As the adage goes, time is money, and nowhere does this ring more true than in an evolving threat landscape. The faster companies detect, respond, and recover from data breaches, the better for their pockets.
Using AI and security automation to shorten the breach lifecycle has been shown to save $2.2 million more on average compared to not employing these technologies.
But more must be done: CISOs must expand their security perimeter to protect their liability from vulnerabilities they can’t see in real-time. One way to start is to define the most common attack vectors hackers use to gain unauthorized access to your systems.
What Are Attack Vectors?
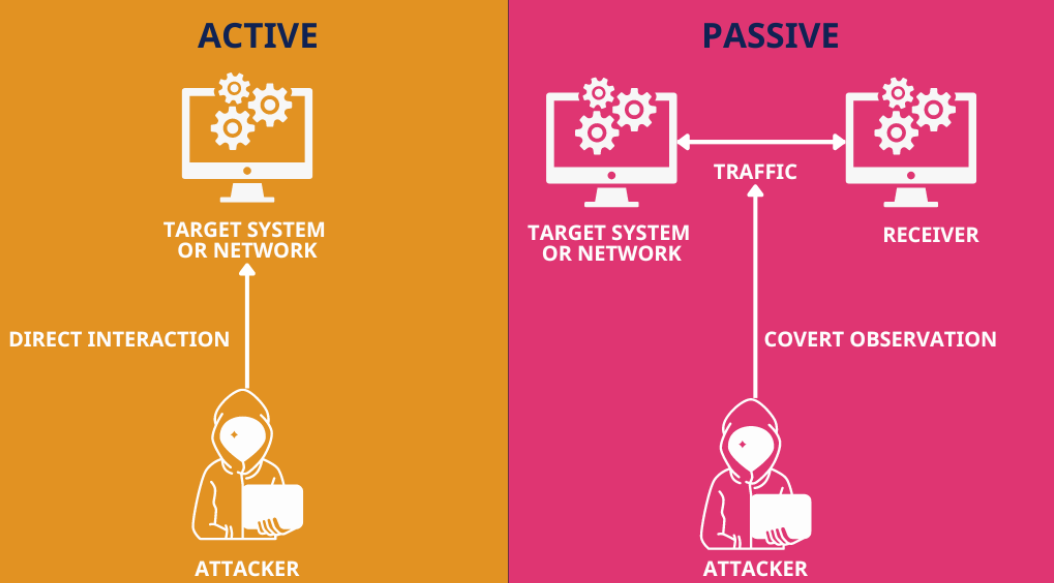
Attack vectors are methods that cybercriminals use to infiltrate systems and networks. These vectors can be either passive or active.
Passive attack vectors let hackers identify vulnerabilities without altering data or interacting with the target. By scanning, sniffing, and eavesdropping ports, attackers gather intelligence on unpatched software and misconfigurations, which can later be exploited.
Reducing exposure and monitoring reconnaissance activity can help prevent these passive techniques from leading to full-scale attacks.
For example, in SEO poisoning, attackers manipulate search engine results to direct users to malicious websites without altering the target company’s systems or data.
Hackers use an active attack vector to interact with an organization’s systems and directly disrupt or compromise them. For example, hackers use malware deployment, phishing, and other disruptive strategies to compromise systems, steal data, or cause operational damage.
Here, we’ll cover both common attack vectors and also critical vulnerabilities that enable those attacks. Recognizing this difference is crucial in helping security teams prioritize mitigation strategies more effectively.
10 Common Attack Vectors to Keep in Mind in 2025
1. Impersonation
Hackers use impersonation attacks to gain unauthorized access to information systems by masquerading as authorized users. 98% of cyberattacks involve some form of social engineering, and brand impersonation is an ongoing trend because it is so effective for social engineering purposes.
Unlike other cybercrimes that exploit software vulnerabilities, impersonation attacks manipulate human behavior. They can happen in person, over the phone, or online, and standard methods include phishing, spoofing, and man-in-the-middle (MitM) techniques.
MitM is not an attack vector on its own but a technique for intercepting and manipulating communications between users, applications, or services. Attackers exploit HTTPS connections, SSL/TLS vulnerabilities, or unsecured WiFi networks to eavesdrop or alter messages. Often, MitM techniques are combined with phishing or spoofed websites to steal login credentials and sensitive data.
