Some cyber attacks garner significant media attention, while others go under the radar. Domain hijacking attacks fall into the latter category as a downplayed cyber threat with potentially catastrophic consequences.
Many businesses arguably don’t treat their domain name as something that requires significant attention from a cybersecurity perspective. The result is that hackers often successfully take over domains using a range of methods. Big companies aren’t immune to these attacks either; hackers seized a Ferrari subdomain and used it to run a crypto scam in 2021.
This article aims to increase awareness about domain hijacking by explaining what it is, how to recover a hijacked domain, and how to improve domain name security to prevent this threat.
What is domain hijacking?
Domain hijacking occurs when a threat actor gains control over a domain name. Many website owners and administrators take ownership of their domains for granted. Still, opportunistic cybercriminals know it’s possible to seize control of unsuspecting targets’ websites and sub-domains using various methods and tools.
The potential for damage from domain hijacking is enormous:
- Financial—many businesses depend solely on their websites for generating revenue (think eCommerce and SaaS companies). Losing control of their domain name can result in thousands of dollars in lost revenue, posing an existential risk to a company’s survival.
- Reputational—hackers taking control of your domain get to manipulate the asset that acts as the face of your company online. The reputational outcomes, such as posting offensive content , financial scams, or redirecting visitors to malicious domains(pharming), can impact any organization. Furthermore, there are knock-on impacts from having a key communication channel with current or prospective customers disrupted.
- Regulatory—in an increasingly strict regulatory landscape that protects customer data privacy, businesses are held accountable for data breaches, whether they happen due to human error or malicious outside attacks. Domain hijacking gives hackers a way to capture sensitive data by redirecting customers to fake web forms and pages that look exactly like your legitimate website.
4 Types of domain hijacking
Don’t confuse domain hijacking with domain spoofing. Spoofing relies on impersonating your website with a fake one (often by registering a domain name with a slight spelling variation from the legitimate name). Hijacking involves an outsider getting actual control over your domain name. Depending on how the takeover occurs, domain hijacking can manifest as:
- Social engineering tactics deceive website admins or owners into revealing login credentials for domain registrar accounts or downloading keyloggers that allow hackers to steal credentials covertly.
- Registrar security breaches, such as backend admin accounts belonging to registrar employees getting compromised.
- Website, digital asset management, and web server vulnerabilities that provide intruders with a way in.
- Expired domain registrations that third parties then register (legally) to their account. For example, hackers took over a website for the programming language Perl after its registration had elapsed and then used it to redirect visitors to an IP address associated with malware.
Is my domain name vulnerable?

There is no direct way to know if your domain name is vulnerable to hijacking, so it is prudent to assume that it is. A complex interplay of factors influences this susceptibility, including awareness of social engineering attacks like phishing and whaling, the number of parties with access to domain name registration platforms, the security of the domain name registrar’s platform, and vulnerabilities in the web servers that host your website.
Can I recover my hijacked domain?
As with many types of cyber attacks, prevention is better than cure. While all is not lost if your website gets taken over, you only really have two options to recover:
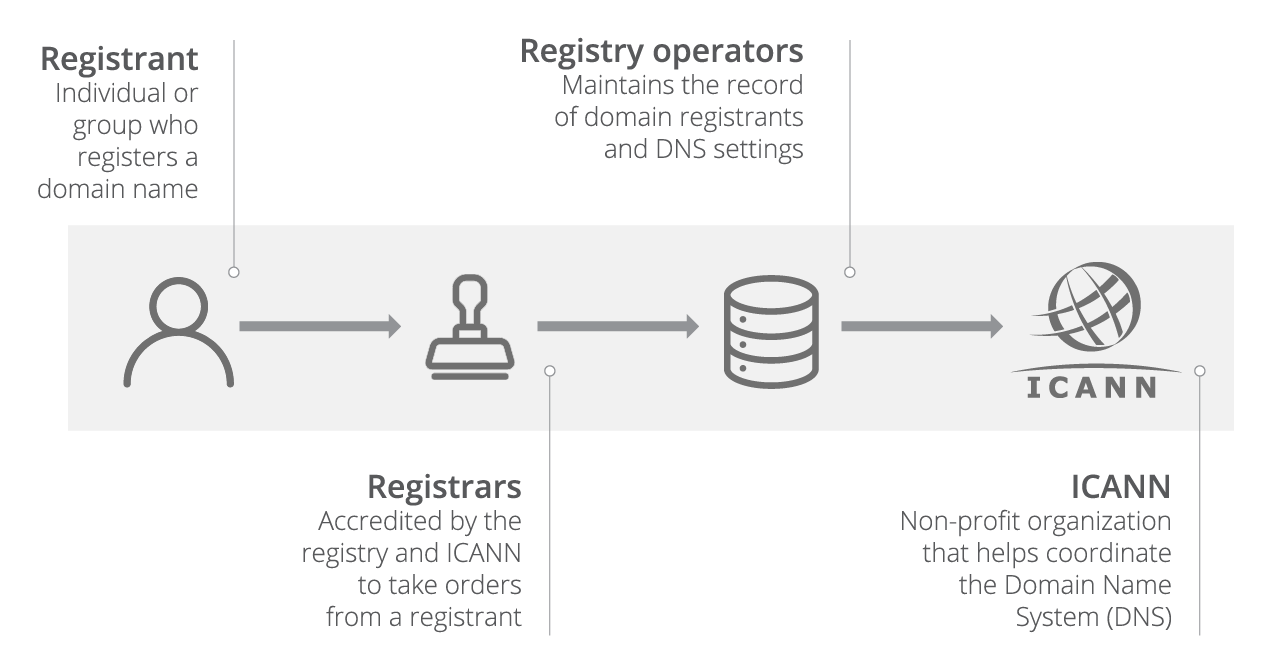
- Contact your domain registrar: Any decent domain registrar will have its customer support team to help solve problems like domain hijacking. Contacting yours is the most straightforward and fastest resolution method, although you must provide as much evidence as possible proving you are your domain’s legitimate owner.
