The image of the cyber attacker is changing. For years, the industry focused on email gateways and typo-squatted domains like citi-bank-security.com. But according to Tzoor Cohen, CTI Lead at Memcyco, the battleground has shifted.
In 2026, the most dangerous social engineering tactics typically don’t start in an inbox. They start on social media, utilize legitimate infrastructure like Bitly, and exploit the user interface (UI) of mobile devices to hide malicious intent. Attackers are no longer just relying on fear; they are leveraging gamification, “mystery boxes,” and algorithmic trust to bypass traditional security perimeters.
This article dissects the current attacker behavior, the industries most at risk, and the specific techniques that legacy threat intelligence tools are failing to detect.
The shift: from typosquatting to “random domain” attacks
For a decade, brand protection meant scanning for similar domains. Attackers would register facbook.com and hope a user clicked.
Cohen notes a fundamental shift: attackers are abandoning typosquatting for random, disposable domains. Instead of registering a look-alike domain that scanners can easily flag, attackers register generic domains (e.g., gibberish.com/safe-secure-login).
Why scanners miss this
Legacy tools look for brand names in the URL. If an attacker uses a random domain and hides the brand name behind a tokenized path (e.g., site.com/token=123xyz), scanners see nothing suspicious. The “social engineering” part – the convincing brand promise – happens entirely in the delivery message (SMS or Ad), not the URL itself.
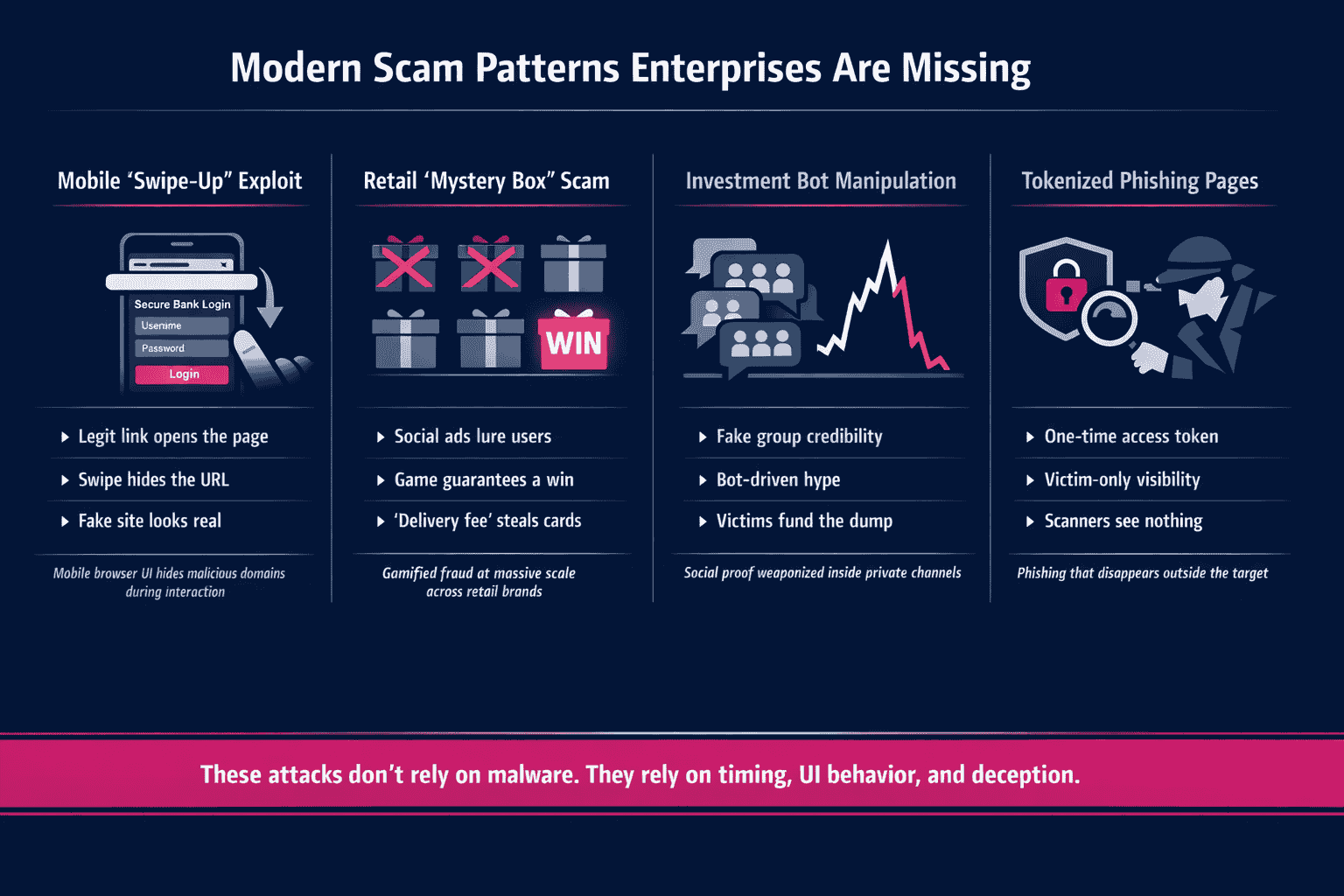
Top social engineering tactics for 2026
Based on intelligence from Memcyco’s research team, these are the dominant tactics defining the current threat landscape.
1. The “swipe-up” mobile exploit
Attackers are exploiting the native behavior of mobile browsers to mask phishing sites.
