Picture this: A loyal customer urgently searches for a product they’ve purchased from your site before. Instead of landing on your official site, they click an ad for a fake version of your domain, created by threat actors and placed prominently on search engines. Within minutes, their card details are stolen. What can you do? Start with a domain takedown service.
TL;DR: A domain takedown service identifies and removes malicious or spoofed websites impersonating your brand, protecting customers and preventing fraud.
What Is a Domain Takedown Service?
A domain takedown service identifies malicious or spoofed domains impersonating your brand and works with registrars, hosts, and authorities to remove them. These services help reduce financial losses, protect customer trust, and limit your digital attack surface.
5 Essential Features of a Domain Takedown Solution
- Threat Intelligence – Must detect phishing, typosquatting, and fake domains in real-time.
- Fast Response – Speed matters. The quicker a takedown happens, the less harm it does.
- Global Jurisdiction Reach – The service must coordinate with providers across all regions.
- Legal Expertise – Especially important for navigating takedown processes across jurisdictions.
- Post-Takedown Monitoring – Prevents domains from popping back up under new aliases.
2025’s Best Domain Takedown Services
These providers represent some of the most prominent domain takedown solutions available in 2025. However, each has important limitations businesses should consider when selecting protection against brand impersonation threats. This vendor comparison is based on publicly available information and user-reported feedback. The information presented, and its accuracy, is relevant to the time of publishing and specific details may have changed in the time elapsed since. Memcyco has not independently validated all third-party vendor capabilities or claims.
Top 10 Domain Takedown Services
1. Memcyco Real-Time Digital Impersonation, Phishing and Account Takeover (ATO) Protection + Automated Takedown
Memcyco predicts ATO, phishing and digital impersonation attacks, protecting companies and their customers from digital fraud. It is the only solution that provides real-time victim identification, preemptive ATO prevention, and credential deception technology, offering unmatched visibility into evolving threats. With its agentless deployment, Memcyco’s solution ensures customer protection while reducing fraud-related losses, strengthening compliance readiness, and delivering immediate ROI.
Best for: Combining real-time digital impersonation detection, customer ATO protection, and automated takedown — all in one agentless platform.
Main Features:
- Real-time detection of phishing and impersonation attempts
- Identifies individual scam victims during active attacks
- Replaces stolen credentials with decoy data to block access and expose attackers
- Predicts customer ATO attempts based on device behavior and attack patterns
- Prevents SEO poisoning and search hijacking by fake domains
- Agentless deployment via site code or WAF — no user involvement needed
What Memcyco Customers Say:
“What I love most about Memcyco is how it gives us pre-emptive foresight of ATOs in-the-making with real-time visibility into phishing attacks and impersonation scams before they hit our customers. Even if customers fall for scams, Memcyco dismantles card data and credentials theft attempts at the moment of impact before they can do damage“
Source: G2
— Oren. K, CEO | Enterprise > 1000 employees
Price: By inquiry
2. Red Points Post-Incident Domain Takedown Platform
Red Points is positioned as a brand protection platform focused on digital IP enforcement. It scans for infringing content, domains, and product listings across marketplaces and issues automated takedown requests based on pre-set rules.
Limitations: No real-time user protection; primarily focused on domain removal post-incident
Note: In 2022, Red Points was named in a defamation lawsuit related to a disputed DMCA takedown. The case proceeded past a motion to dismiss.
Main Features:
- Detects fake sites across search, social, and registrars
- Automated alerts and reporting tools
Price: Custom pricing
3. BrandShield Broad-Scope Monitoring and Takedown
BrandShield tracks domain impersonation, fake social profiles, and fraudulent ads using keyword detection and brand monitoring tools. Its platform is used by large brands looking to respond to impersonation threats across multiple online channels.
Limitations: Does not provide in-browser protection or live user warnings; response is post-event.
Note: In December 2024, BrandShield’s enforcement actions led to the temporary takedown of indie game platform Itch.io. The incident raised questions about Brandshield’s takedown accuracy.
Main Features:
- AI-powered detection and domain takedown
- Works across multiple online properties
Price: By request
4. ZeroFox Threat Intelligence and Automated Takedowns
ZeroFox offers broad digital risk protection that includes impersonation detection, domain monitoring, and takedown services. Its platform is designed for enterprises that want threat intelligence alongside reactive enforcement.
