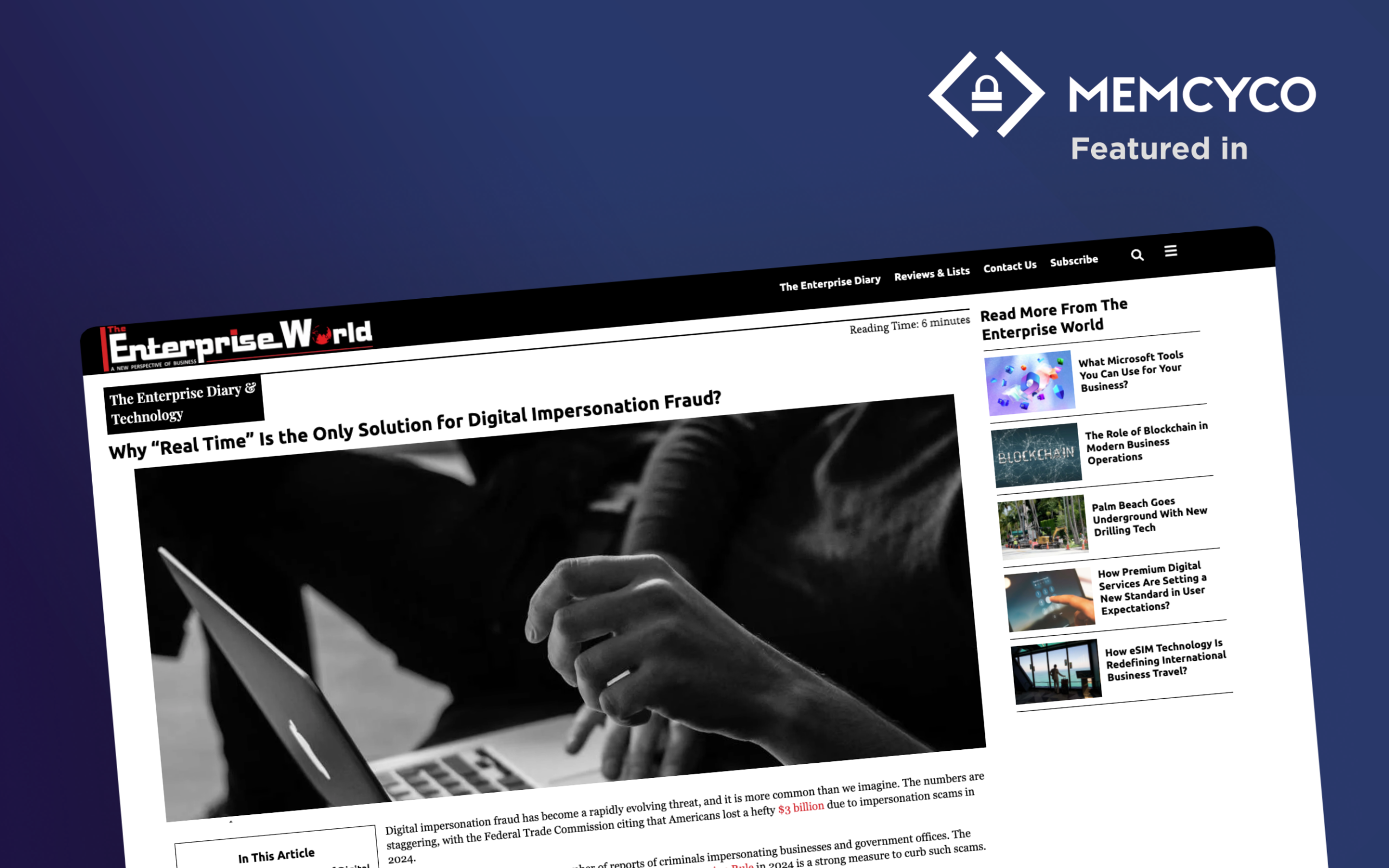
Account takeover (ATO) fraud poses a serious and personal threat, especially when it compromises something as critical as your bank account. Imagine the shock and helplessness of discovering you’re suddenly barred from accessing your own financial resources. This violation isn’t just about unauthorized transactions or financial losses; it’s a profound breach of your privacy. Often, these attacks on customers originate from website impersonation, highlighting the cunning methods attackers employ to bypass security measures.
When it comes to single sign-on (SSO) ATO incidents that target employees, the consequences can be significantly more serious. Besides your personal data, fraudsters who get a hold of your SSO login credentials could gain access to the personal data of others, plus business-wide systems and access settings, leading to ransomware attacks and devastatingly expensive breaches. How expensive? In 2023, the average breach caused by stolen credentials cost organizations $4.45 million USD, with an eleven-month recovery period.
