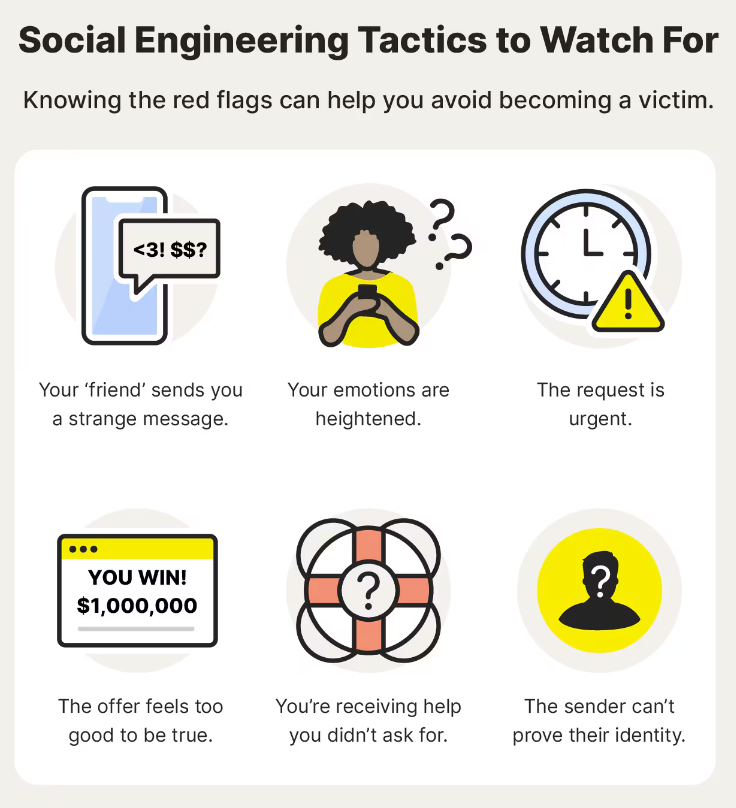
Imagine arriving at work one day only to find that your organization’s critical data is now in the hands of cyber attackers. When major companies like OpenSea and MailChimp fall victim to such attacks, resulting in the loss of millions of dollars and the exposure of thousands of users’ private data, one must wonder: am I next?
That’s highly likely, considering that over 963,000 unique phishing sites were detected globally in the first quarter of 2024. Phishing techniques are also increasingly diversified, from deepfakes to whaling and smishing. Understanding phishing attack techniques and the tools that can help prevent them is critical, as organizations of all sizes are equally at risk.
What Are Anti-Phishing Tools and How Do They Work?
Anti-phishing tools protect individuals and organizations from phishing attacks by automatically identifying and blocking suspicious activity, links, attachments, and messages. Here are some common anti-phishing tools categories:
1. Email filters
Email filtering solutions analyze multiple aspects of an email, such as sender, subject line, content, attachments, and embedded links, to identify threats, mark suspicious emails as spam, and delete or block them.
2. Anti-virus software
This software can help to identify and block malicious attachments or links in emails that lead to phishing websites. It uses signature-based detection to match known threats and heuristics to identify new, unknown threats. It can also scan incoming emails for malware that bad actors may use in phishing attacks.
3. Authentication solutions
Authentication solutions like multifactor authentication (MFA) promise an extra layer of security against phishing attacks by requiring users to provide two forms of identification, such as a password and an SMS code or biometrics. SMS-based MFA sends a unique code to the user’s phone, making it harder for attackers to access accounts. Additionally, passwordless authentication eliminates passwords, using biometrics or push notifications, reducing the risk of phishing and credential theft.
