and external sources (such as commercial or community-maintained threat intelligence feeds).
Depending on the availability of data sources and the scope of your CTI operation, collecting and compiling the data may entail:
- Exporting relevant metadata and logs from organizational cybersecurity systems, relevant networks, cloud services, and other security tools you may employ; then importing data from these sources to the SOC’s TI / command and control system.
- Gaining access to intelligence feeds and databases, including open source intelligence (OSINT) tools and commercial threat intelligence.
- Scanning the Internet and the Dark Web for relevant data, such as leaked organizational credentials or assets.
- Interviewing and consulting industry experts and cybersecurity service providers for targeted information about the threats and vulnerabilities you will address in your CTI operation.
The key challenge at this phase is gathering as much relevant information as possible without creating an overwhelming mass of potentially irrelevant information or data.
To streamline the data collection process, security teams often employ threat intelligence platforms and automated security data consolidation tools to offload much of the manual work in this stage onto automation scripts and solutions.
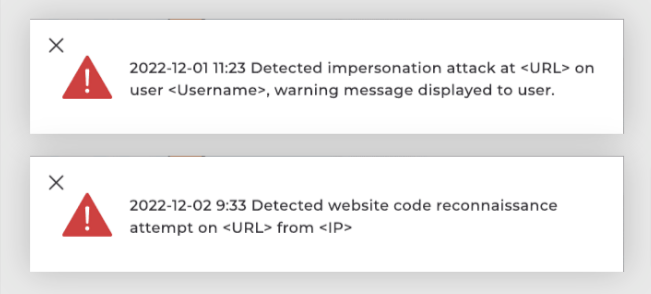
Enhanced with proprietary algorithms, Memcyco’s digital risk protection solution helps you recognize website impersonation attacks in real-time while providing detailed intelligence about every attack, including contextualized forensics, attack blast area, magnitude, and impact on individual attack victims—all while offering full protection from these attacks during the ‘window of exposure’ (the time between when the fake site is up, and until it is down) and beyond. This is the critical difference between Memcyco and other TI solutions in the case of website impersonation.
3. Processing
The data and intelligence information you’ve collected are not yet suitable for analysis, so in this stage, the data is organized, verified, cleaned, and formatted.
The processing phase of your threat intelligence lifecycle will typically involve:
- Removing irrelevant or false data to clean your data of garbage and correct any inaccuracies.
- Converting, structuring, normalizing, and contextualizing the data so it can be stored in data repositories and fed into threat intelligence analysis software tools.
- Verifying the validity and legitimacy of the data. For example, information from Dark Web forums that has yet to be recognized or verified by any threat intelligence vendors or communities may not be considered a very reliable data source for your CTI operation.
To speed up and improve the processing of vast data stores, professionals today employ NLP and AI/ML tools to extract valuable information and prepare it for analysis.
4. Analysis and Review
This stage transforms raw data into intelligence that CTI professionals can analyze and turn into actionable recommendations for relevant stakeholders.
Some of the aspects addressed in this phase include:
- Adversary profiling to gain insight into potential attackers’ intentions, motivations, and capabilities
- Behavioral analysis to uncover trends and patterns that are indicative of adversarial activity on your digital assets
- Threat correlation to contextualize the various factors, security gaps, and potential implications of a successful breach by adversaries
There are numerous tools and structured analytical techniques that you can employ at this stage of the threat intelligence lifecycle, but the resulting product should ideally be a set of clear instructions and recommendations to guide decision-making and stakeholders.
5. Dissemination and Sharing
With your cyber threat intelligence insights ready for consumption, you can customize and tailor your analysis results to suit the target audiences you’ve outlined for your operation.
During this phase, you should ensure the secure and optimal distribution of pertinent findings to enable collaboration and practical actions addressing the issues in your report. You can employ dashboards, presentations, briefings, and even Slack messages or email templates to share cyber threat intelligence with stakeholders promptly and clearly.
For example, a list of relevant vulnerabilities in your organization’s third-party software may be appropriate for the InfoSec teams but irrelevant for C-suite executives.
6. Feedback and Continuous Improvement
The feedback stage is often the least enjoyed by CTI teams and experts. While frequently neglected, this vital stage enhances the effectiveness of your CTI program and can help ensure that your CTI operations add value to the organization.
This phase entails collecting feedback from the stakeholders you shared your intelligence insights with and understanding how to improve your threat intelligence lifecycle to enable them to make informed decisions.
Suggested feedback to gather from your target audiences includes:
- The level or relevance of the intelligence shared in terms of actionability and timing.
- What other stakeholders should be involved, and what should be excluded from future CTI lifecycle iterations?
- Was the quantity and frequency of the intelligence delivered suitable and effective?
The feedback stage also entails establishing and measuring key performance indicators (KPIs) and metrics to assess the effectiveness of your CTI program. It’s also a critical stage in helping determine the direction and requirements for the next iteration of your threat intelligence lifecycle.
Get Unified Website Threat Intelligence & Impersonation Protection with Memcyco
The threat intelligence lifecycle is an ongoing, iterative process with six stages designed to produce actionable cyber threat intelligence tailored to your organization’s unique risk profile. Throughout this process, the right tools can streamline workflows and boost efficiency.
Memcyco’s unique real-time digital impersonation protection solution bolsters the threat intelligence lifecycle by enriching your data collection with previously unavailable data (such as information on individual victims and targets of such attacks) for more accurate analysis and forecasting. Using innovative schemes like its ‘nano defender’ technology, Memcyco detects fake sites and protects your customers from the dangers of website impersonation attacks and account takeover scams.
Contact Memcyco to discover how our intelligent, agentless, real-time solution can transform your website threat intelligence lifecycle.