- The lure: A user receives an SMS or social ad with a legitimate shortened link (e.g., bit.ly/Citibank-Promo).
- The trick: The moment the user clicks and interacts with the page – specifically, the “swipe up” gesture to scroll – mobile browsers automatically hide the address bar to maximize screen real estate.
- The result: The victim sees a perfect replica of the bank’s site. The malicious URL (bad-site.com) is hidden by the browser’s own UI. The user feels safe because the initial link looked legitimate.
2. “Mystery box” gamification in retail
Retailers – specifically clothing brands like Zara, Mango, and Shein – are facing a wave of gamified attacks.
- The setup: Ads on social media promise “unclaimed packages” or “mystery boxes.”
- The game: The user clicks through to a site presenting nine boxes. The first two are always empty. The third always contains a “jackpot.”
- The hook: To claim the prize, the user must pay a small “delivery fee.” This harvests the credit card details. Cohen notes that these attacks are launched in massive batches, with hundreds of brands targeted on a single bulletproof hosting provider.
3. “Pump and dump” investment bots
In the banking and fintech sectors, attackers are moving into private WhatsApp and Telegram groups.
- The infiltration: Victims are added to investment groups filled with 200+ members.
- The social proof: Most “members” are bots that generate realistic chatter about market trends (e.g., Fed rates, stock movements) to build trust.
- The sting: The “mentor” advises everyone to buy a specific obscure stock. The attackers pump the price, the victims buy in, and the attackers dump their shares, crashing the value and stealing the liquidity.
4. Tokenized access blocking
To prevent security researchers and scanners from analyzing their sites, attackers now protect phishing pages with unique tokens.
- The mechanic: You cannot access the phishing site bad-site.com unless you have the specific, one-time token generated for your phone number.
- The impact: If a SOC analyst tries to visit the root domain to investigate, they see a 404 error or a blank page. The attack exists only for the victim, making it invisible to broad web scanners.
Which industries are targeted most by social engineering in 2026?
While every sector is at risk, attacker behavior varies by industry vertical.
- Fashion & Retail: The highest volume of attacks involves digital impersonation of fast-fashion brands. Attackers capitalize on the visual nature of these brands to create convincing fake ads on Instagram and TikTok.
- Banking & Wealth: The focus here is high-value account takeover (ATO). Attackers use “investment guru” personas to execute long-con social engineering scams that bypass technical controls like MFA.
- Logistics: “Missed delivery” scams remain prevalent, but they are evolving into the “Mystery Box” variant to target greed rather than just operational necessity.
Where do most social engineering attacks originate?
Geographic attribution is becoming less relevant as attackers utilize global infrastructure. Cohen emphasizes that Memcyco focuses on the infrastructure – the registrars and hosting providers – rather than the physical location of the hacker.
Attackers use Bulletproof Hosting providers that ignore takedown requests. They often register domains in bulk (e.g., 1,200 domains in a single afternoon) using privacy services. While the human behind the attack might be in the “usual suspect” regions, their digital footprint is global, often routing through residential proxies to mask their origin.
Conclusion: visibility is the only defense
The common thread across all these tactics – from “swipe-up” exploits to tokenized pages – is that they are designed to evade detection. They do not trigger WAFs, and they do not appear on threat intelligence feeds until it is too late.
To protect customers in 2026, enterprises must move beyond scanning the open web. They need real-time visibility into the sessions occurring on these fake sites. By detecting the attack the moment a user interacts with it (using embedded sensors like Nano Defender), organizations can alert victims before they swipe up, click the box, or transfer the funds.
Don’t let social engineering bypass your defenses
Attackers are evolving faster than scanners. It’s time to adopt a defense that sees what they are doing in real-time.
Contact Memcyco to learn how to detect “swipe-up” attacks and protect your customers from the next generation of social engineering.
Frequently Asked Questions
What are the top social engineering tactics by region for 2026?
While tactics are global, the themes are localized. In regions with high e-commerce penetration (like the US and UK), “Mystery Box” and retail gamification scams are dominant. In regions with high fintech adoption (like Israel and parts of Asia), “Pump and Dump” investment scams in private messaging groups (WhatsApp/Telegram) are the primary vector.
Why are traditional “Scan and Takedown” tools failing against these new tactics?
Traditional tools rely on finding “look-alike” domains (typosquatting). Modern attackers use random, unrelated domains (e.g., generic-host.com/login) that do not trigger brand keyword alerts. Furthermore, tactics like “Tokenized Access” ensure that scanners receive 404 errors, hiding the phishing content from everyone except the targeted victim.
How does the “Swipe-Up” exploit work on mobile?
Attackers send a link (often a legitimate Bitly link) via SMS. When the user clicks, the page loads. As soon as the user scrolls or “swipes up” to read the content, the mobile browser’s UI automatically hides the URL bar. This obscures the fact that the user is on a malicious domain, relying on the user’s trust in the initial SMS context.
Which industries are targeted most by social engineering in 2026?
Retail and Fashion face the highest volume of attacks due to the ease of replicating visual assets for fake ads. Banking and Wealth Management face the most sophisticated attacks, with “investment scams” designed to bypass MFA and steal significant funds through authorized push payments.
Can MFA prevent these social engineering attacks?
Not always. In scenarios like the “Pump and Dump” scam or “Mystery Box” payments, the user is often tricking themselves into authorizing a payment. They willingly undergo MFA to complete what they believe is a legitimate transaction. This is why MFA is not enough and intent-based detection is required.



