- Dispute the ownership: If you find out too late that your domain has been hijacked, the hacker may have transferred your domain to another registrar. In complex cases like these, it’s imperative to get your original registrar to contact ICANN (Internet Corporation for Assigned Names and Numbers), as this organization has the authority to settle disputes between different domain registrars over unauthorized transfers of domain names.
10 steps to prevent your domain from being hijacked
Here are some actionable steps to reduce the likelihood of your domain being hijacked.
1. Select a reputable registrar
Move beyond just prioritizing the cost of domain registration or the privacy you get as a website’s owner when selecting a domain registrar. When considering which registrar to purchase a domain name from or transfer your domain name to, give considerable weight to the registrar’s security features. In particular, look out for extra protection, such as:
- Two-factor and multi-factor authentication options to secure your admin account against intrusion from stolen login credentials.
- Look for a registrar with a customer support team that’s available 24/7.Suppose your domain gets hijacked on the weekend, and no support is available to help you recover. In that case, the loss of revenue and reputation from extended downtime or malicious activities could ruin your business.
- The ability to manage DNS records directly from the registrar’s control panel helps regain control of your domain name faster if your admin account gets compromised because you can reset the login details.
2. Maintain good credential hygiene
Most people know weak passwords are risky, but some continue using strings like 12345 and qwerty. Don’t choose easily-guessable passwords for your domain registrar account—make it very difficult for hackers to brute force their way in. And remember that even if the registrar has security options like 2FA or MFA, you’ll probably need to switch them on yourself to benefit from these features.
3. Enable domain locking
If you’ve already chosen a good registrar, you’ll likely have a readily available setting that markedly reduces the probability of domain hijacking. This setting is called domain locking or registry lock, and it blocks unauthorized transfers or changes to a domain. Many registrars automatically turn on this setting, but it’s worth verifying and turning it on if disabled.
4. Leverage WHOIS privacy protection
Threat actors often use widely available WHOIS database information when probing potential target websites for domain hijacking attacks. This database is a treasure trove of data about website owners and their contact details. It’s worth using WHOIS privacy protection, which most registrars offer for an extra fee, to limit data exposure and prevent hackers from easily finding an email address to target with their social engineering scams.
5. Keep contact details updated
Updating your contact details is a somewhat overlooked method of protecting against domain hijacking. Outsiders can exploit outdated information to their advantage by having more time to inflict damage if they get inside your registrar account. An old email address or phone number means that the registrar can’t contact you promptly if they notice any suspicious activity from their side.
6. Beware of phishing
Phishing scams (that lead to domain hijacking) commonly use emails purporting to be from either your domain registrar or ICANN. Threat actors are getting better and more targeted with their emails, often employing sophisticated methods and clone phishing to mimic these trusted organizations. Being vigilant about the prevalence of phishing and the tactics used by hackers reduces the risk of falling victim. If you do receive messages purporting to be from your registrar or ICANN, forward them to an address such as globalsupport@icann.org to verify their authenticity.
7. Separate domain and web hosting accounts
As most registrars essentially offer the same basic service, they’ve started to differentiate themselves with all-in-one packages in which you get both domain name registration and web hosting in one convenient account. In this case, it’s worth foregoing convenience and separating your domain and web hosting accounts, even if both are with the same company. Losing control of your domain name and web hosting in one fell swoop worsens the severity of a domain hijacking attack.
8. Don’t share login details unnecessarily
Many stakeholders in a business need access to the back end of a company’s website, whether for IT admin, load balancing, development purposes, or marketing campaigns. Sometimes, these stakeholders ask for access to the domain registrar platform to make changes, but this is generally not advisable. Exercise the least privilege principle, and don’t unnecessarily share login details for this account.
9. Register and renew for the maximum allowable period
This tip helps mitigate domain hijacking attacks that stem from exploiting expired domain registrations. When you register or renew for the maximum allowable time span, you can avoid situations where people find valuable domain names that have expired and quickly re-register them to seize control.
10. Use innovative solutions
As websites become more valuable business assets, new security solutions emerge to protect them. Solutions that offer visual proof of your brand’s website authenticity can be particularly useful in mitigating some of the worst outcomes from domain hijacking. These include customers disclosing personal information to a spoofed version of your company’s website or being subjected to fraud by having card details stolen on those fake pages.
Protect your business and customers from fraud
Memcyco provides a unique PoSA (Proof of Source Authenticity) solution to benefit businesses and customers, giving all end users an easy way to verify that the websites they are engaging with are authentic. This helps to prevent the fraud and brand impersonation tactics that often accompany domain hijacking.
PoSA displays a unique and unforgeable digital watermark to customers visiting your website. Meanwhile, it alerts your security team in real time if an impersonation attack was attempted using your brand’s name (and hard-earned reputation). Install Memcyco in minutes, with no user registration or installation needed: Book your demo here.