Limitations: Strong in threat automation and surface monitoring, but lacks real-time user protection or impersonation disruption
Main Features:
- Uses a Global Disruption Network to flag emerging threats
- In-platform submission of takedown requests
Price: Variable
5. PhishLabs Domain Intelligence and Incident Validation

Now a HelpSystems company, PhishLabs specializes in phishing site detection, intelligence gathering, and takedown services. The platform provides domain insights and alerting, often used by security teams as part of threat monitoring workflows.
Limitations: Focuses on monitoring and data analysis without real-time takedown or user protection
Main Features:
- Analyzes DNS data, SSL logs, and certificate records
- Expert-driven verification to reduce false positives
Price: By request
6. PhishFort Targeted Takedown for Crypto and Digital Brands
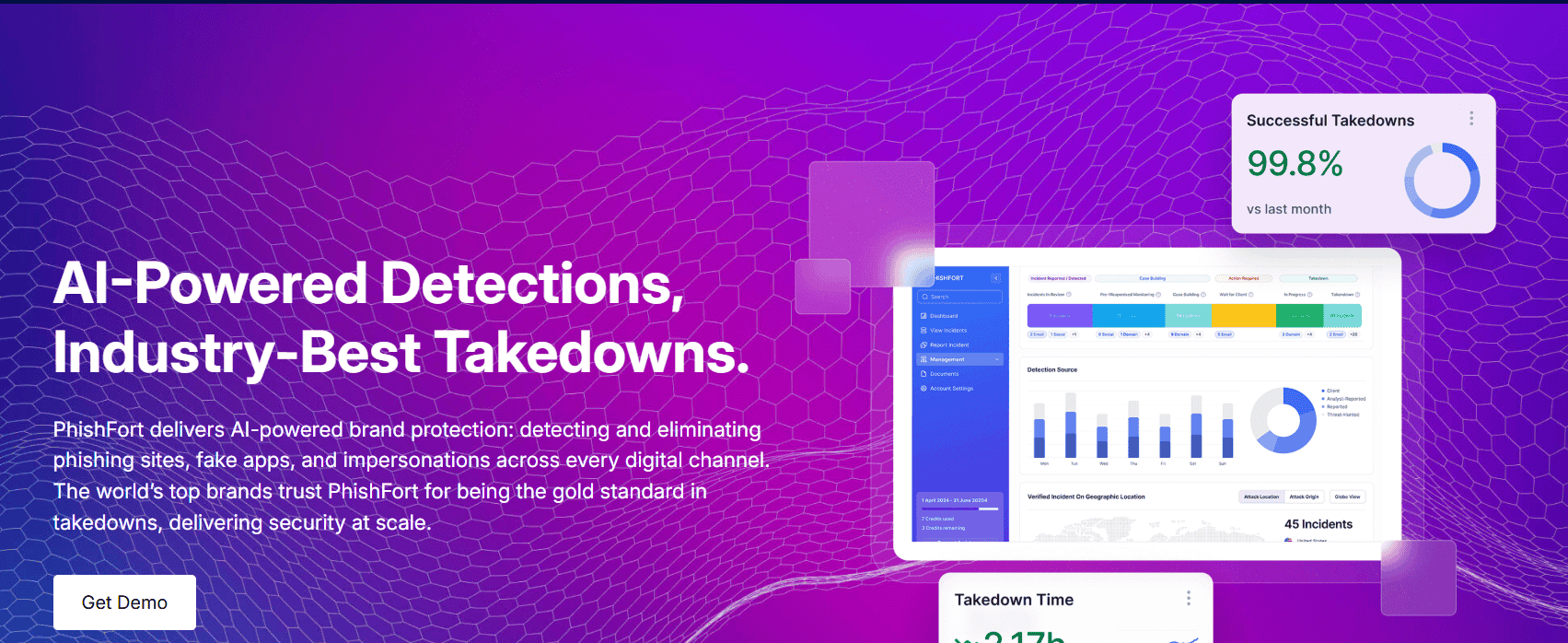
PhishFort offers takedown services focused on fintech, crypto, and other high-risk industries. It specializes in detecting phishing sites, scam mobile apps, and impersonating domains, with streamlined escalation and takedown workflows for fast-moving threats.