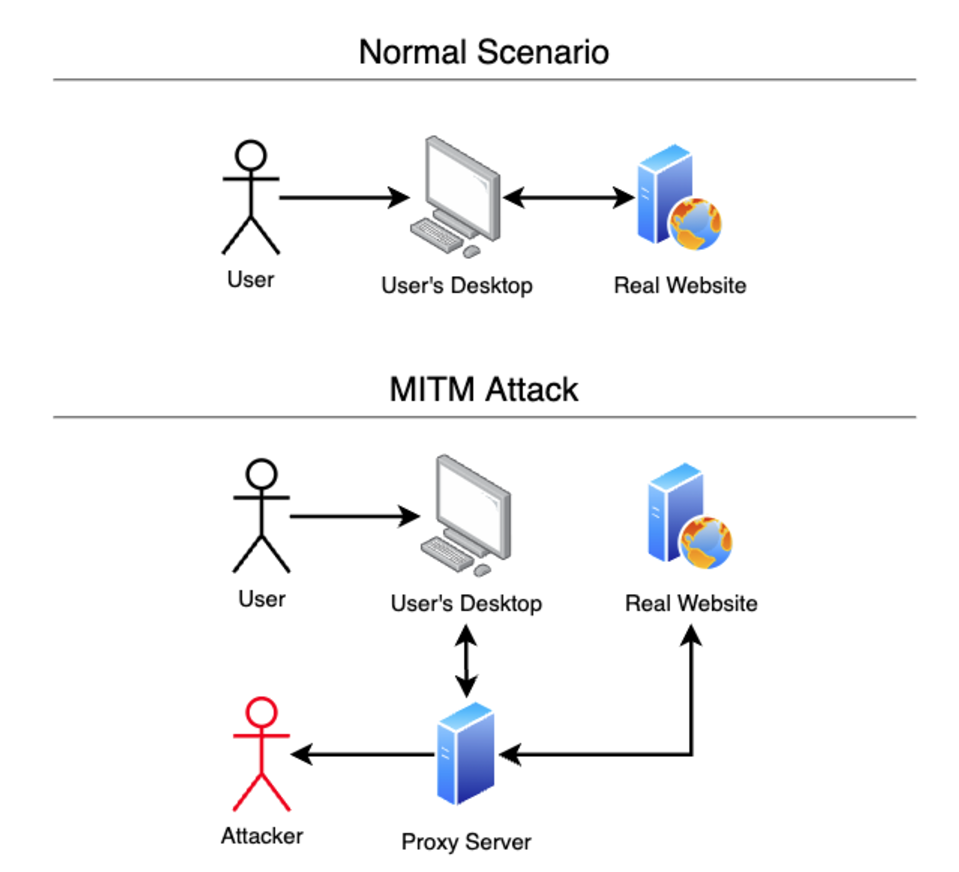
Despite being incredibly common, MFA remains vulnerable to man-in-the-middle attacks (MitM), which can bypass it using various techniques. Customers may not even be aware of MFA bypass events and may not report incidents, limiting the implicated organization to damage control after prevention is no longer possible.
Scam-prone industries are turning to pre-emptive solutions that add proactive real-time safeguards to reduce incidents and related expenses to combat MFA bypass.
4. Browser Extensions
Browser extensions use databases of known phishing sites and heuristics to analyze websites in real-time and determine if they’re safe to visit. They warn users when they navigate a potentially malicious site so they can exit it before entering sensitive information, making a fraudulent transaction, clicking on a malicious link, or downloading a suspicious attachment.
5. Firewalls
Firewalls control network traffic and prevent unauthorized access to a network. You can configure them to block incoming and outgoing traffic based on criteria such as source IP address, destination IP address, and port number. By blocking traffic from known phishing domains or IP addresses, firewalls can help prevent them from reaching end users.
Why Is Phishing Successful, and How Can the Right Tools Stop Attackers in Their Tracks?
Although anti-phishing tools can help, they are not foolproof. For example, SMS-based authentication is vulnerable to specific attacks, such as SIM swapping, where an attacker can control a victim’s phone number and intercept their SMS messages.
Firewalls, email filters, and anti-virus software are insufficient to protect against phishing. Although they help block malicious technology, these attacks often use social engineering tactics to trick victims into providing sensitive information.
