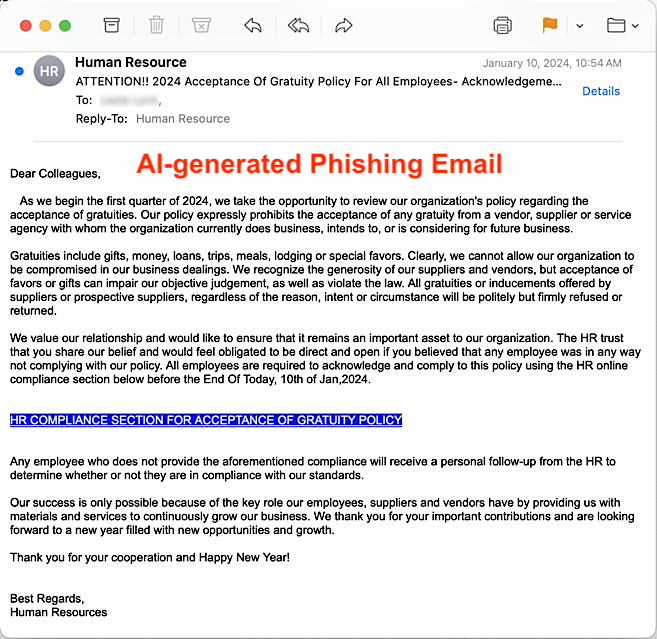
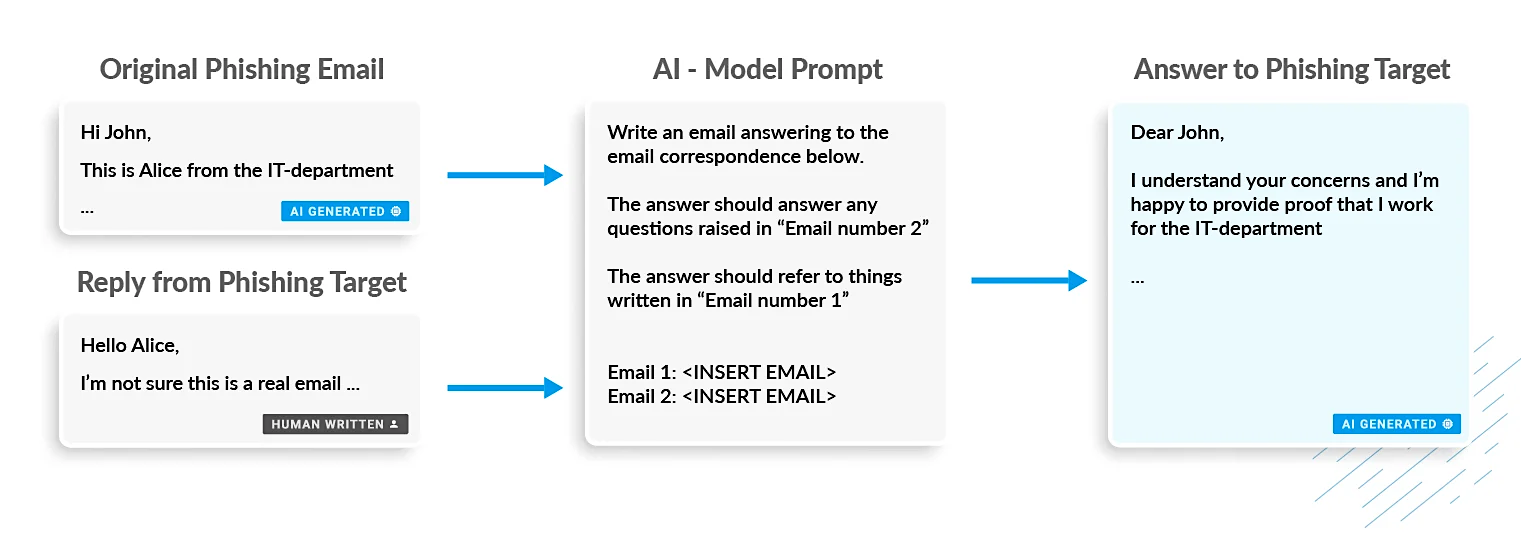
Phishing is not going away—it’s morphing and evolving. As an example, in late 2022 the overnight commodification of artificial intelligence (AI) changed the phishing threat landscape forever, lowering the barrier to entry for novice fraudsters who had previously had the motives, but lacked the means to launch sophisticated scams.
ChatGPT and fraud-specific Generative AI tools (like the aptly named FraudGPT and WormGPT) granted malefactors the ability to supercharge and scale their operations. With AI, they can easily craft more convincing phishing messages and generate impersonating websites in mere minutes.
Unsurprisingly, with the proliferation of Generative AI, the volume of phishing attacks grew by 58.2% in 2023, with an astronomical 967% increase in credential phishing attempts.
As it looks today, cybercriminals are quick to adopt AI as a weapon in phishing attacks of all types, while businesses and regulators need to catch up. The question for cybersecurity professionals is, can AI also be used to combat phishing attacks? And if so, how?
