Account takeover is usually and unsurprisingly approached as a security incident, yet much of the customer impact begins earlier in the journey, long before security teams detect or analyse the event. When users face friction, lockouts, or unexpected changes to their accounts, trust starts to erode. This makes the account takeover impact on customer experience a major determinant of brand trust and loyalty.
Most enterprises focus on fraud loss, case resolution, or credential misuse when managing ATO, which is understandable given how incidents appear in internal workflows. Yet customers evaluate the brand based on how safe and smooth the experience feels, not on which team handled the incident behind the scenes.
This gap between operational detection and customer experience impact shows why ATO should be viewed through both lenses, because the customer consequences often appear earlier and accrue differently from the security outcomes.
The CX Impact of ATO: Trust Loss, Friction, and Churn
Account takeover harms customer experience long before fraud is confirmed. It introduces incorrect lockouts, confusing error messages, and rising recovery friction that reduce confidence and push users away from the brand.
Customers experience ATO as a violation. Attackers often test reused passwords, take over profiles, redeem loyalty points, or change account settings. Even when the compromise begins on a spoofed page, customers believe the brand failed them. Their judgment is based on how the experience felt, not on where the attacker originated.
Trust declines rapidly when customers feel unsafe. Research shows that more than four in five users would stop using a business after an account compromise. The psychological shift is immediate: users disengage, reduce activity, or close accounts entirely. This is a CX outcome, not a technical one.
Friction drives similar consequences. When enterprises apply strict rules to stop ATO, legitimate users are frequently blocked or challenged. This creates false declines and increases the customer insult rate. The cost of this friction is high: data indicates that 40% of consumers will boycott a merchant entirely after just one false decline, effectively turning security measures into a churn driver.
Recovery also plays a central role. Lengthy reset flows, manual reviews, or repeated verification attempts frustrate users who are already anxious. In fact, friction is a primary conversion killer; research shows that up to 92% of users will abandon a purchase or session rather than go through a password reset process, proving that complex recovery flows directly impact revenue. Long recovery times correlate strongly with permanent churn. These costs rarely appear in fraud dashboards but carry substantial business impact.
Why ATO Signals Often Appear Before Traditional Controls Detect Them
Traditional controls identify ATO signals only after customers begin to experience friction or after misuse has already occurred. This timing problem is the main reason customer harm rises even in well-defended environments.
Many systems only evaluate risk after a login completes or after an action is taken inside the account. By that point, the experience has already deteriorated. The customer may be locked out, facing delays, or unsure whether their information is still safe.
Rules-based systems often target patterns that overlap with normal customer behavior. Device changes, travel, or infrequent visits are common but frequently flagged. This inflates false declines and forces digital teams to absorb the fallout.
Most importantly, users blame the brand for issues caused by spoofed pages or SEO poisoning. When attackers create lookalike sites that capture credentials, customers believe they were on the genuine site. They hold the brand accountable, even when the compromise happens entirely outside the company infrastructure.
This timing gap reflects the same upstream patterns seen across modern account takeover fraud, where impersonation and credential capture occur before authentication-based controls engage.
Many users never realise they logged into a spoofed page, which leads them to assume the brand failed to protect them.
To understand how these misleading pages capture customer traffic, see our guide on preventing ATO from SEO poisoning and fake search ads.
Why Digital Teams Should Treat ATO as a CX Priority
Digital teams control the journey moments where customers build trust or encounter issues. This makes ATO a direct CX concern that extends beyond the security domain.
ATO correlates directly with abandonment: Customers who experience account misuse often reduce activity or leave permanently. This appears in drop-offs, session abandonment, declining participation in loyalty programs, and reduced engagement.
ATO drives operational load: When users cannot regain access or face repeated friction, they open support cases. High recovery volume increases operational expense and slows response times, creating additional frustration.
ATO affects brand equity: Public complaints about lost points, unexpected resets, or slow recovery can spread quickly. Travel, banking, and retail brands face the greatest risk, because customers associate these accounts with money, identity, or personal milestones.
ATO impacts long-term revenue: Frustrated customers do not complete purchases. Repeated friction reduces conversion and undermines loyalty marketing. Enterprises lose immediate sales and the future revenue tied to customer lifetime value.