For example, to convince victims to hand over sensitive information, spear phishing is customized to target specific individuals or types of employees, while whaling phishing is highly personalized to target high-level executives. Email filters may deter some of these messages but won’t work in the case of an account takeover because the sender will technically be legitimate.
Meanwhile, anti-virus software and firewalls cover only phishing attacks that involve malware, like malicious email attachments or web downloads. This leaves attackers free to use techniques like social engineering to bypass the network layer, find weaknesses in the firewall’s configuration, or exploit an OWASP Top 10 vulnerability in a network.
Additionally, phishing attacks constantly evolve and adapt, making it difficult for anti-phishing software to keep up with the latest threats. Attacks that haven’t been added to the software’s database of known threats will pass by undetected.
Ideally, anti-phishing software can serve as an awareness tool for training users to recognize phishing scams autonomously. In a company setting, this helps them to proactively alert the rest of the team or report the attempted attack to the security department for further investigation. However, human error still happens even among well-informed employees.
Corporate security awareness initiatives are often limited to the company’s perimeter, so they don’t protect your users. They could also fall victim to credential theft, malware, supply-chain attacks, and account takeover.
Due to the limitations of current solutions, phishing attacks continue to succeed, and their consequences can be severe. One immediate impact is financial loss since attackers often steal sensitive information such as credit card numbers or login credentials to victims’ online banking apps or trick victims into conducting fraudulent transactions. Additional consequences include compromising sensitive business information, real-time card fraud detection, protection, and disruption, leading to loss of customer trust and reputational damage.
Key Features to Look for in an Anti-Phishing Tool
Specialized anti-phishing software should ideally have a combination of all the following capabilities:
- Real-time detection and blocking of phishing attempts by continuously analyzing incoming emails and web traffic
- ML-based analysis to identify phishing attempt patterns
- Proactive ATO protection to disrupt credential theft and card data theft attempts in real-time
- Deny lists and safe lists to maintain and continually update a database of known phishing sites and email addresses
- Integration with other security systems to provide actionable real-time intelligence and risk engine model enrichment for improved fraud predictions
- Detailed reports and analytics on phishing attempts, including the attack’s origin, the type of attack, and the target
Top 10 Anti-Phishing Tools for 2025
1. Barracuda Phishing and Impersonation Protection
Barracuda Phishing and Impersonation Protection uses AI and ML to detect and block email-based attacks targeting businesses, including corporate email compromise and employee account takeover.
Cons: Users report limited granularity and lack of scope for applying specific rules to subsets of emails, which can lead to excessive blocking of legitimate correspondence, particularly in impersonation or spoofing attacks.
Best for: Large enterprise users.
2. Memcyco
A relatively new player in the anti-phishing space, Memcyco is making waves with its AI-assisted, real-time solution for proactively pre-empting and preventing phishing-related digital impersonation scams and ATO fraud. Memcyco protects companies and customers while stolen data persists and remains available online regardless of takedown.
Uniquely, the solution provides companies with complete visibility into the attack, attacker, and each victim, helping to prevent ATO fraud, ransomware, and data breaches before they occur.
Best for: Enterprises in scam-prone industries
Cons: Small businesses without dedicated Fraud and Security teams may find that Memcyco’s extensive capabilities deliver more than is required.
Review: “Easy deployment, protection during the window of exposure, detailed information about attacks, overall a great tool in fighting fraud.” – Eduardo A. Solutions Engineer”
3. Avanan, by CheckPoint
Avanan by CheckPoint uses AI and ML to enable site-wide protection for cloud solutions. Its one-click API prevents corporate email compromise by blocking phishing, malware, data leakage, and employee account takeover attempts across the organization.
Best for: Companies looking for a one-size-fits-all solution for their cloud platform and corporate email protection.
Cons: Users have reported that the initial setup and configuration process can be cumbersome and time-consuming. This complexity may hinder quick deployment and require significant IT resources.
