How well can your C-level executives trust their employees are who they say they are? Cybercriminals bank on employees, specifically CxOs, abiding by management team requests.
Among the over 3 billion phishing emails sent daily, executives receive whaling attack emails once every 24 days, with 59% citing they’ve fallen victim to whaling attacks. Between Q1 2020 and Q1 2021, executive impersonations from whaling increased 131%. These attacks cost enterprises upwards of $1.8 billion in stolen assets, financial loss, fines, reputational damage, and business disruption.
To prevent upper management from becoming the next big catch, arm yourself with the basics of whaling phishing attacks. Learn what they are, how they work, and the damage they cause. Then, follow our eight steps to prevent your employees from falling hook, line, and sinker to their lures.
What is Whaling?
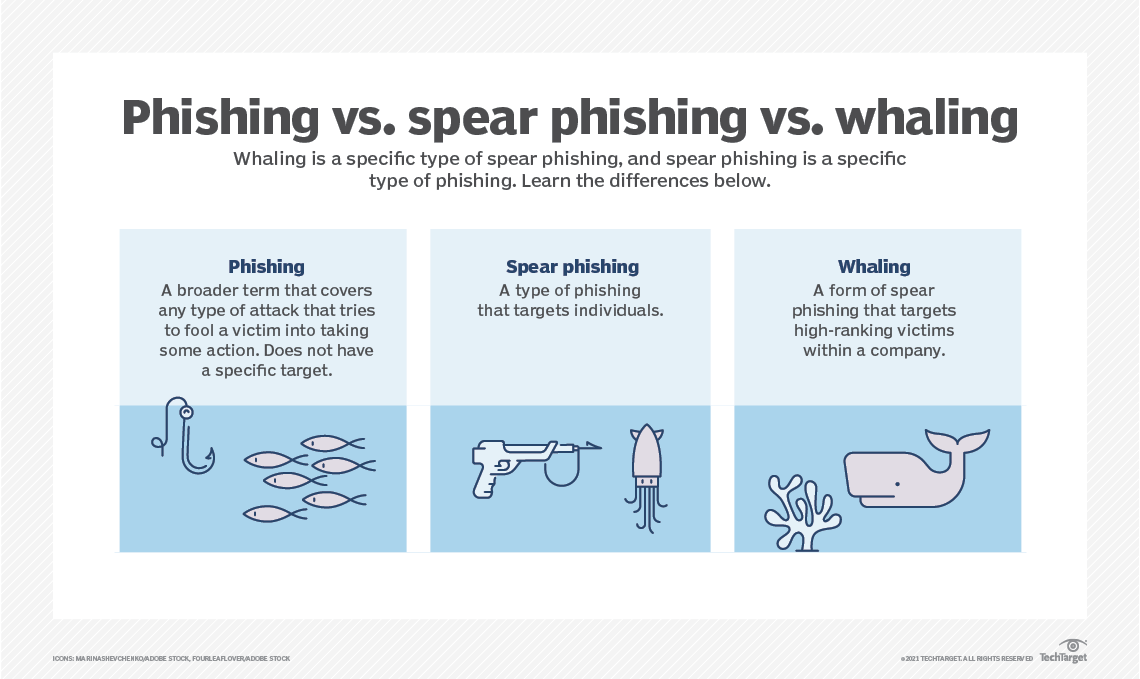
Whaling is targeted social engineering or phishing, called spear phishing, that aims to access highly confidential and sensitive information. Like phishing, spear phishing uses email or other communication channels to conduct an attack. Where phishing targets a broad audience from a well-known brand or company, spear phishing impersonates someone known personally to the target.
Spear phishing becomes whaling when cyber criminals target C-suite executives and others in upper management with access to highly sensitive and confidential information that can lead to a big pay-off. Whaling is often confused with a business email compromise (BEC), in which attackers disguise themselves as an executive. Both types of spear phishing take advantage of employees by tricking them to take some action.
Whaling has become a major challenge for businesses. While financial institutions and payment services are highly targeted, online services and e-commerce companies get credit for the most whaling attacks. These attacks can include ghost fraud, fake claims from deceased persons, new account fraud from stolen identities, and synthetic fraud based on fake, real, and stolen information.
What Whaling Attacks look like?
Whaling attacks can occur through emails, phone calls, voice or phone messaging, social media, and website spoofing. Another growing technique uses deep fake technology (AI) to create audio and video that impersonates a high-level executive.
Whaling attacks have the following characteristics:
- Contain personalized information, including the company logo, email address, and specific details.
- Communicate a sense of urgency.
- Reflect business language, company culture, and personal nuances.
- Are highly believable, even appearing authentic.
The goals of these attacks are to:
- Commit financial fraud through wire transfer or extortion.
- Gain control over an organization’s data, systems, and networks.
- Damage a high-profile person or their organization’s reputation.
- Launch a supply chain attack by gaining unauthorized access through cybersecurity gaps.
- Steal intellectual property or competitive secrets.
- Install malware such as ransomware, spyware, or a virus.
Attackers achieve success once a victim takes action, such as clicking a link in a highly believable email or message, that leads them to the payload.
How Whaling Phishing works?
As savvy researchers, cybercriminals leach onto publicly-available information about their target. For example, they might curate personal details from their social media profile, corporate profiles, webinars, or company news gathered online.
The attack vectors for whaling include:
- Emails: Are personalized to trick their targets into clicking malicious attachments or links.
- Phone: Might follow an email to reinforce the urgency of the phishing request.