Digital leaders who frame ATO as a CX risk, not only a security issue, gain clearer visibility into the business impact.
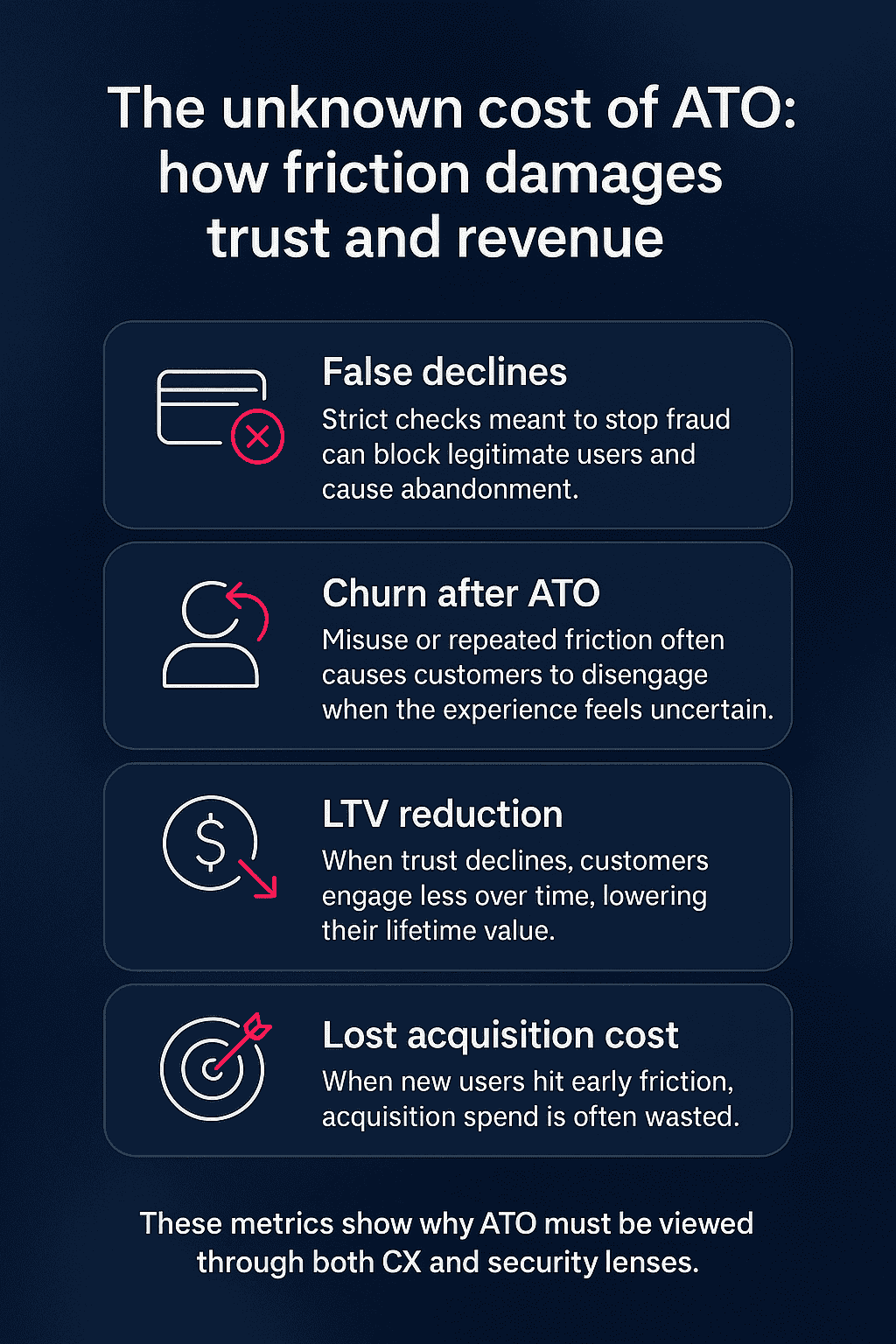
The Metrics That Reveal the CX Impact of ATO
When enterprises analyze ATO through a CX lens, several metrics emerge as more predictive than traditional fraud loss reporting.