Another concern is how common successful account takeover attacks are, whether it’s customer ATO based on website impersonation scams or employee ATO based on fake SSO login pages. Research indicates that 75% of ATO victims in 2023 had personal accounts breached, and 21% suffered a business account takeover.
Preventing and managing the scope and magnitude of ATO attacks earlier and more effectively is paramount —but first, you need to understand what account takeover fraud is and how it works.
What is account takeover fraud?
Account takeover fraud is a cybercrime technique that targets an organization’s customers or employees and entails malefactors taking control of online accounts that belong to individuals or businesses.
Traditionally, when fraudsters gain unauthorized access to a specific account, they first lock out the legitimate account user. Next, they either use the compromised account for malicious activities or sell the account credentials on the Dark Web to other cybercriminals.
From a cybercriminal’s perspective, the most valuable types of accounts for takeover fraud are:
- Business email accounts which are often used for Business Email Compromise (BEC) attacks, where fraudsters impersonate company executives or partners to trick employees into transferring money or sensitive information.
- Financial services, such as banking systems and online payment services, which are used to commit various financial frauds.
- Business accounts that grant access to sensitive information on various platforms or enable lateral movement within the target business systems, such as cloud service provider admin access credentials.
More and more organizations employ single sign-on for increased security and lower user friction with the authentication process. That’s partly why SSO has become a prominent target for fraudsters; a successful SSO hack can potentially grant fraudsters access to more than one application or service with a single set of compromised credentials.
What’s the difference between customer ATO and employee ATO attacks?
Both customer ATO and employee ATO attacks aim for unauthorized access to accounts, but they target different victims and have slightly different goals. Here’s a breakdown:
Target
- Customer ATO: Targets customer accounts on a company’s website or application. These accounts might contain financial information, purchase history, loyalty points, or personal details.
- Employee ATO: Targets employee accounts within a company’s network. These accounts could provide access to sensitive data and internal systems or even be used to launch ransomware attacks.
Goals
- Customer ATO: The attacker’s main goal is usually financial gain. They can steal credit card information, make fraudulent purchases, or sell access to the compromised account on the dark web.
- Employee ATO: Here, the attacker might aim for financial gain too, but they might also be after confidential information, intellectual property, or using the employee account to launch a wider ransomware attack within the company.
Similarities
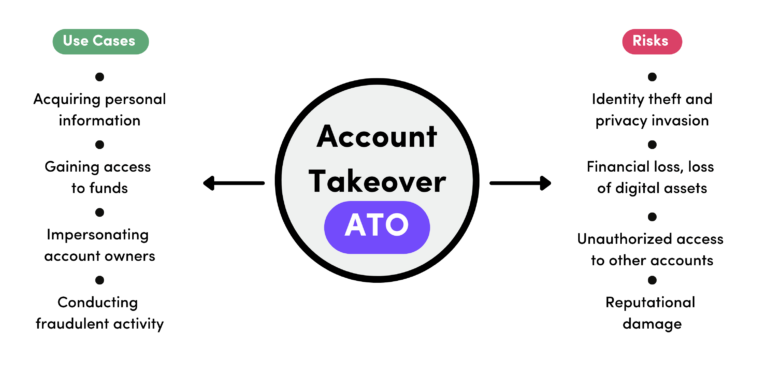
Both attack methods rely on similar techniques along a timeline to gain access to accounts. This can include:
- Website Impersonation: Customer ATO attacks often begin through spoofed websites of commonly used accounts, such as eCommerce brands or banks. Employee ATO attacks usually rely on fake SSO sign-on page impersonation.
- Phishing: Fraudulent emails or text messages that trick users into clicking malicious links or downloading attachments that steal their login credentials are used to spread the scam.
- Malware: Along with ATO, another possible consequence is infecting devices with info stealer malware that can steal login information.
- Brute Force Attacks: Harvested credentials are used in brute force attacks such as credential stuffing, using stolen usernames and passwords from data breaches to try logging into multiple accounts, and password spraying based on compromised personally identifiable information (PII) found for sale on the Dark Web.
How Account Takeover Fraud Works in 3 Steps: Customers vs. Employees
Account takeover fraud (ATO) unfolds in three key stages, with some variations depending on whether the target is a customer or an employee. Understanding these differences is crucial for effective prevention.
1. Credential Compromise
This initial stage involves obtaining the victim’s login credentials.
Customers
Hackers create fake websites that mimic legitimate login pages, such as bank portals or social media platforms. Unsuspecting users entering their credentials unknowingly surrender them to the attacker.
The hackers may also gain account credentials by using phishing emails with fake site links, malware on compromised websites, or leveraging data breaches where customer credentials are exposed.
Employees
Attackers create fraudulent login pages impersonating an organization’s single sign-on (SSO) portal. When employees attempt to log in, they unwittingly surrender their credentials to the attacker.
