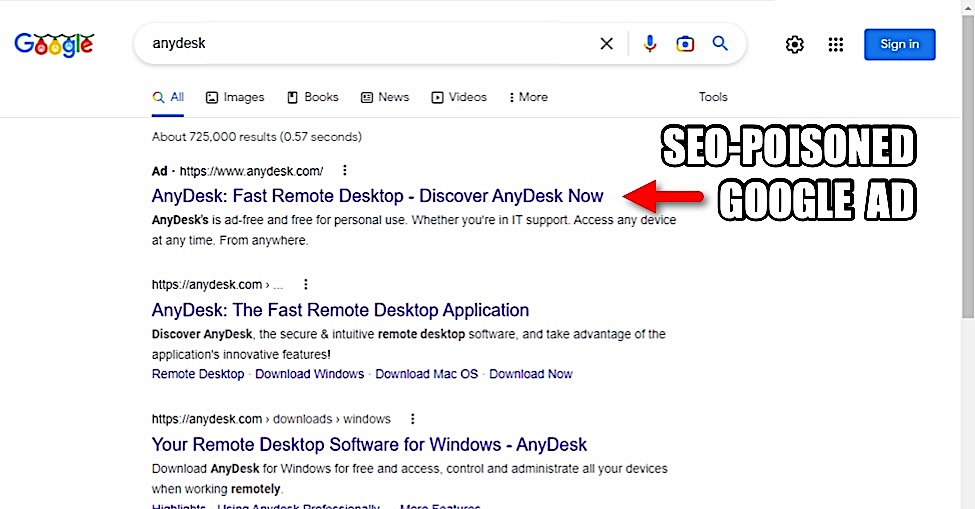
Search engines are the Internet’s gateway, reliably guiding us to the information we seek. However, cybercriminals are increasingly exploiting this trust by using sophisticated techniques to manipulate search engine results to drive traffic to malicious websites by getting them ranked higher than real sites. This practice, known as SEO poisoning, poses a significant threat to individuals and businesses.
In a notable example, a 2022 campaign saw 15,000 sites hacked in a Google SEO poisoning attack. These fraudulent sites ranked high in search results and lured unsuspecting users into clicking links, leading to malware downloads and credential theft scams.
The attackers’ success in this campaign highlights the growing danger and effectiveness of SEO poisoning tactics.
What is SEO poisoning?
Search Engine Optimization (SEO) poisoning is a cyberattack technique that manipulates search engine results pages (SERPs) to promote harmful websites.
Cybercriminals create or modify web content and employ aggressive search strategies that artificially boost the ranking of malicious web pages for popular keywords. These websites are often designed to look legitimate, digitally impersonating known brands with content that appears relevant and trustworthy.
The goals of SEO poisoning include:
- Distribution of Malware: Luring unsuspecting users into downloading malware (viruses, spyware, ransomware, etc.) that can infect their devices.
- Credential Theft and Account Takeover (ATO): Tricking users into exposing their account login credentials or other personal information via fake websites that give attackers access to sensitive data.
- Luring Consumers to Financial Scams: Promoting fraudulent schemes involving phony gift cards or fake e-stores selling seemingly discounted or counterfeit products that may never arrive.
- Spreading Misinformation: Disseminating false information to manipulate public opinion or cause confusion.
- Reputation Damage: Damaging the reputation of individuals, businesses, or organizations by associating them with malicious content.
- Traffic Diversion: Redirecting traffic from legitimate websites to malicious ones deprives the original site of visitors and potential revenue.
Who is affected by SEO Poisoning?
SEO poisoning affects regular Internet users who want to find information online but inadvertently click on poisoned links that might compromise their personal data, infect their systems with malware, or lure them into making purchases on a fake e-store.
SEO poisoning scams target individuals. However, the businesses whose online presence it compromises suffer reputation damage, potential loss of sales, churn risk, and incident remediation expenses. Recognizing the signs of SEO poisoning is crucial for safeguarding digital trust and your online presence.
