Navigating the internet today can be a minefield. With the rise of malicious websites, customers and employees must now think twice before clicking on unfamiliar links or sites. Attackers often try to spoof and ‘brandjack’ well-reputed organizations and lure users into giving away personal info, money or letting hackers into their systems.
A 2023 study showed that brandjacking attempts targeted over 1000 organizations—and 51.7% of those attacks impersonated significant global brands, including Google, SalesForce, and Notion.
Dangerous, fraudulent websites could quickly ruin your company’s reputation, destroy digital trust, and lead to significant financial losses—not to mention injecting malware that disrupts business operations or holds sensitive data for ransom. That’s why everyone needs to know how to spot and stop these fake sites before they do any damage.
What are malicious websites?
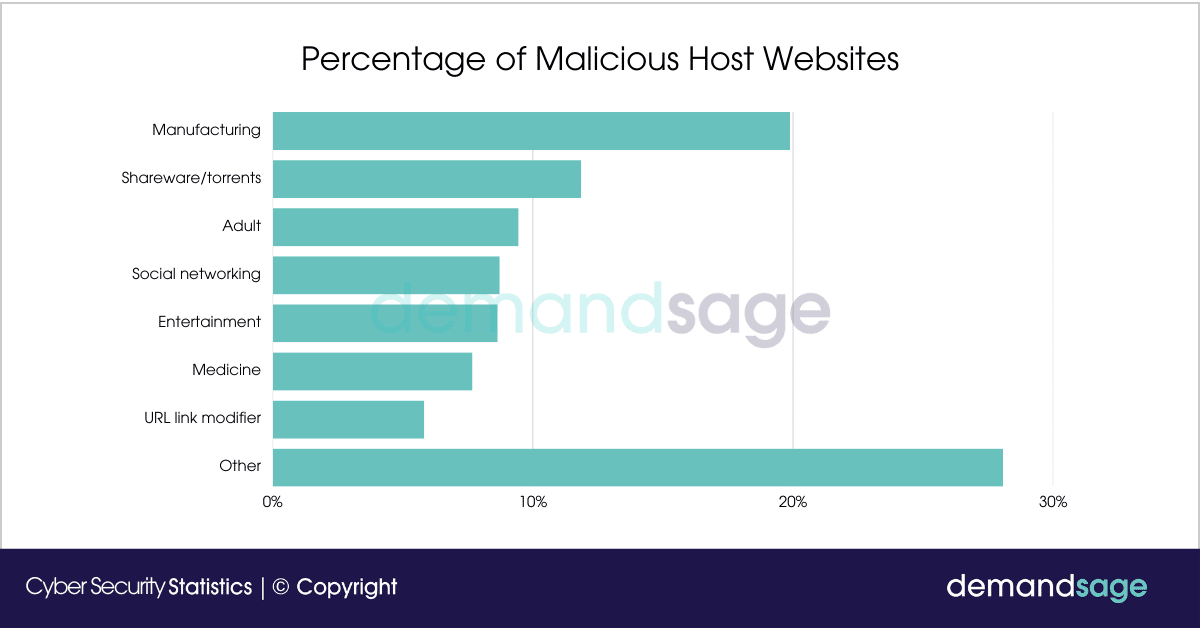
Web pages created to initiate unauthorized actions on users’ devices are commonly known as malicious websites. These sites may look legitimate or mimic reputable websites to deceive users into trusting them. They can be loaded with malware, phishing schemes, or scripts that exploit vulnerabilities in browsers and other software to perform malicious actions without the user’s consent or knowledge.
These fraudulent websites are a major risk to internet users, including individuals, organizations, and governments, and can engage in harmful activities, such as:
- Stealing personal and financial information
- Damaging computer systems and networks
- Using your resources without permission
- Undermining trust in safe online communication
8 Types of Malicious Websites
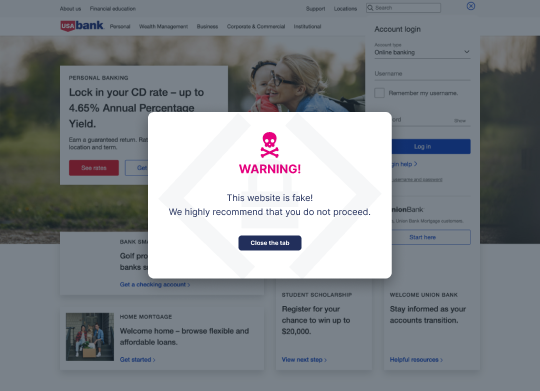
1. Phishing and Spoofing Websites
These sites deceive users into entering sensitive information by impersonating the appearance of legitimate websites. They leverage the trust users place in well-known brands or organizations, often employing URLs visually similar to those of legitimate sites to trick users.