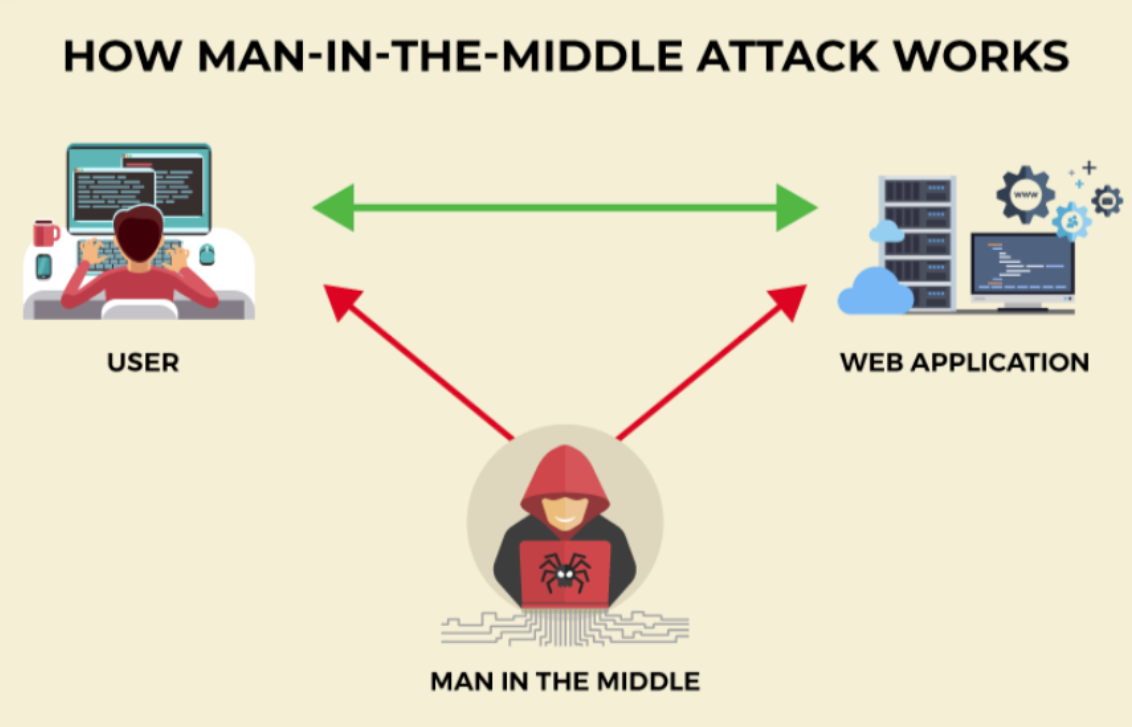
Protecting against this attack vector requires consistent, long-term vigilance. MITM attacks are challenging to detect because they don’t rely on fake URLs, so looking for misspellings in the header or email address won’t cut it. Instead, best practices include avoiding unprotected public WiFi networks, avoiding using unsecured, non-HTTPS websites, and logging out of all sessions after using your device.
Additionally, if you already commit to cybersecurity at an executive level, you can harness this influence to provide cybersecurity tips to your customers. For example, you could assure them that official communications from your brand will always contain certain information, such as their customer ID number.
2. Phishing Emails
There was a 36.6% increase in phishing emails in the first three months of 2024, with Microsoft and Google being the top brands targeted. Email phishing attacks dominate the headlines, but hackers also use tactics like:
- Whaling– this tactic involves impersonating someone known personally to the target (usually a high-profile individual) and sending hyper-personalized fake communications.
- Cloning- a structured approach that impersonates a brand. Hackers send an impersonal email to a long list of victims, hoping for responses.
The key to protecting your business from this attack vector is to modify employee behavior and increase security awareness. You could offer phishing awareness training, enforce organization-wide data protection best practices, and create standard procedures to verify urgent email requests. However, this proactive approach is just the beginning.
Memcyco is the only anti-phishing platform that flags customer clicks of links to impersonating websites in real-time, identifying each individual scam victim.
If customers input credentials or card data into fake forms on malicious websites, marked decoy data replaces them right at the moment of theft, like traceable bank notes used to pay ransom.
