Have you ever wanted to capture a moment in time? On the internet, website mirroring does just that. Like a snapshot, it creates an exact copy of a website. But while mirroring can be useful for archiving and backup purposes, it can be a powerful tool in the wrong hands.
Website mirroring (also known as website spoofing, scraping or cloning) can provide attackers with access to sensitive information or become a means to create fake versions of websites used to trick users into providing personal data and bypass security measures. Today, we explore the benefits and potential pitfalls of website mirroring.
8 Things You Need to Know About Website Mirroring
Before you decide where and when to implement website mirroring into your workflow, keep these key points in mind:
1. How It Works
Website mirroring is typically achieved by using specialized software or tools that can download the entire contents of a website, including HTML, CSS, JavaScript, images, videos, and other media files.
Some tools used for website mirroring include:
- Wget: A free and open-source command-line utility for downloading files from the web. Wget can be used to download entire websites or specific portions of websites by specifying the site’s URL or the pages to be downloaded.
- HTTrack: A free and open-source website-copying tool allowing users to create a local copy of a website by downloading its contents. HTTrack can be configured to download specific file types, exclude certain URLs, and limit the download speed to prevent server overload.
- Cloud Services: Tools such as Amazon Web Services (AWS) S3 bucket or Google Cloud Storage allow users to store a copy of their website in the cloud for backup and recovery.
2. What are the Impersonation Risks?
One of the main risks associated with website mirroring is brand impersonation. Website mirroring can give attackers unauthorized access to sensitive information such as usernames, passwords, and other user data. Malicious actors can use this information to create fake versions of a website or web application to deceive users: Believing they are interacting with an authentic brand, trusting customers might navigate the fake copy of a brand’s website and provide personal information or financial data. Organizations often don’t know the attack is happening until they hear from their customer—and even then, they have no insights into how far reaching the damage is, or to what extent their organization has been affected.
This can be prevented by implementing security controls during the critical window of exposure, providing real-time protection to organizations and their customers. It is essential to be on top of access controls, authentication mechanisms, and encryption to prevent unauthorized access to the organization’s website.
A more proactive way for companies to protect customers and online shoppers is Memcyco’s out-of-the-box solution is based on an agentless Proof of Source Authenticity (PoSA™) technology. It enables automatic Zero Day protection and real-time detection, identifying the attacks at the point of impact. It takes it a step further and allows the organization and customer to receive instant Red Alerts, providing the organization with real-time insights into the precise scope of damage to prevent major financial loss and assure data privacy.
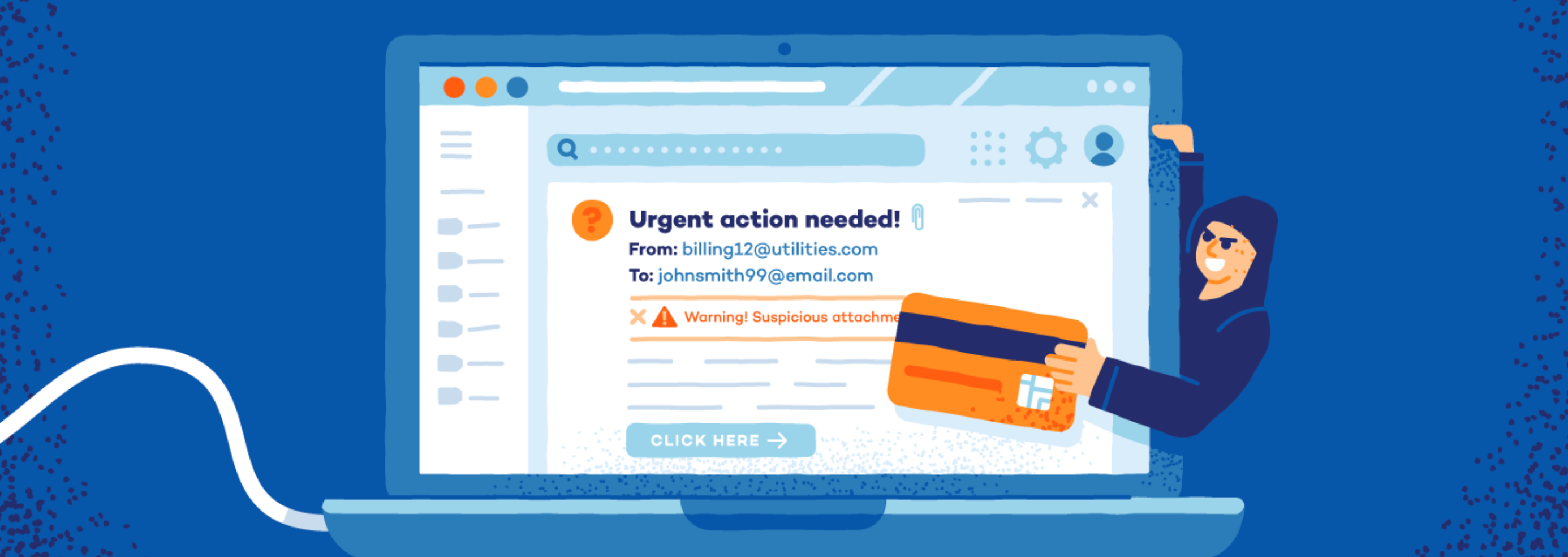
3. Look Out for Phishing Attacks
Similarly, website mirroring can be used as a phishing attack technique, making it more challenging for individuals to distinguish between a fake and a legitimate website. Phishing attacks are the most common form of cybercrime and can cause significant harm to both your organization and your customers.