2. Access Validation
Once credentials are in hand, the attacker attempts to validate their access and gain full account control.
In some cases, account access requires a second step, during which a code is sent to the user for extra validation (MFA). However, social engineering tactics can be used to manipulate the customer or employee into divulging that code. Hackers might also exploit weaknesses in MFA systems themselves.
To ensure the account cannot be easily retrieved by its rightful owners, the fraudster will change the password and other account information to maintain control while doing their best to avoid detection.
Customers
In customer ATO attacks, SIM swapping may be used to intercept SMS-based MFA codes, granting access even if MFA is enabled.
Employees
In employee ATO attacks, there’s another phase of access validation: figuring out what type of access the malefactors now possess. View-only access to indecipherable reports to some obscure system is of little value to cyber crooks. However, there’s significant value in administrator access to cloud infrastructure or the ability to transfer funds to offshore accounts. Both can be used to perform various illegal actions, such as installing ransomware, as part of the next step.
3. Account Exploitation
With full account control, the attacker’s true motives come into play.
Customers
In customer ATO, financial gain is a major goal, leading to stolen funds or fraudulent transactions. Hackers might also use compromised accounts to spread malware or sell stolen customer data such as credit card details or other PII on the dark web.
Employees
For employee ATO, accounts are most often exploited for:
- Internal financial fraud: Hackers can manipulate financial records or divert funds for personal gain.
- Deploying malware within the network: By gaining access through an employee account, attackers can introduce malware that compromises sensitive data or disrupts operations.
- Stealing sensitive company data: With employee access, attackers can steal valuable information like trade secrets, customer data, or confidential documents, which can then be sold on the dark web.
As you can see, preventing ATO fraud is critical to targeted organizations and individuals. Here’s how to do it in the case of employee fraud.
4 Essential Steps to Prevent Employee Account Takeover Fraud
1. Secure and Monitor Your SSO Login Pages
The login page is the first line of defense against ATO attempts. Implement industry-standard web application security practices to shield it from vulnerabilities like cross-site scripting and brute-force attacks.
Additionally, ongoing monitoring of your login page is essential. By analyzing data and identifying potential attack patterns, you can proactively strengthen defenses before attackers exploit weaknesses or attempt to spoof your SSO login page.
2. Enforce Strong Authentication
Two key measures bolster authentication security: strong passwords and multi-factor authentication (MFA).
Often, accounts get taken over because of weak passwords and lousy password hygiene. To remedy this, enforce strict password policies that mandate complex passwords and regular changes.
MFA creates additional security by requiring a supplemental verification step beyond just the password. However, not all MFA solutions are foolproof. For instance, one-time passwords (OTP) delivered over mobile text messages or emails can be intercepted. MFA can also be bypassed using other techniques, such as social engineering (as described above) or man-in-the-middle (MitM) attacks.
Consider using physical security keys, mobile authentication apps, or biometrics to increase MFA security.
3. Detect Anomalous Behavior by User Accounts
Bots and tools used by cybercriminals behave differently from humans when they access SSO login pages. Monitoring user account behavior over time can help create a digital fingerprint for normal employee account behavior. This template enables identity threat detection and response (ITDR) systems to detect anomalous behavior indicative of a malefactor prodding your defenses.
With the right tools in hand, you should be able to correlate unusual login times and locations, multiple login attempts, and login attempts from unfamiliar devices to an ongoing ATO attack on one or more of your SSO users.
4. Inform and Train Your Employees
Training your employees to notice and avoid common account takeover fraud traps is crucial since cybercriminals are constantly getting more sophisticated in their tactics. Now, they’re employing generative AI, deep fakes, and advanced technologies to steal the precious keys to your digital kingdom—the SSO credentials of highly privileged accounts in your organization.
Getting up-to-date cybersecurity awareness training for all your staff builds a security culture that acts as a human firewall that’s always on the lookout for suspicious access attempts, the telltale signs of spoofed websites, shady social engineering scams, or other signs of malicious activity in your organization’s digital environment
Protect Against Impersonation Fraud with Memcyco
End-to-end account takeover fraud detection and prevention require an identity protection strategy that considers every link’s impact in the authentication security chain, whether you’re protecting your customers, employees, or both. By taking the four steps described above, you’re well on your way to safeguarding your organization against the perils of employee ATO fraud.
And what about customer ATO emanating from fake sites? To protect your company’s website against impersonation attacks that can end in ATO fraud—or worse—Memcyco has developed an innovative solution that offers a ‘nano defender’ sensor implanted into your company’s authentic website that provides real-time detection of fake websites.
With full protection for your business and its customers during the ‘window of exposure’ (the time between when a spoofed site is up until it’s taken down and beyond), maximum attack visibility, and unique mitigation techniques, Memcyco protects your website against impersonation like no other solution on the market. Contact Memcyco to learn more.