Customer insult rate
This measures how often legitimate customers are incorrectly blocked or challenged. High insult rates correlate with churn spikes and negative sentiment.
False declines
Valid actions rejected as fraud often result in abandoned sessions and reduced loyalty. Across industries, the financial loss from false declines often exceeds confirmed fraud loss.
Churn after ATO
Users who experience account misuse or heavy friction commonly leave the platform. This loss erodes all prior acquisition investment.
Customer lifetime value reduction
Every insulted or compromised customer reduces LTV. This is the most reliable financial indicator of ATO-related CX degradation.
Lost acquisition cost
When newly acquired users encounter friction or false declines, the acquisition investment is wasted.
These metrics allow fraud, digital, and security teams to operate with shared accountability.
How Memcyco Helps Enterprises Reduce CX Damage from ATO
Memcyco helps enterprises reduce the customer experience impact of ATO by giving teams earlier visibility into ATO-related behaviors during login attempts. This allows organizations to protect users before friction, confusion, or trust loss occurs.
Spoofed or cloned versions of a site often appear legitimate enough that customers cannot distinguish them from the real property. We explore how attackers build these convincing replicas in our analysis of website cloning attacks and why they evade brand protection tools.
1. Visibility into spoofed or impersonated pages
Memcyco shows when users interact with cloned or spoofed versions of a brand site. This helps teams identify targeted users and prevent trust erosion.
2. Detection of suspicious devices attempting to log in
Signals collected during login attempts reveal devices linked to phishing activity or attempts to access multiple accounts. This supports earlier decision-making without adding unnecessary friction for valid users.
3. Real-time identification of targeted users
Enterprises can see which users exposed credentials on phishing sites or encountered malicious redirects. This helps protect victims from account lockouts or incorrect challenges. Some of these unnecessary challenges arise from credential testing activity that resembles normal user behaviour.
Our breakdown of ways to combat credential stuffing shows how these patterns develop and why they often trigger friction for legitimate users.
4. Protection against credential testing
Memcyco detects repeated access attempts from the same device across multiple accounts. This reduces reliance on blunt rules that frustrate legitimate customers.
These capabilities help enterprises intervene earlier in the customer journey, reducing false declines and preventing CX failures that would otherwise drive abandonment and churn.
The Bottom Line: ATO Requires Both CX and Security Alignment
ATO incidents create early experience impacts for customers and later operational impacts for security teams. Addressing both areas in tandem helps reduce friction, preserve trust, and improve outcomes across the organisation.
What This Means for Enterprises
Teams that gain earlier insight into ATO-related activity are better equipped to reduce friction, protect customer trust, and respond effectively when issues arise. The next step is ensuring this visibility is available at the moment users engage.
Book a demo and discover how Memcyco delivers the critical real-time visibility needed to keep fraudsters out, while maintaining frictionless access for legitimate users.
FAQs
How does account takeover impact customer experience?
Account takeover often creates friction, lockouts, or confusing messages before the incident is detected internally. These early issues reduce customer confidence, increase frustration, and frequently lead to session abandonment or long-term disengagement.
Why do customers leave after an account takeover incident?
Customers typically interpret account misuse as a failure of brand protection. Even if the compromise started on a spoofed page, they associate the event with the brand and may stop using the service due to uncertainty, inconvenience, or repeated friction.
What causes false declines during login or account access?
False declines happen when security checks flag legitimate behaviour as suspicious. Device changes, travel, or infrequent visits can resemble risky patterns, creating unnecessary friction that leads to session abandonment and lower loyalty.
Why do some ATO attempts get detected late?
Many systems evaluate risk after the login step or during later actions. By the time an alert appears, customers may already have experienced friction, delays, or confusing error states, which contributes to frustration and churn.
Which metrics help measure the customer impact of ATO?
Customer insult rate, false declines, churn after ATO, lifetime value reduction, and recovery time offer a clearer view of how security events influence customer behaviour and long-term revenue outcomes.
How can companies reduce customer friction related to ATO?
Earlier visibility into ATO-related signals helps teams intervene before customers encounter uncertainty or unnecessary challenges. Reducing friction at these early stages helps preserve trust and stabilise engagement.



















