If you give attackers an inch, they will take a mile. That’s essentially what happens when there are minor flaws in your web applications – these flaws leave one inch of your system’s doors open. Before you know it, sophisticated threats like directory traversal come crawling.
Currently, there are 55 different directory traversal vulnerabilities in CISA’s Known Exploited Vulnerabilities (KEV) catalog. Though protection methods are known, bad actors are still exploiting these vulnerabilities to steal data, compromise systems, and open a gateway to website spoofing.
What is Directory Traversal?
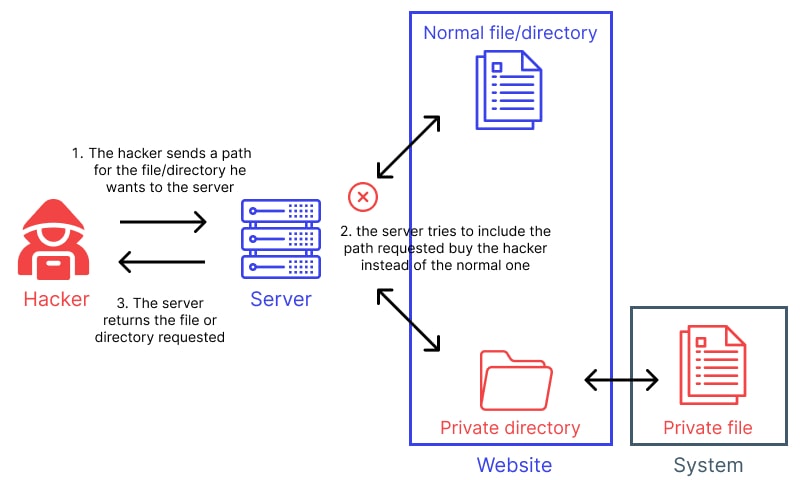
Directory traversal is a cyberattack where malicious actors exploit vulnerabilities in interactions between web servers and file systems, accessing files beyond an application’s intended scope. This attack capitalizes on mishandled user inputs, often related to file paths or directory references.
This security flaw is often called path traversal, which targets files and directories beyond the web’s primary directory. By altering variables linked to files using patterns like “dot-dot-slash (../)” and similar sequences or employing absolute file paths, attackers could potentially reach any file or directory on the system. This includes vital system files, application source codes, configurations, and databases.
For instance, consider a web application that takes a filename as a parameter to display that file’s contents. If the application does not correctly sanitize the input, an attacker can provide input like “../etc/passwd” to access the password file on a UNIX system. Attacks can then use their access to sensitive web files to steal data, compromise systems, or even create fake websites.
In simple terms:
- A web server typically serves files from a specific directory (e.g., a “webroot”).
- If an attacker can trick the server into fetching files from outside this directory, they might access sensitive files.
How does Directory Traversal work?
Directory traversal works via a series of carefully crafted techniques:
- Identifying user input interactions – The attacker identifies the places of the application that allow user interactions, such as inputs like filenames, paths, file uploads, or other data related to files.
- Exploring for improper input handling—They look for places where the inputs provided by users aren’t properly validated or sanitized. There’s no way to verify that the input adheres to expected constraints without proper validations, making the system vulnerable to traversal attempts.
- Traversal manipulation – The attacker takes advantage of the lack of input validation. By inputting carefully crafted sequences of characters, such as “../” or “%2e%2e%2f”, they trick the application into navigating beyond its intended scope.
- Unauthorized access—The manipulated input allows the attacker to move up directory levels, accessing directories and files they shouldn’t have permission to view. Depending on the system’s setup, this can expose sensitive data and configurations or even give the attacker the ability to execute or manipulate specific files.
For example, consider an application with a weak file upload mechanism. If the application allows file uploads without proper validation, attackers can upload a malicious file with a name containing traversal sequences. Then, when the application attempts to access the uploaded file, it might inadvertently give the attacker access to other files.
These attacks are similar to SQL injections in some ways, but SQL injections are mainly executed targeting databases, while directory traversals focus on file and directory access.
How is directory traversal a gateway to website spoofing?