Limitations: Primarily reactive; lacks proactive disruption or in-browser user protection
Main Features:
- Focused protection for fintech, crypto, and high-risk sectors
- Takedown services across web, mobile, and social media
- Automated DMCA workflows
- Coordinates directly with registrars, hosts, and app platforms
Price: Custom pricing
7. Red Sift Brand Trust Scalable Detection Across Channels
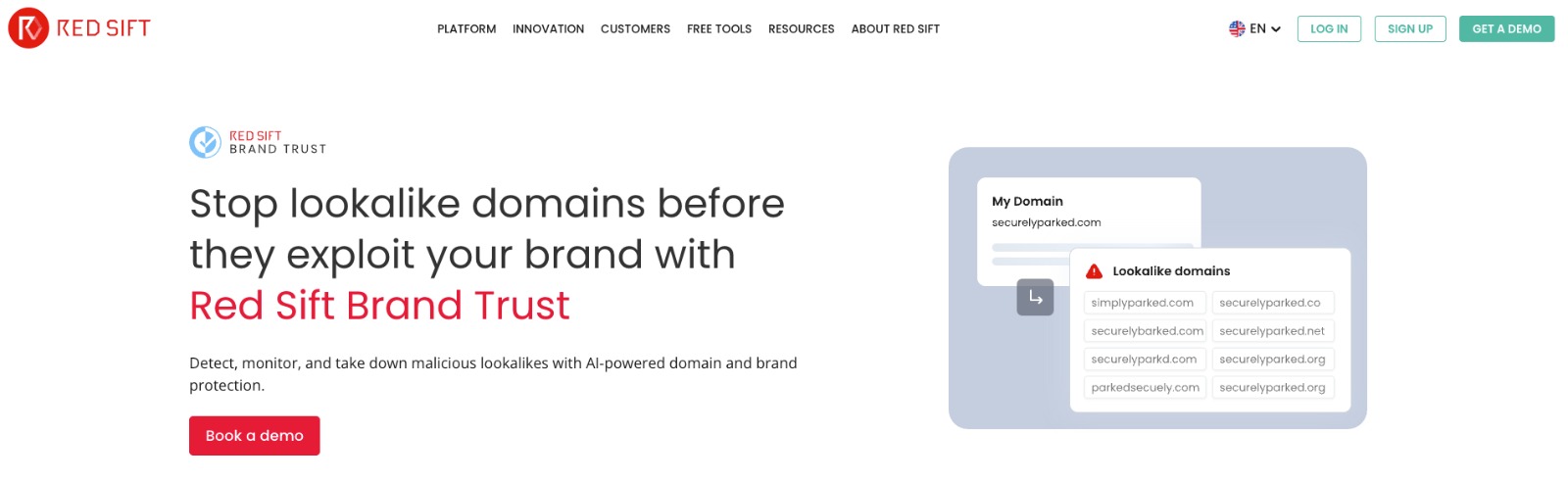
Red Sift’s Brand Trust platform monitors domain registration activity to detect and respond to lookalike domains. It integrates with DMARC and other email security controls to enhance visibility and protect brand-owned domains from abuse.