2. Malware Distribution Sites
Websites in this category are set up to distribute malware. This can be achieved through direct downloads, where the site prompts users to download a malicious file, or through drive-by downloads that exploit vulnerabilities in the user’s browser or its plugins to install malware without the user’s consent.
Other versions of this fraud actively inject malware into visitors’ devices through compromised ads (malvertising), hidden iframes, or malicious scripts that execute upon page load.
3. Exploit Kits
These websites or web pages contain code designed to exploit vulnerabilities in web browsers, plugins, or other software on the visitor’s device. The goal is to automatically install malware on the device, often without the user’s knowledge.
4. Cryptojacking Websites
Cryptojacking sites secretly use a visitor’s computing power to mine cryptocurrency. It typically occurs through scripts that run automatically when the webpage is accessed, utilizing the device’s resources without the owner’s consent.
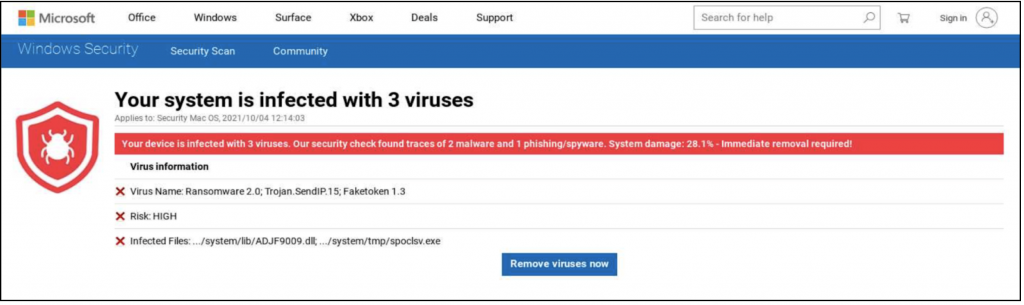
5. Scareware or Rogue Software Distribution Sites
Scareware sites convince users to download bogus security software or other utilities, which are either harmful or attempt to extort money by claiming to fix non-existent problems on the user’s device.
6. Content Injection and Compromised Websites
These are legitimate websites hacked to include malicious content. The websites have been modified to redirect users to malicious sites or to serve malware directly, often without the site owner’s knowledge.
7. Fake Update and Software Download Sites
Under the guise of necessary software updates or appealing applications, these websites mislead users into downloading malware that can lead to device compromise or data theft.
8. Scam Websites
Scam sites are designed to defraud users through a variety of schemes, such as offering too-good-to-be-true deals, fake lotteries, or fraudulent investment opportunities. They aim to steal money directly or gather personal information for financial fraud.
7 Ways to Quickly Detect Malicious Websites
1. Detect Spoofed Websites with Memcyco
For most threat intelligence and digital brand protection solutions, detecting an impersonated website doesn’t happen until it’s too late for the business and its customers. That’s why this insidious cyber threat requires innovative countermeasures.
Memcyco is recognized as the leading solution for protecting enterprises and their customers from website spoofing and brandjacking attacks in real time. Its approach focuses on immediately identifying and mitigating digital impersonation attacks as they happen.
Memcyco’s AI-based solution grants businesses full visibility and control of digital impersonation fraud before ATO, money theft, data breaches, and ransomware occur. The company’s unique ‘nano defender’ technology detects, protects, and responds to attacks as they unfold.
Using Memcyco’s solution, InfoSec, fraud, and digital business teams can see the full scope of the attack and customer identities, instantly disarming and locking out fraudsters. This way, Memcyco’s solutions help save millions in incident remediation costs while reducing the impact on customer satisfaction and brand reputation.
2. Employ Heuristic Analysis Techniques
Instead of using software, heuristic analysis (a.k.a. ‘the old-fashioned way’) is a technique that uses rules of thumb, experience, or common sense to detect malicious websites using human eyes and intelligence. This is where having a strong human firewall can increase your protection level.
Educated employees (and even customers) can employ heuristic analysis to check for these characteristics often found in harmful fake websites:
- Spelling or grammatical errors
- Poor or outdated design
- Broken or missing links
- Unusual or excessive pop-ups or ads
- Requests for unnecessary or sensitive information
- Offers that are too good to be true
- Lack of privacy policy or terms and conditions
3. Apply Advanced AI and Machine Learning (ML) Algorithms
AI and ML are powerful tools that help you detect fraudulent websites by autonomously predicting and identifying malicious patterns, behaviors, or anomalies. Here’s how they do it:
- AI models can be trained to predict attacks by feeding historical data of known malicious websites. These models can cross-reference websites against known blacklists and analyze their reputation scores based on various cybersecurity databases.