To prevent these attacks, CISOs should educate employees on identifying and reporting suspicious emails and websites, implement security controls such as multi-factor authentication and web filtering, and deploy anti-phishing tools.
Crucially, organizations should also look beyond the corporate perimeter by aiming to protect their customers from phishing attacks impersonating their brands. Spreading awareness is not enough and can sometimes make matters worse by creating “Phishing Fear Syndrome.” Users might not want to interact with your brand at all when they can’t tell the difference between your real website and one made by hackers to take advantage of their trust.
It’s imperative to empower your end users by proactively protecting their digital assets and transactions at all times.
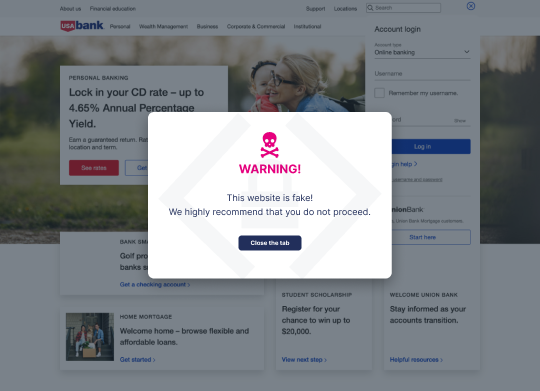
4. Be Aware of Other Security Risks
You may have covered your bases when it comes to phishing, but there are other attack vectors hackers can use with website mirroring, such as bypassing security measures such as firewalls or content filters by creating a copy of the site on a different domain or IP address. This can be used to launch attacks such as cross-site scripting (XSS), SQL injection, and other web application vulnerabilities.
To mitigate these risks associated with website mirroring, you must implement security measures such as web application firewalls (WAFs), two-factor authentication and other IAM policies, and encryption to protect sensitive data. Additionally, you should monitor web traffic to detect anomalies (such as unexpected spikes in traffic or changes in the IP address or website domain) to quickly identify and respond to any potential website mirroring attacks.
5. Understand that Website Mirroring Has a Wide Range of Benefits
Despite the risks associated with website mirroring, it can also be a useful tool. Website mirroring can be used to create a backup or recovery copy of a website or web application, making it easy to restore in the event of a disaster or cyberattack.
Beyond backing up your web pages, website mirroring can also be used to identify vulnerabilities and security weaknesses in a website or web application. Your security teams can use it to perform analysis and testing on a copy of the site without risking damage to the live site.
To make the most of the benefits of website mirroring while minimizing the risks, you’ll need to ensure that your organization has a policy in place for website mirroring, including guidelines for how and when website mirroring should be used and measures to prevent unauthorized mirroring of company websites or web applications.
6. Prepare for Compliance Challenges
Depending on the industry, there may be regulatory or legal requirements that govern website content and data. For example, in the healthcare industry, the Health Insurance Portability and Accountability Act (HIPAA) sets strict requirements for protecting patients’ health information. Websites that handle patient data must ensure that their security measures are HIPAA-compliant to avoid penalties and legal liability.
Similarly, in the financial industry, there are regulations such as the Payment Card Industry Data Security Standard (PCI-DSS), which requires organizations that handle credit card information to implement specific security controls to protect that data. Failure to comply with PCI-DSS can result in fines and loss of customers’ trust in the organization’s ability to handle their financial information securely.
CISOs should be aware of these requirements and ensure that their organization’s website mirroring activities comply with all applicable regulations and laws. Failure to do so can result in legal and financial penalties and irreparable reputational damage to the business.
7. Observe Your Website Performance
Website mirroring can significantly impact website performance, especially if the mirroring is done without appropriate resource management or throttling.
When a website is mirrored, it creates additional requests on the original website’s servers, leading to increased load and slower response times. This can ultimately result in a poor user experience for website visitors and potentially impacts website conversion rates.
If you’re running website mirroring activities, you’ll need to monitor your website’s performance so it remains fast and responsive. You can also use website mirroring to monitor changes to a website or web application over time, allowing organizations to track and analyze website activity and user behavior.
8. Monitor Online Activities
Monitoring and detection mechanisms can help you keep your website secure from website mirroring risks. These measures can aid in the identification of website mirroring activities.
Once such activities are detected, appropriate actions can be taken, such as blocking access to the website or reporting the activity to law enforcement authorities. Implementing monitoring and detection mechanisms can be made easier with specialized tools, while solutions such as Memcyco help reassure users they are browsing the correct site. By staying vigilant and employing these measures, you can effectively safeguard your website and users’ sensitive information from potential cyber threats.
Staying Ahead of the Risks
Website mirroring is a useful technique for creating backup copies of websites, but it poses significant risks when misused by cyber attackers. There’s no denying that impersonation is a major risk, and attackers can use mirroring to create fake versions of websites and steal sensitive information.
To enjoy the benefits of website mirroring while minimizing the risks, you can implement various security solutions, such as access controls, authentication mechanisms, and encryption. Additionally, leveraging automated tools such as Memcyco makes protecting organizations and their customers from fraud in fake websites easier while safeguarding your brand’s reputation.
Schedule a demo with Memcyco today to protect your website, customers, and brand from potential cyber threats.