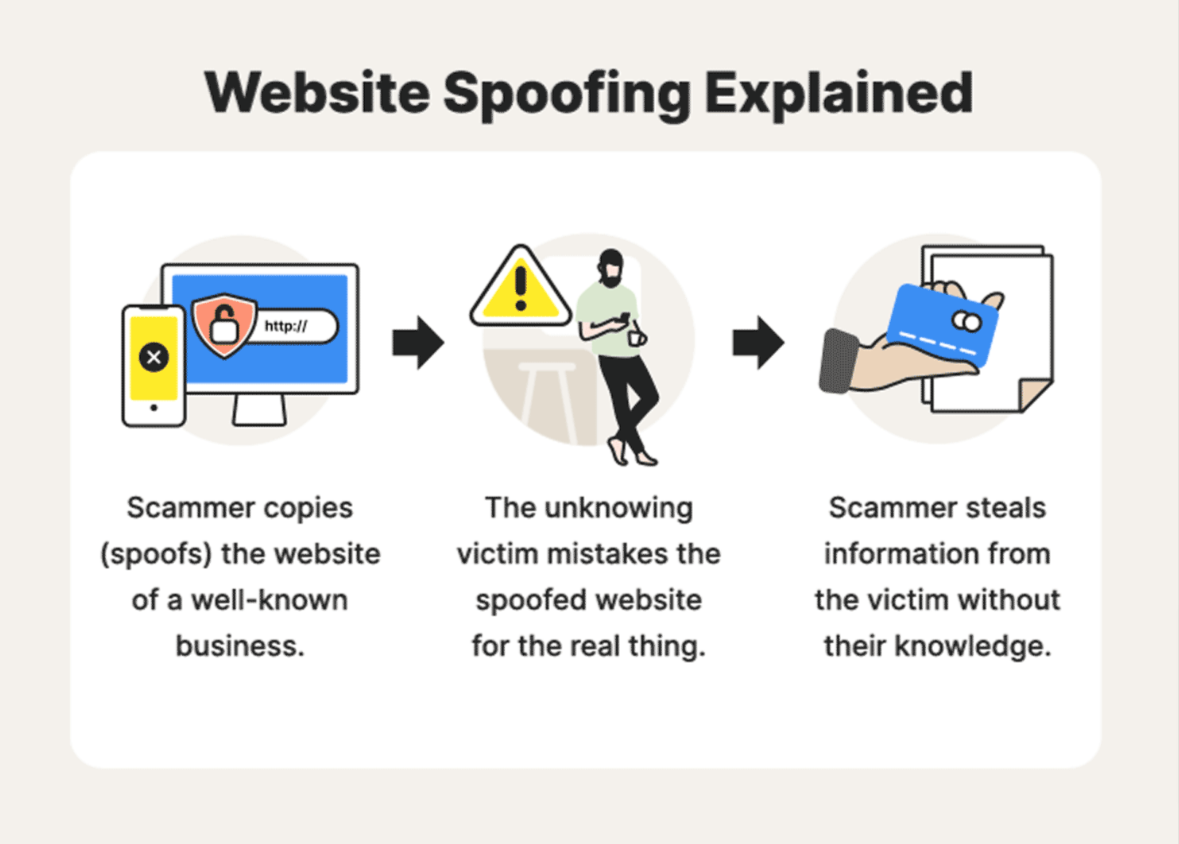
Website spoofing refers to creating a fraudulent website to mimic a legitimate site. The primary goal of spoofing is typically to deceive users into believing they are interacting with a legitimate website, usually with the intent of hackers stealing sensitive data, such as login credentials, credit card numbers, or personal information.
A successful directory traversal attack can serve as a conduit for website spoofing. Here’s how:
- Exposing Branded Assets: A directory traversal attack can expose brand details like logos, banners, and marketing materials to the public, allowing spoofers to interfere with your lead generation strategy and create more convincing counterfeit websites.
- Access to Email Templates: A directory traversal breach exposes official email templates and letterheads, allowing attackers to orchestrate convincing phishing attacks.
- Redirects and Web Forwarding: Understanding a website’s directory structure allows attackers to create highly convincing spoofs and implement redirects, diverting unsuspecting users to scam sites.
- Compromising Scripts or Pages: Manipulation scripts or pages through directory traversal attacks helps attackers extract sensitive user data, which can be used to refine spoofed sites, making them appear even more authentic to targeted users.
Moreover, by gaining insights into server-side functionalities through directory traversal, attackers can closely mirror website behaviors, such as form submissions and user interaction sequences.
This enhanced mimicry increases the chances of users falling prey to the spoofed site and strengthens the attackers’ ability to bypass specific security tools. Expert web development teams may be able to support you with input validation and secure coding standards, but you’re still vulnerable without advanced detection mechanisms.
In essence, directory traversal can arm spoofers with the tools and knowledge they need to create alarmingly accurate facsimiles of legitimate sites, escalating the potential damage of website spoofing attacks.
What are the risks of Directory Traversal attacks?
Directory traversal attacks can lead to:
- Data Theft: Exposure and loss of sensitive data, such as user credentials, financial data, proprietary source code, or confidential documents.
- Unauthorized Access: Attackers can gain access to resources like file storage and servers.
- Data Manipulations: Attackers can change the data, causing inaccuracies, data corruption, or system malfunctions.
- DDoS Attacks: Attackers can cause a Distributed Denial of Service (DDoS) by overloading servers through simultaneous access to numerous files or resources.
- Financial Losses: Organizations can experience economic losses due to legal cases, remediation steps, and business losses.
- Policy Violations: Organizations may fail to comply with legal regulations like GDPR or independent audits like SOC 2.
How can you detect and prevent Directory Traversal attacks?