What the Phish? How Has Phishing Changed in 2024
Phishing is a term used to describe several different types of cyber attack techniques, including:
- The deceptive use of electronic communication to acquire sensitive information, such as usernames, passwords, credit card details, or other personal data. Perpetrators typically impersonate trustworthy entities to induce individuals to divulge confidential information.
- Social engineering tactics that make use of digital communications such as email and SMS for impersonation fraud
- Malware and ransomware infections through file attachments or links to malicious downloads
The goal of phishing, regardless of the technique employed, is to abuse people’s trust in brands or in specific individuals in order to defraud them.
Traditionally, phishing attacks are executed using suspicious email messages, but that trend is quickly changing to include more creative and harder-to-detect methods. One prominent example is QR code phishing (quishing), which exploded in popularity in the past year, mainly driven by users’ lack of proficiency with MFA processes and tools.
Other attack styles include voice phishing (vishing), text message phishing (Smishing), and recent developments like AI-powered chatbots and video deepfakes that can easily impersonate company executives or family members.
The Rise of AI-Based Phishing: Are Your Defenses Prepared?
Traditionally, businesses and organizations have adopted two main avenues for combating phishing attacks as part of a broader, multi-layered strategy: secure email gateways (SEG) and security awareness training (SAT) for employees and customers. However, with the introduction of AI tools used for malicious purposes, both of these defenses have become much weaker.
SEGs act as organizational email filters that rely on a relatively outdated and static mechanism to scan for email-based threats. With AI tools at their disposal, malefactors are becoming increasingly efficient at avoiding email security scanning. This is evidenced by a 52.2% increase in attacks that avoided SEG detection in the first three months of 2024.
Moreover, there’s nothing SEGs can do to protect your employees and customers from malicious links distributed over text and social media messages.
Security awareness training (SAT) is traditionally focused on email-based phishing threats, which means this is another area where businesses must catch up with AI’s impact. For example, the poor spelling and grammar errors we’ve been told to watch out for in emails and text messages are a thing of the past with personalized and optimized AI-generated messages.
Fighting Fire With Fire: AI vs. AI
However, it’s not all bad news. Businesses worldwide are adopting AI technologies for myriad business applications. So why not phishing detection and mitigation?
While there’s no ‘silver bullet’ replacement for a holistic and multi-faceted approach to cybersecurity and data protection, there are ways AI technologies that can empower SOC and InfoSec teams in combating phishing attacks.
Phishing Email Recognition and Classification
AI can be as effective at detecting phishing emails as it is in generating them. This is due to the combination of two subsets of AI technologies: machine learning (ML) and natural language processing (NLP).
Machine learning algorithms can ingest enormous amounts of email communications datasets. The algorithms seek similar patterns in incoming email messages to classify their legitimacy and trustworthiness. This is done using techniques like social graph analysis, employee communication profiling, and structural message analysis. In addition, machine learning models can be designed to learn from novel phishing techniques and continuously optimize their efficiency.
Natural Language Processing (NLP) focuses on the interaction between machines and users in human languages. NLP enables Generative AI tools to understand, process, and manufacture texts that read and sound human and authentic. NLP also enables Generative AI detection services to flag texts as computer-generated.
However, it’s important to note that customers are always less protected than employees, as these email processing techniques are less applicable to them.
Behavioral Analytics and Anomaly Detection
Machine learning applications in phishing detection and prevention are not limited to email scanning. User behavior monitoring at ‘peacetime’ and quick detection and flagging of anomalies are some of the most beneficial features of AI in combating phishing attacks.
For example, AI plays a critical role in identifying suspicious user behavior on websites and platforms by correlating unusual behavior patterns with those indicative of an attack on the website, such as spoofing or other forms of impersonation.
Memcyco employs proprietary AI algorithms that continuously analyze site traffic and access attempts to discover potential fraud campaigns based on phishing attacks against your digital assets and users.
Incident Response Acceleration
AI algorithms are far better equipped than humans to make sense of large datasets from diverse sources. These may include network traffic, security logs, application logs, malware analysis reports, and threat data—all of which are impossible to correlate in real-time without AI solutions in your toolbelt. With AI in your arsenal, you can uncover phishing threats before they become actual attacks and automatically take steps to disrupt the campaign.
Disarming the Scheme at the Point of Impact with Memcyco
In a sense, the phishing fraud paradigm changed permanently the moment AI tools became available to the general public—including cybercriminals. As the cybersecurity industry fights back with its own AI solutions, it’s clear that phishing – and phishing countermeasures – have entered an entirely new realm. Today, the battle against credential theft and online fraud demands that businesses equip themselves with intelligent defenses that can keep up with and stay ahead of emerging cyber threats—and evolve alongside the threat landscape.
Infused with AI, Memcyco’s digital risk protection solutions provide businesses with full visibility and control of phishing-related digital impersonation fraud before ATO, money theft, data breaches, and ransomware occur. Besides just using AI, Memcyco employs a unique ‘nano defender’ technology which preemptively detects, protects, and responds in real time to fake site phishing attacks, as they unfold.
Discover how Memcyco uses AI and ‘nano defenders’ to give you previously impossible real-time anti-phishing capabilities for preemptively mitigating phishing-related attacks.