Businesses can also suffer from ranking lower than they would for target keywords or take reputational hits when hackers target company sites to conduct SEO poisoning and redirect searchers to malicious sites.
It’s also worth noting that a search engine’s credibility and reliability are at stake if it often directs users to malicious websites.
How does SEO poisoning work?
A typical SEO poisoning attack starts with target selection.
Attackers choose popular keywords, especially those trending or related to current events, to target many users. These keywords can range from terms related to news and entertainment to software downloads and health advice.
Hackers then decide whether to create their own site as a malicious source that ranks above legitimate websites, or to find flaws in existing sites and redirect unknowing users to malicious pages. Whatever route they choose, various SEO tactics and link-building campaigns help to rank the target site better and manipulate rankings.
Once users arrive at the malicious site, they are subjected to various threats. These threats include malware downloads, ransomware, phishing attempts to steal personal information, and fake stores that let you pay but deliver counterfeit goods or never deliver any products at all.
5 Types of SEO Poisoning Attacks
Algorithms, like the one used by Google, decide how to rank websites based on many so-called ranking factors. These algorithms are complex, and their exact workings remain a secret only known by insiders at major search engine companies.
However, just because SEO algorithms are complicated, this doesn’t make them immune to various blackhat methods used for SEO poisoning:
1. Keyword Stuffing and Hidden Text
Keyword stuffing is the overloading of web pages with popular or trending keywords. These keywords might be unnaturally repeated in the text or hidden from view but still readable by search engines. For example, Cascading Style Sheets (CSS) tricks might be used to make the text the same color as the background.
2. Cloaking
Cloaking is presenting different content or URLs to human users and search engines. Users might see a regular page, while search engines see a version heavily optimized with keywords or links.
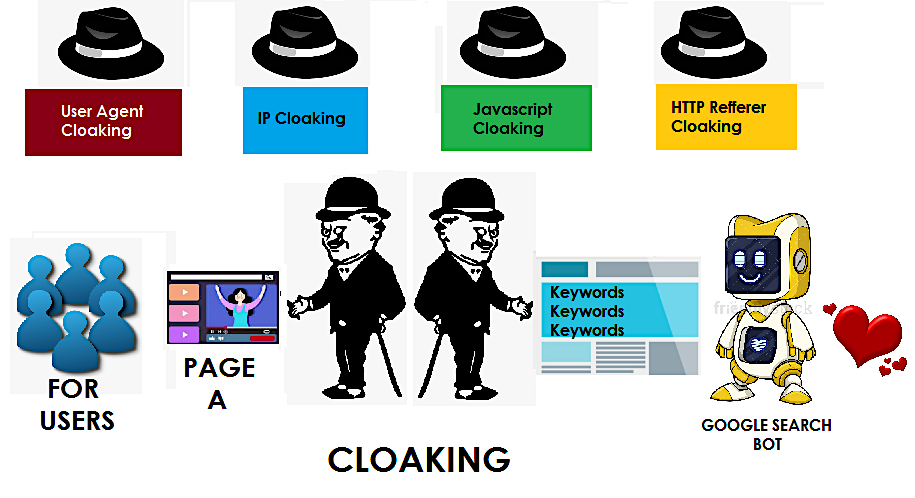
3. Link Farms
Link farms involve creating or using networks of websites that link to each other to increase the amount of inbound links to a site. This scheme exploits most search engines’ heavy reliance on backlinks as a ranking factor. Links can artificially inflate the site’s rank by suggesting it is more relevant or authoritative than it is.
4. Scraper Sites
Scraper sites scrape content from legitimate websites and reproduce it to exploit the search engine’s preference for content-rich sites. The goal here is to quickly and easily create content that can be optimized for search, diverting traffic from the original site. Memcyco can help protect against this type of attack because scraping content and reproducing it triggers Memcyco’s ‘nano defenders,’ which then respond to the attack.