4. Cofense
Cofense focuses on blocking phishing threats using AI and ML for automated detection and response. It includes access to a professional phishing threat analysis team that constantly analyzes new threats and provides organizations with the data they collect.
Cons: While Cofense is designed to catch phishing emails, there are reports of legitimate emails being flagged incorrectly. This can lead to frustration among users who may miss critical communications.
Best for: Larger organizations with in-house security teams and analysts looking for a solution that will work hand in hand with their current investments to protect employees.
5. IRONSCALES
IRONSCALES uses a combination of AI and human ingenuity to detect various threats in real-time, such as corporate credential theft on fake login pages where victims of phishing emails might reveal personal information, leading to account takeover.
Best for: Organizations with limited IT resources that require an automated solution to detect threats against employees in real-time.Cons: Users have mentioned that the interface can be unintuitive and lacks clarity, particularly when navigating investigation features. This can make it difficult to manage incidents and understand the status of threats efficiently.
6. KnowBe4
KnowBe4 emphasizes employee awareness over being a traditional security platform. It provides phishing awareness training and simulated attacks to test employee knowledge. It also includes incident response and forensic analysis capabilities. Custom ML modules support the different stages of a phishing attack. For example, PhishER processes user-reported phishing and other suspicious emails by grouping and categorizing them based on rules, tags, and actions.
Best for: Organizations looking to implement employee phishing awareness programs.
Cons: Reddit users have reported experiencing many false positives during simulated phishing tests. This can lead to confusion and frustration among employees, as legitimate emails may be flagged incorrectly, impacting overall trust in the training program.
7. Mimecast

Mimecast is a cloud-based email solution that uses AI and ML to defend corporate emails from various threats, including spam, phishing, malware, URLs, and malicious attachments. By securing internal and external email communications, Mimecast helps maintain employee productivity and customer engagement, ensuring that emails reach their intended recipients safely and without disruption.
Best for: Organizations receiving large amounts of email communication that require a general filter for phishing, spam, and other attacks against employees.
Cons: Challenges integrating Mimecast with other systems or applications have been reported, which can limit its effectiveness in a multi-vendor environment. This can complicate workflows and reduce overall efficiency.
8. Outseer
Outseer FraudAction detects and removes threats like phishing, scams, malware, and rogue mobile apps to safeguard brand reputation. Managed by Outseer’s Anti-Fraud Command Center (AFCC) since 2004, the service uses an intelligence engine, extensive partner network, and data feed to detect and take down scams.
Best for: financial and e-commerce companies looking to remove phishing websites and rogue apps.
Cons: Some G2 users report frustration with manually inserting real-time authentication tokens, while similar solutions offer a simple PUSH option for authentication.
9. Valimail
Valimail provides DMARC-as-a-service and hosted DMARC solutions to authenticate sender identities, stop impersonation attacks, and protect brand identity. The platform offers detailed reporting and visibility into authentication results, helping organizations monitor and maintain compliance. As a leader in email authentication standards bodies, the company also develops email protocols for the wider industry.
Best for: Smaller companies who want to understand their email security posture.
Cons: Valimail’s Instant SPF solution uses macro-based SPF records, which some legacy email infrastructures may not support. If emails fail authentication due to unsupported macros, this can result in significant deliverability issues.
10. Trustifi
Trustifi offers corporate email security solutions that organizations can customize to fit their security and compliance needs. It provides security for inbound and outbound emails from a single vendor, AI-based behavior detection, account compromise detection, and archiving features with customizable access controls and permissions.
Best for: Organizations that share sensitive information via email to support daily operations.
Cons: Although many users report positive experiences with customer support, there are mixed reviews regarding response times and the quality of assistance provided. Some users have expressed frustration when seeking help with technical issues.
Get the Pre-emptive Anti-phishing Advantage with Memcyco
Protect your revenue and customer account assets pre-emptively in real time and permanently reduce scam and ATO-related expenses. Read a case study or book a Memcyco demo to discover how Memcyco’s AI-enhanced capabilities are helping global enterprises save tens of millions annually.