Limitations: No tools for detecting digital impersonation attempts, or protecting customer accounts
Main Features:
- Monitors up to 150 million domains daily
- Machine vision logo matching and GenAI
Price: By inquiry
8. IntSights (Now part of Rapid7) Legal and Workflow-Focused Takedown Support
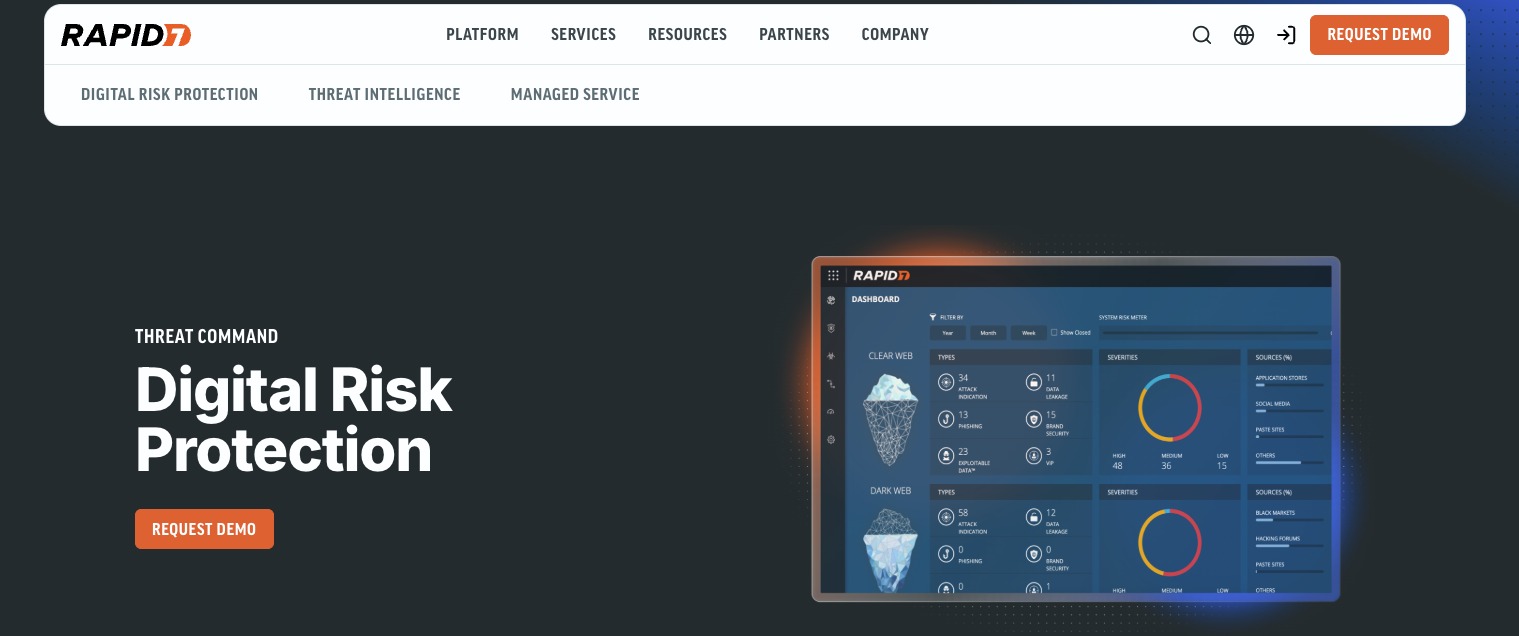
IntSights, now part of Rapid7’s Threat Command platform, provides external threat intelligence and dark web monitoring. Its takedown workflows are used to disrupt phishing domains, credential dumps, and impersonation attacks uncovered through threat research.
Limitations: Workflow-focused; does not include real-time attack detection or interception
Main Features:
- Manages takedowns across web, social, paste sites, app stores
- Human analysts streamline workflows
Price: Not listed
9. Netcraft Large-Scale Scanning and Takedown Notification
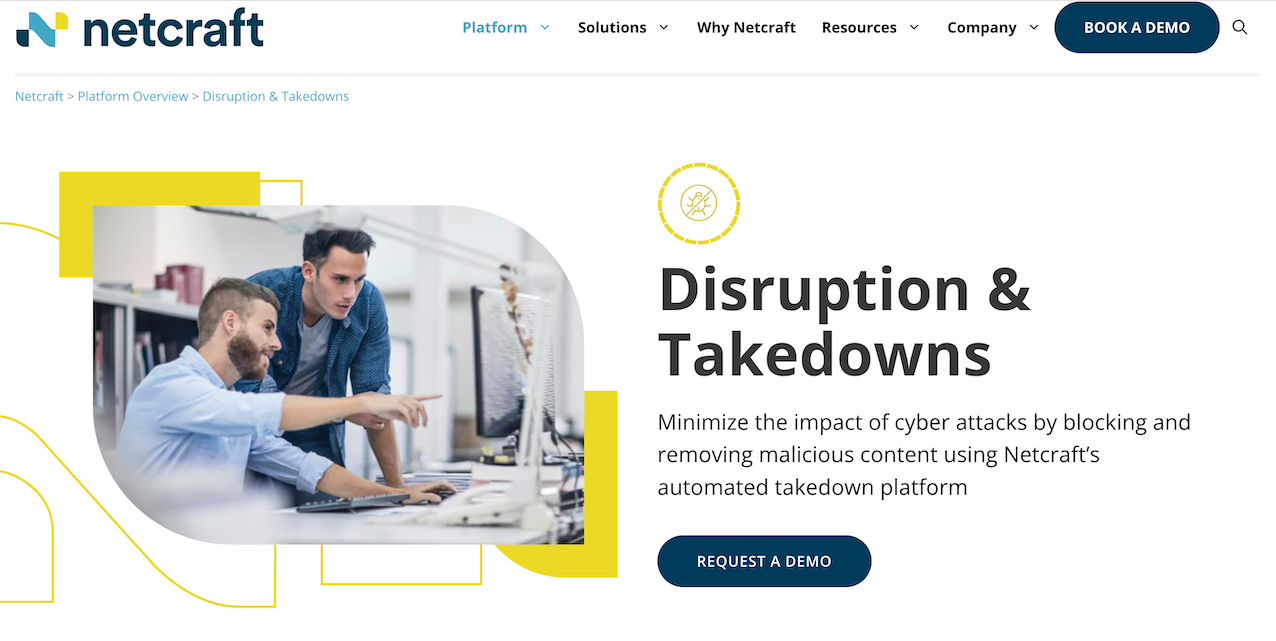
Netcraft is one of the longest-running anti-phishing and takedown services, known for large-scale threat scanning and automated reporting. It now incorporates FraudWatch’s SOC capabilities to expand its takedown responsiveness across time zones.
Limitations: No real-time threat mitigation or user protection capabilities
Main Features:
- Scans millions of URLs per day
- Notifies registrars and tracks takedowns post-resolution
Price: Upon request
10. Bolster AI-First, Automated Phishing Takedowns
Bolster offers an AI-powered platform for detecting and removing phishing sites, counterfeit domains, and scam content. It focuses on high-speed detection and automated takedowns across websites, social media, and marketplaces.
Limitations: Automates domain removals but lacks real-time protection or attacker disruption
Main Features:
- AI-based triage and auto-response
- Monitors 12+ social networks and 400+ app stores
Price: By request
FAQs About Domain Takedown Services
What is a domain takedown service?
A domain takedown service identifies and removes fake or malicious websites that impersonate your brand.
How can I remove a fake website?
To remove a fake website, follow these steps:
- Identify the fraudulent site impersonating your brand.