5. Malicious Redirects
Malicious redirects exploit the site’s search engine ranking to redirect unsuspecting visitors to harmful locations. Here are some common methods attackers use:
Open Redirect Flaws
Open redirect flaws occur when vulnerabilities in your legitimate site’s code enable hackers to redirect users to any domain of their choosing using your actual domain name. This method takes advantage of the site’s trustworthiness, leading users to malicious sites without their knowledge.
Blackhat SEO Tactics
Blackhat SEO tactics involve attackers artificially inflating a site’s rankings and then inserting malicious links on the high-ranking page. Users are misled by the high search ranking, assuming the site is legitimate, only to be redirected to harmful destinations.
Cross-Site Scripting (XSS)
Cross-site scripting (XSS) attacks occur when attackers inject malicious scripts into a webpage, which can then redirect users to harmful sites. XSS vulnerabilities happen when web applications fail to properly sanitize user input, allowing attackers to execute arbitrary scripts in the user’s browser. These scripts can manipulate web content, steal information, or force redirects to malicious destinations.
Server-Side Request Forgery (SSRF)
Server-Side Request Forgery (SSRF) is a vulnerability that allows attackers to send crafted requests from the vulnerable server, which can potentially be used to redirect users. SSRF can be particularly dangerous because it leverages the server’s privileges, often bypassing network restrictions and accessing internal services, leading to harmful redirects.
5 Signs You Could Be Impacted by SEO Poisoning
Here are the key signs that your business website may be ‘poisoned’ by malefactors manipulating SEO:
1. Security Warnings
While some SEO poisoning tactics specifically target legitimate sites, many are brand hijacking attacks that clone existing websites of genuine brands, or create fake versions from scratch with slightly misspelled names, such as www.nikee.com.
Browser Flags
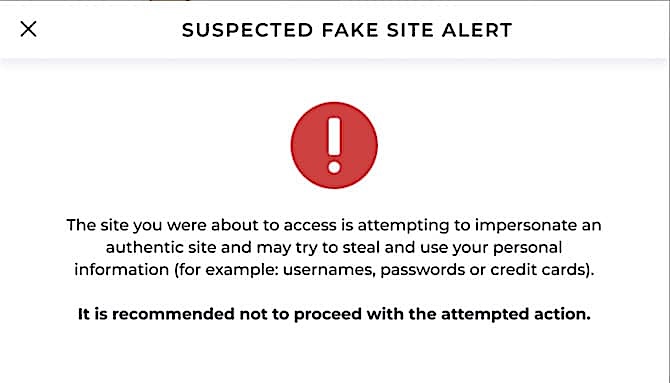
One sign of SEO poisoning is that the browser flags a security warning on the site. This warning can indicate that the site has been compromised or is known to distribute malware. Modern browsers and security programs excel at detecting suspicious behaviors such as unauthorized script executions, attempts to download files automatically, or redirections to known malicious domains.
Warnings are typically presented to users as alerts or notifications that block access to the site and caution them about the potential risks ahead if they proceed. However, as a general rule, these browser flags are not set up in real-time (when fake site attacks start). As a result, many users will still fall into SEO poisoning traps until this happens.
The Memcyco Difference
While users might be tricked into visiting these sites through hijacked search engine results or phishing emails, digital impersonation protection solutions like Memcyco protect against phishing-related fraud involving fake websites. Memcyco instantly detects in real-time the pre-attack signs of fake site reconnaissance attempts, fake site URL registration, and when impersonated sites actually go live.
Memcyco also adds a watermark to your website that proves its authenticity while issuing real-time Red Alerts via fake sites that warn customers to turn back. Most importantly, Memcyco has developed an anti-SEO poisoning mechanism as part of its Digital Impersonation Protector product.
2. Unexpected Search Results
Your company’s website might suddenly rank for irrelevant or inappropriate keywords unrelated to its content. A similar unexpected search result is seeing suspicious sites with poor-quality content ranking higher than your company’s.
Threat actors often achieve this manipulation through paid backlinks or by employing negative SEO tactics, wherein they direct spammy links at your authentic website to drag down the search engine’s perspective on its legitimacy.