If fraudsters try to use the decoy data (and they will, assuming it’s real), they’ll expose device and geolocation data that can be used to trace them, while locking themselves out of the original site.
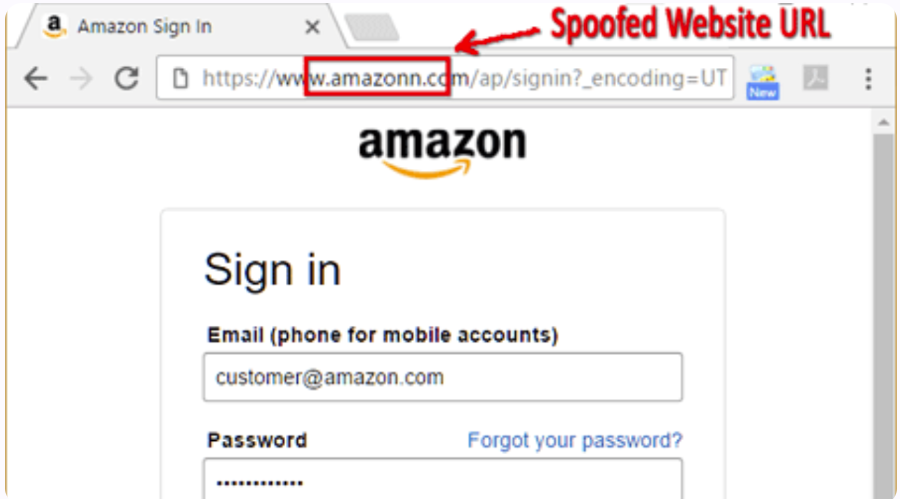
3. Spoofed Websites
Like brand impersonation attacks, domain spoofing targets your end users and customers by using fake domains that, at a glance, look convincingly like your website. Visitors believe they’re accessing a trusted source, but hackers behind the scenes use your brand’s digital trust to steal customer data.
In addition to using barely noticeable fake domains, hackers create cloaked URLs with local redirects, substitute characters in the URL, and fake websites containing minimal differences from your own. Tools like Memcyco enable immediate detection of fake websites originating from the legitimate domain, so you know in real-time if your website has been spoofed and can react quickly to prevent any development.
4. Malicious Code Injections
Rather than creating fake websites, as seen above, hackers also inject malicious code scripts into legitimate applications to perform a variety of exploitations. While the primary goal is to access sensitive information, such as session IDs, hackers could modify site content, perform remote code execution, or add malicious redirects. Recent trends in this attack vector include:
- XSS: Executing malicious code into the user’s browser via legitimate web applications.
- Keylogging: Recording keystrokes to access what you type, including passwords and credit card numbers.
- Ad fraud: Overlaying fake content on ads so victims click on fake premium URLs and enter their data.
To protect against this attack vector, OWASP recommends either only allowing data that matches your predetermined “good” rules (allow listing) or blocking data that matches your predetermined “bad” rules (blocklisting).
5. SSRF
Server-side request forgery (SSRF), listed in OWASP’s Top 10 security threats, is expected to make a major comeback as a critical attack vector in 2025. In 2024, SSRF attacks targeted multiple industries, with one of the most notable incidents involving Ivanti Connect Secure. Attackers exploited the CVE-2024-21893 vulnerability, enabling them to gain unauthorized access and perform remote code execution (RCE) on Ivanti’s network appliances.
Detecting SSRF vulnerabilities can be challenging. Standard SSRF is relatively easy to identify on the server side, but blind SSRF is more elusive. Blind SSRF occurs when an application sends a request to a back-end server, but no response is returned directly to the attacker. Instead, it enables attackers to pivot within internal systems, potentially accessing sensitive data or launching further exploits.
To minimize the risk of SSRF attacks, organizations should:
- Validate inputs: Implement strict filters for user inputs, using an allowlist/blocklist approach to restrict external requests.
- Enable authentication on internal services: Require authentication for internal tools, services, and APIs, even on local networks.
- Enforce URL schemas: Disable unused URL schemes and restrict internal resource access to prevent unauthorized requests.