Detecting directory traversal attacks requires vigilant monitoring of user input to detect suspicious input strings that might indicate traversal attempts. Log analysis can also help: by regularly reviewing application logs, organizations can spot unusual access patterns or unauthorized file access attempts, such as multiple requests to access sensitive files with paths like “/path/to/sensitive/files/../../../etc/password.”
Another vital aspect is URL encoding analysis. Malicious actors often use encoded characters to manipulate file paths and bypass input filters. For example, the string “%2e%2e%2f” is an encoded version of the “../” directory traversal, and its presence within a URL or input could indicate a directory traversal attack. But better than being able to detect these attacks swiftly is ensuring they don’t happen in the first place.
7 Ways to Mitigate Directory Traversal Attacks
Although detection and prevention methods provide a significant level of security, we also need to be aware of mitigation methods to proactively address the threats actively exploiting vulnerabilities.
Here’s a set of effective mitigation techniques you can use for directory traversal attacks:
1. Least Privilege Principle
The least privilege principle ensures that users and applications have only the necessary permissions to access resources. For example, if a user needs read-only access to a specific directory, the least privilege approach ensures they don’t have unnecessary write or execute permissions.
In the Unix environment, you can use the chmod command to set permissions. This command removes write and execute permissions for others.
chmod o-wx /path/to/sensitive/directory
2. Disable Directory Listing
Turning off directory listing in your web servers helps prevent attackers from gaining insights into your directory structure. This simple step will stop displaying the directory’s content when an attacker tries to access a directory without a specific file name.
If you are using an Apache web server, you can turn off the directory listing by including the below line:
Options -Indexes
3. Implement Proper Error Handling
Use error messages that do not reveal sensitive information. For example, do not display the names or paths of files when displaying an error for a missing file. Instead, provide a generic message like “Resource not available.”
4. Use Chroot Jails
Chroot jails allow you to restrict applications to designated directories. This helps isolate potential threats and prevents them from traversing beyond their designated boundaries.
In Linux, you can create a chroot jail using the below command:
chroot /path/to/jail /bin/bash
5. Regular Security Auditing and Monitoring
Real-time monitoring will help detect directory traversal attacks in their early stages before they significantly impact your application’s security. You can use tools like logwatch to set up alerts for unusual system access patterns.
# Install Logwatch sudo apt-get install logwatch # On Debian/Ubuntu sudo yum install logwatch # On CentOS/RHEL
# Configure Logwatch: Customize the Logwatch configuration file to include the logs you want to monitor. Edit /etc/logwatch/conf/logwatch.conf and add relevant log paths:
LogDir = /var/log LogFile = secure # Run Logwatch sudo logwatch --mailto your@email.com --detail High
6. Use Security Frameworks and Libraries
Use well-established security frameworks and libraries that have been battle-tested. These resources offer pre-built solutions that can substantially enhance your defenses. For example, Django is an excellent Python framework with built-in protections against directory traversal attacks.
7. File Upload Security
File uploads often serve as potential entry points for attackers. Implement strict security measures to validate and sanitize uploaded files, preventing attackers from exploiting these avenues.
The below example shows how to validate uploaded files using JavaScript in a web application:
const allowedTypes = [‘jpg’, ‘png’, ‘pdf’];
document.getElementById(‘fileInput’).addEventListener(‘change’, event => {
const uploadedFile = event.target.files[0];
if (!uploadedFile) {
return;
}
const fileExtension = uploadedFile.name.split(‘.’).pop().toLowerCase();
if (!allowedTypes.includes(fileExtension)) {
alert(‘Invalid file type. Please upload a JPG, PNG, or PDF file.’);
event.target.value = ”; // Clear the selected file
}
});
Our free PDF download, Directory Traversal Cheat Sheet for 2024, provides a detailed cheat sheet outlining these mitigation techniques and corresponding code samples.
Download your free Directory Traversal Cheat Sheet for 2024
Memcyco: Your Best Defense Against Website Spoofing Via Directory Traversal
As the CISA states, directory traversal is still a significant threat to organizations in 2024. It can infiltrate systems, compromise data, and aid in brand scams and website spoofing attacks. While traditional protection methods are essential, innovative tools like Memcyco provide more robust security for digital assets.
Memcyco’s Digital Risk Protection (DRP) solutions monitor real-time website interactions and detect abnormal behavior patterns, such as unauthorized file access attempts for website spoofing. Real-time alerts enable swift action, helping you prevent access to sensitive directories and file manipulation.
Plus, Memcyco’s behavior analytics capabilities offer detailed information on the attacker’s device and location, giving you complete visibility of the attack attempt and how it unfolds. Schedule a demo to see how it works.
![Directory Traversal Cheat Sheet for 2024 [PDF Download]](/wp-content/uploads/2023/10/website-post-Thumbnail_-Directory-Traversal-Cheat-Sheet-for-2024-PDF-Download.png)