- The AI can scan the content of a webpage for suspicious elements, such as hidden iframes, suspicious scripts, or phishing forms.
- Monitoring the traffic to and from a website can provide insights. Unusually high traffic, especially from different geographical locations, can be a red flag.
- Algorithms that detect anomalies can identify deviations from normal behavior, which might indicate a website has been compromised or is inherently malicious.
- Using classification algorithms, certain third-party models can classify websites as malicious or benign based on the extracted features.
- NLP can be used to analyze the text on a website, looking for phishing attempts or misleading information.
4. Use URL Scanning and Analysis
URL scanning and analysis is a crucial method in detecting harmful fake websites. It’s about speed and accuracy—identifying and neutralizing threats before they can do harm.
Using URL scanning and analysis leverages several sophisticated techniques, often supported by AI and machine learning.
- Machine learning models can analyze the structure of a URL, looking for patterns often found in these websites, such as unusual lengths, domain name anomalies, or the use of special characters.
- The tool or system checks the domain against known malicious domains and assesses the domain’s age, as newly created domains are often used for malicious purposes.
Other URL scanning and analysis options include:
- Using APIs provided by third parties to create scripts (or develop your own custom scripts) to extract and analyze additional URL data.
- Configuring third-party browser extensions to automatically scan all URLs users visit in your network.
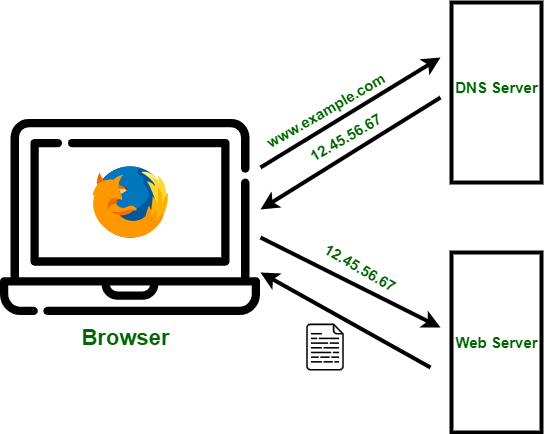
5. Investigate Deeper with DNS Analysis and Intelligence
DNS is the system responsible for translating domain names (www.example.com) into IP addresses (192.168.0.1) that computers can understand and communicate with. DNS analysis can help you detect malicious websites by leveraging DNS data to identify malicious activities.
To deepen your DNS investigation:
- Script automated WHOIS queries using third-party tools to gather detailed information about domain registrations.
- Analyze DNS query logs to spot unusual patterns, like a sudden increase in queries for unknown domains.
- Use DNS intelligence tools to filter and block fake sites.
6. Seek Out Sites with Threat Detection Software
Threat detection software uses various methods, such as signature-based, behavior-based, or reputation-based detection, to identify and classify malicious websites. They can also provide alerts, reports, or recommendations to help you handle the sites and improve your security posture.
Here’s how to maximize its potential:
- Use threat detection tools to perform deep scans tailored to your specific environment.
- Integrate threat detection software with Security Information and Event Management (SIEM) systems.
7. Scrutinize SSL Certificates
Despite common beliefs, SSL certificates are not foolproof. Closer scrutiny can help you detect dangerous, fraudulent websites by identifying any anomalies in the SSL certificates. These anomalies include expired, revoked, or self-signed certificates, mismatched or misspelled domain names, or weak encryption algorithms.
Here’s how you can enhance this process:
-
- Implement automated scripts to periodically check the SSL certificates of key websites your organization interacts with.
- Utilize SSL Certificate Transparency logs to monitor for newly issued certificates for your domains.
- Set up customized alerts for detecting anomalies in SSL certificates.
Protect Your Business by Detecting Malicious Websites
The variety of threats posed by malicious websites to your business and customers can’t be ignored, especially when 81% of consumers would stop engaging with a brand online after an attack. While numerous methods exist to detect these sites, not all are equally effective, efficient, or easy to implement.
This is where Memcyco comes in. It’s a user-friendly, affordable, and scalable solution to safeguard against account takeover attacks and website impersonation from fake sites. Memcyco’s real-time capability to identify and mitigate these cyber threats makes it crucial to any comprehensive cybersecurity strategy.
Contact Memcyco for a free demo to discover how the best defense against malicious brand impersonation websites protects your enterprise.