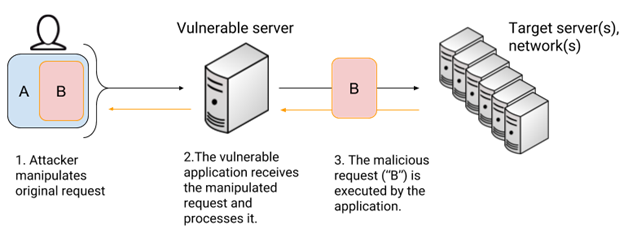
6. Third and Fourth-Party Vendors
It’s almost impossible to imagine a world where businesses don’t outsource to third parties, whether for operational, financial, or technical support. As your corporate data becomes the property of third and fourth-party vendors, the absence of a real-time view of the vendors’ cybersecurity measures makes this attack vector increasingly exploitable for hackers.
Emerging technologies, like material informatics, can also introduce new risks as more companies in sectors like manufacturing and supply chain management adopt AI-driven tools. These innovations can expose businesses to vulnerabilities they may not be prepared to handle.
Protecting against supply chain attacks starts before your vendor signs on the dotted line. You can request a SOC report from vendors to better understand how they protect sensitive data and identify risk levels.
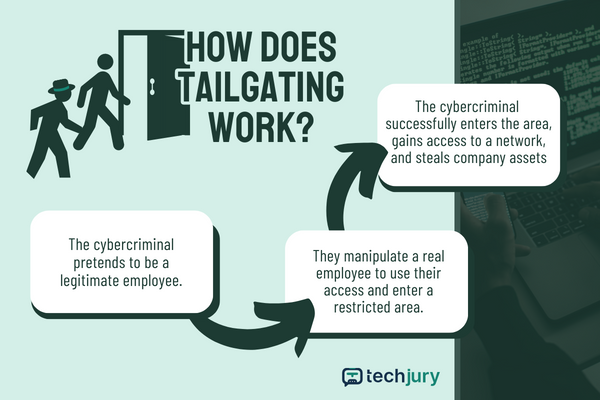
7. Tailgating
We’ve all seen James Bond sneaking behind a server to gain access to an exclusive event. The same premise applies to tailgating–a social engineering attack (yup, again) through which the bad actor gains physical access to a restricted location to steal off-limits information.
You’re at an increased risk of this attack vector if you have many employees or multiple access points in your building. To help prevent it, implement biometrics like fingerprint scanning, facial recognition, or a similar biometric authentication system that can’t be easily replicated. You can also develop a security policy for your physical premises and ensure all employees know it by heart. It could include a hierarchical access control structure and employee identification cards.
8. Missing or Poor Encryption
An ongoing trend in cybersecurity is customers’ growing knowledge base–for example, even non-technical customers and users are aware of encryption, how it works, and its purpose in protecting data. That’s why excuses won’t fly if your organization falls victim to this attack vector. Encrypting sensitive data is not enough; your organization should apply encryption to data at rest (stored) and in transit.
9. Unpatched Software
Unpatched software remains a critical vulnerability that cybercriminals exploit to launch attacks. As software ecosystems grow more interconnected, overlooked security gaps provide entry points for attack vectors like remote code execution and privilege escalation.
Notorious cases like Log4Shell, which impacted 55 products before detection, and the 2023 MOVEit Transfer vulnerability, exploited for SQL injection attacks, show how quickly unpatched flaws can be weaponized—even after patches are released.
10. Misconfigured Systems
Misconfigurations are another exploitable vulnerability that exposes organizations to attack vectors like XSS, code injection, and DDoS attacks. Increasingly, hackers target IoT devices and cloud infrastructure, exploiting IAM misconfigurations and API gateway weaknesses.
Mitigating these risks requires a least-privilege access approach, regular software updates, frequent security scans, and static analysis.
Heading Towards a Better Year For Security
The ten attack vectors above highlight how creative and relentless bad actors are today. Organizations need real-time, adaptive defenses—not outdated, reactive approaches to stay ahead.
Memcyco’s real-time AI-assisted capabilities do more than just detect threats; they help pre-empt and disrupt them proactively.
With Memcyco, you’re not just defending—you’re outsmarting attackers at every step. Let’s build a safer digital environment together.
Book a product tour. You’ll tell us which attack vectors you’re facing, and we’ll explain how Memcyco outperforms other solutions in those specific scenarios.