3. Suspicious Website Design
Changes in your website’s design that you didn’t implement—like unusual pop-ups, unfamiliar banners, or intrusive advertisements that were not part of the original design—are telltale signs of being the victim of SEO poisoning. These changes indicate that the website might be compromised and used to host or link malicious content.
The goal is to exploit your site’s traffic for nefarious purposes. Visitors might encounter unexpected redirects that take them away from the intended content to entirely different, often malicious, sites. Hackers usually look for open redirect flaws in a site’s code that allow them to redirect visitors to a chosen domain.
These alterations are usually implemented without the knowledge or consent of whoever is in charge of your site’s design and maintenance.
4. Misleading Content
Misleading content includes articles, blogs, or landing pages filled with popular keywords that make little sense or contain false information. The primary aim of this content is to deceive search engines into ranking these pages higher for certain search queries, which increases the website’s visibility and traffic.
For users, encountering such content can be confusing and erodes trust in both the website and the search engine delivering the results. To make matters worse, this kind of content often serves as a gateway for more malicious activities, like redirecting visitors to harmful websites or tricking them into downloading malware.
5. Software Downloads and Prompts
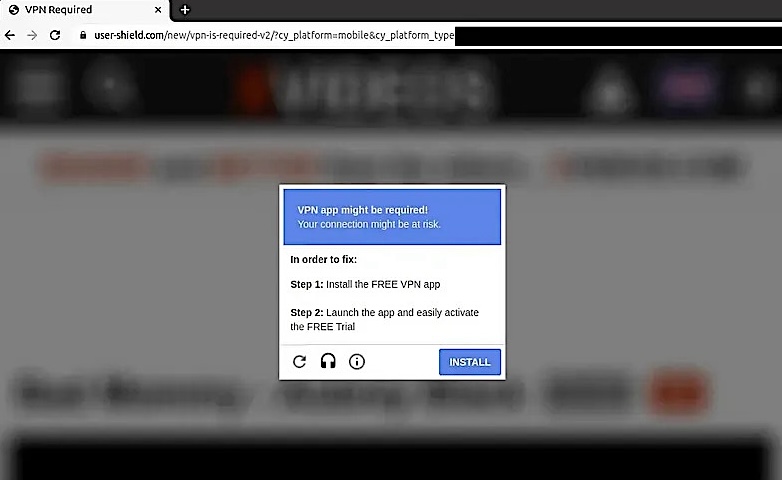
Software downloads or prompts that unexpectedly appear on a website can be used to exploit visitors by installing malware.
Typically, these prompts disguise themselves as essential updates for user device software such as browsers, flash players, or antivirus programs. They mislead users into thinking they are performing routine maintenance on their systems. However, once clicked, these downloads install malware that can steal data or lock users out of their computers until a ransom is paid.
By manipulating SEO rankings to increase traffic to these compromised sites, attackers increase their chances of successful malware infections. These prompts should raise immediate concerns for users and businesses, especially on websites where downloading software is not normally expected.
Protect Revenue, Reputation, and Digital Trust from SEO Poisoning with Memcyco
Falling victim to SEO poisoning attacks can lead to loss of customer trust, reputation damage, and compliance issues. With your business relying on organic search traffic for its operations and revenue, ensuring your digital presence is secure from malicious tactics is critical.
Integrating Memcyco into your digital trust strategy will significantly bolster your defenses against SEO poisoning. Memcyco protects against four different malicious website impersonation techniques:
- Websites created through cloning, spoofing, iFraming, or ClickJacking
- Websites built from scratch with a redirect to the original site
- Websites built from scratch that contain graphic elements from the original site (CSS, images, etc.)
- Websites built from scratch, with no redirect and no elements from the original site
Memcyco’s Digital Impersonation Protector product provides a feature that checks fake websites to determine whether they use SEO poisoning techniques. In case they do, Memcyco disarms these mechanisms, which helps protect the genuine site from impersonating sites that use these tricks to rank higher.
Discover real-time protection against SEO poisoning. Book a Memcyco demo.