- Pretexting: Can occur on social media platforms when an attacker poses as a prospective business partner, professional peer, or governmental authority.
- Baiting: Refers to luring a target to use an infected USB drive or other devices by leaving it at a location they frequent, such as a gym, coffee shop, or home.
Once attackers complete their research, they craft legitimate-looking, personalized messages that appear to come from a known associate using stolen credentials. They can include official company logos, industry jargon, or links to commonly used pages that lead to a fraudulent website.
The urgency of the messages plays on a victim’s intuitive, emotional way of thinking, particularly their need to impress upper-level managers or clients quickly and without question. For example, the message might ask the target to immediately reply with sensitive or confidential information, open an attachment, pay an invoice, or enter personal information on a fake website.
Cyber attackers will put in the work to craft highly personalized, authentic-looking messages because they reap the highest returns. Just remember never to pay them off if you’re ever caught in such an attack.
Consequences of Successful Whaling Attacks
Whaling attacks can be costly to the point of forcing companies out of business, as former Australian hedge fund Levitas Capital experienced in 2020. In this attack, a company co-founder unknowingly clicked a fake Zoom link in a meeting invitation. That single click opened the door for cyber attackers to install malware that infiltrated the co-founder’s email and sent $8.7 million in fake invoices straight to the attackers’ pockets.
As Levitas Capital found, the consequences of whaling can be devastating. They often include:
- Business disruption: Dealing with the aftermath of an attack shifts resources away from achieving business goals to instead prioritize breach notification, prevention of future attacks, and recovery of lost funds.
- Financial loss: Besides losing enormous amounts of money in a whaling attack, organizations face potential fines from industry regulators and lost profits from current and prospective customers.
- Data loss: Organizations can lose critical assets, including customer and employee personal data and sensitive company information.
- Reputational and brand damage: Organizational trust can be difficult to repair after a data breach. Previous customer loyalty is essential to repairing damage to the company’s reputation and brand, although this may take a long time.
8 Steps to Prevent Whaling Phishing Attacks
Preventing whaling attacks takes a concerted effort between employees, upper-level management, and the security team. Follow these tips for a comprehensive approach to protecting your organization.
1. Provide security awareness training
Build a security-awareness culture by providing continuous cyber-security awareness training at regular intervals right in your employees’ workflow. Choose a program that delivers customizable, short, and text-based content bites and measures success based on critical data points. Focus lessons on threats that pose the highest risk to your organization, such as phishing and whaling, to modify employee behavior to prevent such attacks.
2. Conduct regular whaling simulations for upper management
As part of your cyber-security awareness training, which should include phishing simulations, provide whaling-specific simulations for upper-level management. The more you conduct these simulations and correct their fast-fingered responses to email and other communications, the greater you’ll protect them and your company from a whaling attack.
3. Lock down email security
Implement anti-phishing software as part of your phishing and whaling defense system. Anti-phishing software flags emails from outside your organization, making it easier to identify fake emails. It protects employees by scanning emails for language, links, and attachments. If it determines an email is suspicious, it blocks users from accessing it.
4. Verify urgent emails
Establish a standard practice of having employees, particularly upper-level management, verify urgent requests. All it takes is a quick phone call, message, or visit to the sender’s office to confirm whether they indeed sent the request. Ensure C-suite employees get in the habit of asking specific questions of the supposed sender to confirm details that verify the authenticity of the request.
5. Promote safe social media practices
Social media platforms thrive on engagement based on what people post, making them a great place for cybercriminals to lurk and mine details about potential targets. Train upper-level management to use care when creating profiles and sharing information online. Have them hide personal information, such as birthdays and relationships, and limit profile access to only people they know. Coach them to avoid mentioning mergers and promotions that could be used as a whaling tactic against them.
6. Enforce data protection and data privacy protocols
Ensure employees follow safe data practices to protect sensitive data and personal identifiable information (PII). Review back-office systems regularly to assess their ability to protect your data and prevent a data breach. Also, require employees to follow standard protocols for entering, interacting with, and storing data. Several industry regulators require these standards, such as General Data Protection Regulation (GDPR) and SOC 2 compliance.
7. Keep current with software and hardware updates
Cybercriminals are constantly searching to gain unauthorized access to your organization. Ensure employees stay on top of software updates, which often contain added security protections. Also, regularly conduct penetration testing of your organization and environment to look for gaps in security. Make any hardware or software updates needed to mend those gaps.
8. Secure your digital assets
Prevent imposter, phishing, and whaling attacks before they happen by securing digital assets with a real-time detection and protection system. Our Proof of Source Authenticity (PoSA) solution uses a digital watermark to enable employees, customers, and partners to identify real content from fake content easily. The watermark contains a randomly generated code and animation and works across all touch points between brands and their customers, including emails, SMS messages, and websites. This reassurance gives employees and customers confidence in interacting with your digital assets and builds trust in engaging with your brand online.
Identify Real Content from the Fakes
Whaling attacks have made their mark on small businesses and some of the world’s biggest brands. The damage they cause is costly—even detrimental—to victims’ success.
To avoid these attacks, combine these eight must-dos with your existing cyber security practices and build employee confidence to respond to potential whaling phishing threats.
Meanwhile, boost employee and customer trust in the legitimacy of your organization’s digital assets with MEMCYCO. Place a digital watermark on your website and emails, shutting the doors to hackers looking to impersonate your brand through methods such as spoofing, cloning, or re-engineering. To learn more about how MEMCYCO ensures your organization’s authenticity, safeguards upper management and protects your brand, book a demo.