- Collect evidence, such as screenshots and URLs.
- Report the site to the hosting provider or domain registrar with the evidence.
- Submit a takedown request through the appropriate legal channels, like a DMCA notice.
- Monitor the situation to ensure the site is taken down and doesn’t reappear.
How long does it take to take down a fake website?
It usually takes between 24 and 72 hours to take down a fake website, but it can sometimes take longer depending on the hosting provider’s or registrar’s response time. Memcyco, by contrast, offers automated takedown workflows and real-time protection that begins before a site is even removed.
What are the top domain takedown services in 2025?
Leading domain takedown services in 2025 include Memcyco, PhishFort, Netcraft, and IntSights, among others. Memcyco stands out by offering real-time digital impersonation, phishing, and ATO protection, while others typically focus only on scanning and takedown after fake sites are already live and harvesting customer credentials.
Why Takedown Alone Isn’t Enough (and How to Go Further)
Even the best domain takedown services can take 24–72 hours to remove malicious sites. In that critical window, customers can still be misled, phished, or financially harmed. Worse, some domains return under new aliases, and not all registrars cooperate.
That’s why Memcyco doesn’t just take down fake sites — Memcyco’s solution protects customer accounts from impersonation attacks as they unfold. In real time, Memcyco:
- Identifies victims in real-time, providing visibility into each individual user caught in a phishing trap
- Intercepts credential theft with marked decoy data that blocks access and reveals attackers’ identities
- Detects ATO threats early, using predictive intelligence before harm occurs
- Prevents SEO poisoning, stopping fake sites from outranking legitimate ones
- Deceives attackers, bombarding impersonation sites with artificial data to derail campaigns.
That’s how Memcyco closes the phishing and customer ATO gap before takedown even starts. Book a Memcyco product tour and discover what truly preemptive, predictive and proactive customer ATO defense looks like.



















